Introduction
Like any network aware service, SQL database connections also need to be protected on the wire. If the database connection is unencrypted then it may be possible to perform a man in the middle attack that may allow an attacker to retrieve and tamper SQL queries and data. The risk is highest for databases that allow Internet located IP addresses to connect for access. A successful attack can lead to data compromise.
Enabling encryption for incoming connections on a CloudSQL database
Following are the steps using Google Cloud console:
-
Login to the Google Cloud console and navigate to Cloud SQL Instances (https://console.cloud.google.com/sql/instances).
-
Click on the instance name for which encrypted connections are to be enabled
-
In the left-side panel, select Connections then click on the Security tab
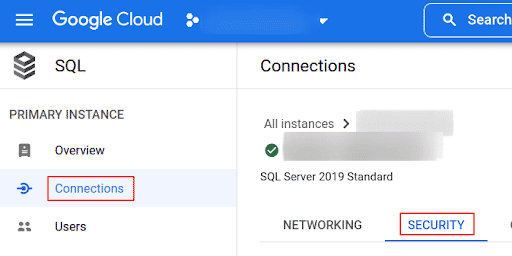
-
In the SSL connections section, click Allow only SSL connections
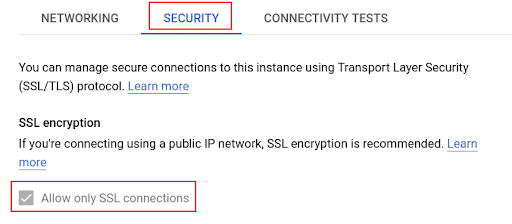
-
Under Manage server certificates click Create new certificate
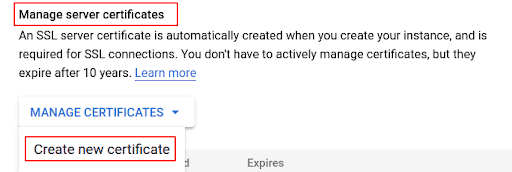
-
Under Manage client certificates click Create client certificate
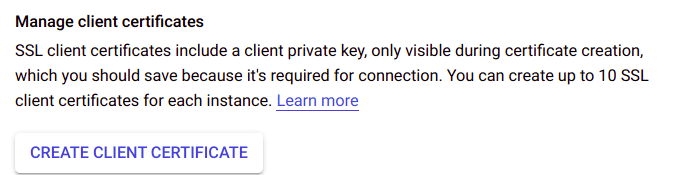
Following are the steps using gcloud on command line
- To enforce SSL encryption for an instance run the command:
gcloud sql instances patch <INSTANCE_NAME> --require-ssl
Note:
RESTART is required for type MySQL Generation 1 Instances (backendType: FIRST_GEN) to get this configuration in effect.”

Riyaz Walikar
Founder & Chief of R&D
Riyaz is the founder and Chief of R&D at Kloudle, where he hunts for cloud misconfigurations so developers don’t have to. With over 15 years of experience breaking into systems, he’s led offensive security at PwC and product security across APAC for Citrix. Riyaz created the Kubernetes security testing methodology at Appsecco, blending frameworks like MITRE ATT&CK, OWASP, and PTES. He’s passionate about teaching people how to hack—and how to stay secure.

Riyaz Walikar
Founder & Chief of R&D
Riyaz is the founder and Chief of R&D at Kloudle, where he hunts for cloud misconfigurations so developers don’t have to. With over 15 years of experience breaking into systems, he’s led offensive security at PwC and product security across APAC for Citrix. Riyaz created the Kubernetes security testing methodology at Appsecco, blending frameworks like MITRE ATT&CK, OWASP, and PTES. He’s passionate about teaching people how to hack—and how to stay secure.