Introduction
For validating the secure configuration of Amazon Web Services against CIS Amazon Web Services Foundations Benchmark Version 1.2.0 we run the Inspec profile.
Once the scan is done it will list the misconfigurations present in the AWS account and the check is from Amazon CIS benchmark.
aws-foundations-cis-baseline assessment
Scan with aws-foundations-cis-baseline takes time depending upon the number of services enabled in your AWS account. Once the scan is complete you can see the CIS benchmarks which are being followed and which are not. This can be then reviewed to prioritize as critical, high, medium, and low.
Audit results
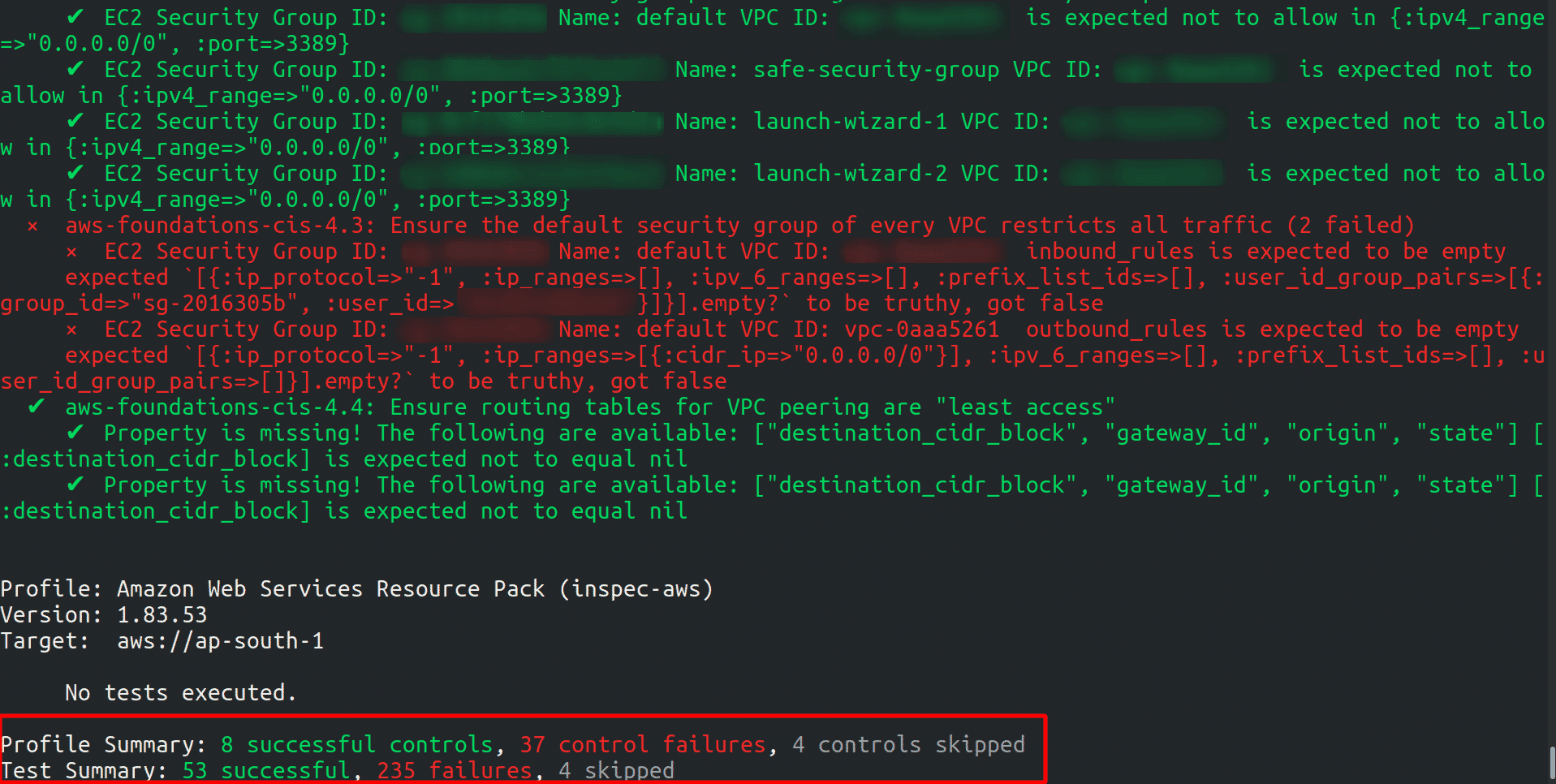
aws-foundations-cis-baseline produces results as list of CIS checks which are successful, failed or skipped. The checks when ran on the AWS account are categorized as below:
- Successful in green color
- Failed in Red color
- Skipped in White color
The check which are following the AWS CIS benchmark are in green and the once which are not following the CIS benchmark are in Red color.
In the end it will list the Profile summary and the Test Summary. The Profile lists the Controls successful, failed and skipped. The Test Summary lists the tests successful, failed and skipped.

Riyaz Walikar
Founder & Chief of R&D
Riyaz is the founder and Chief of R&D at Kloudle, where he hunts for cloud misconfigurations so developers don’t have to. With over 15 years of experience breaking into systems, he’s led offensive security at PwC and product security across APAC for Citrix. Riyaz created the Kubernetes security testing methodology at Appsecco, blending frameworks like MITRE ATT&CK, OWASP, and PTES. He’s passionate about teaching people how to hack—and how to stay secure.

Riyaz Walikar
Founder & Chief of R&D
Riyaz is the founder and Chief of R&D at Kloudle, where he hunts for cloud misconfigurations so developers don’t have to. With over 15 years of experience breaking into systems, he’s led offensive security at PwC and product security across APAC for Citrix. Riyaz created the Kubernetes security testing methodology at Appsecco, blending frameworks like MITRE ATT&CK, OWASP, and PTES. He’s passionate about teaching people how to hack—and how to stay secure.