Introduction
Unused IAM Roles are a security menace and must be periodically reviewed and purged from AWS account. The principle of least access and least privilege must be followed at all times. It is a security best practice to create and have only the roles (with strictly mapped privileges) that are required for the function of the AWS account.
IAM roles should not exist if they are not going to be used. This ensures that the attack surface for the AWS account is reduced. Based on the privileges of the role, an attacker may misuse it to perform privilege escalation via a compute instance and may even compromise the entire AWS account.
In this article we will take a look at how to delete an IAM Role using AWS CLI.
Delete an IAM Role via AWS CLI
Following are the steps to delete an IAM Role using AWS CLI:
-
List all the roles and select the role to be deleted, also note down its ARN
aws iam list-roles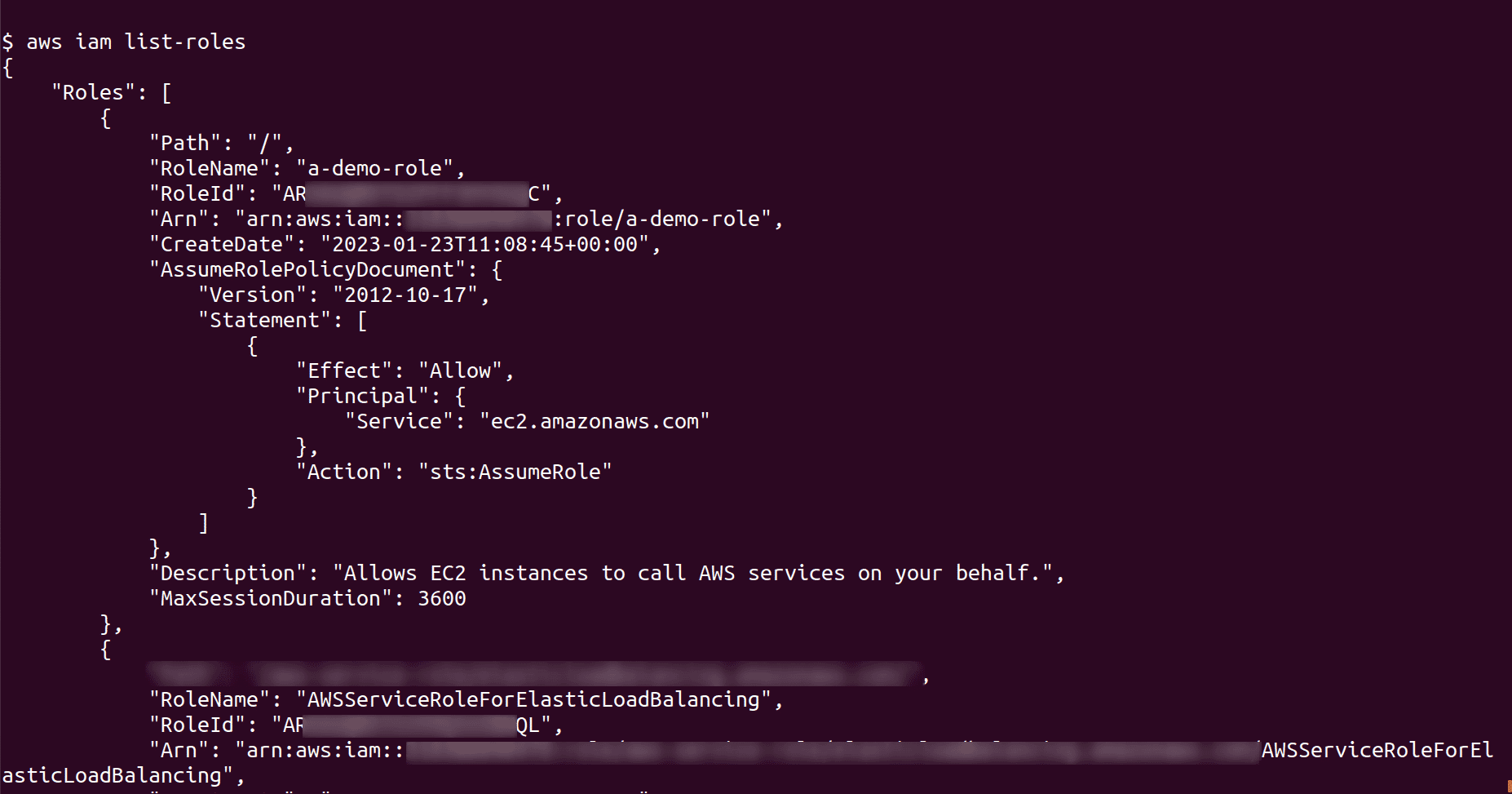
-
(Optional, else skip to step 4) To check role activity, generate service last accessed details and fetch the Job ID of IAM role
aws iam generate-service-last-accessed-details --arn <role_ARN>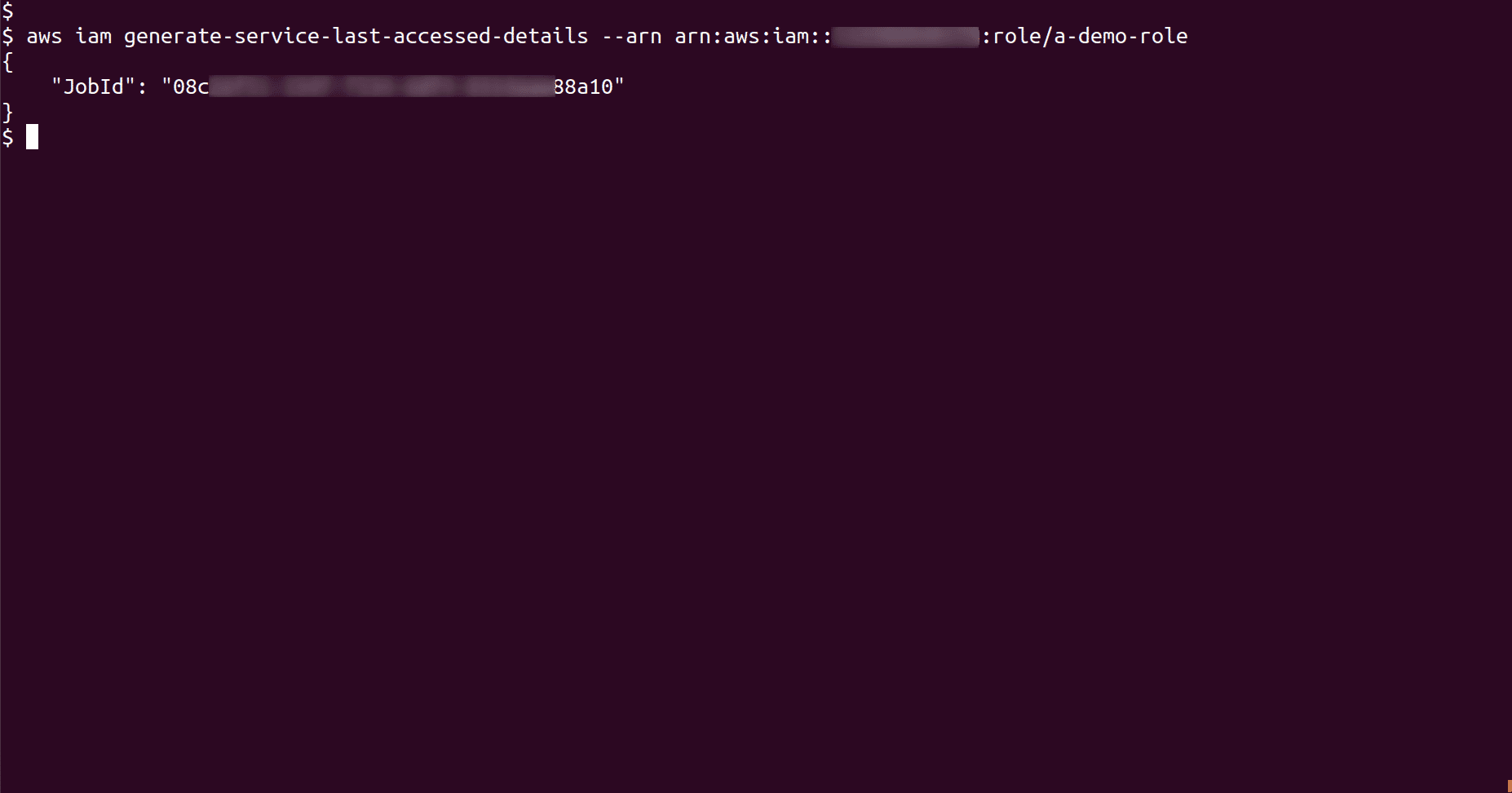
-
To fetch IAM service last accessed details, run following command and provide the Job ID generated in the previous step
aws iam get-service-last-accessed-details --job-id <job_id>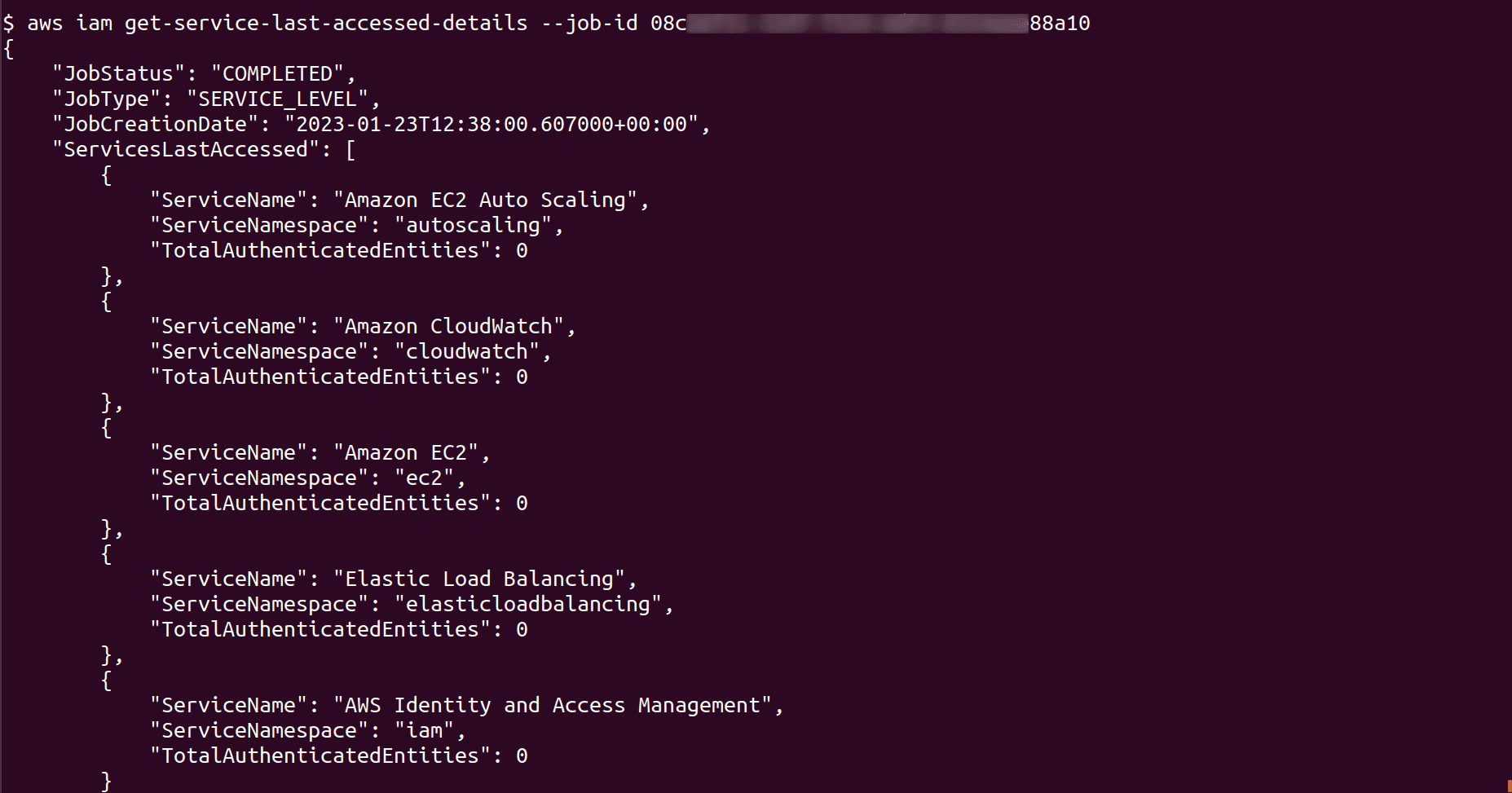
-
Before deleting the role check if any instance profiles and policies are attached to the role and remove them. To check if the role is attached to an instance profile, run following command
aws iam list-instance-profiles-for-role --role-name <Role_name>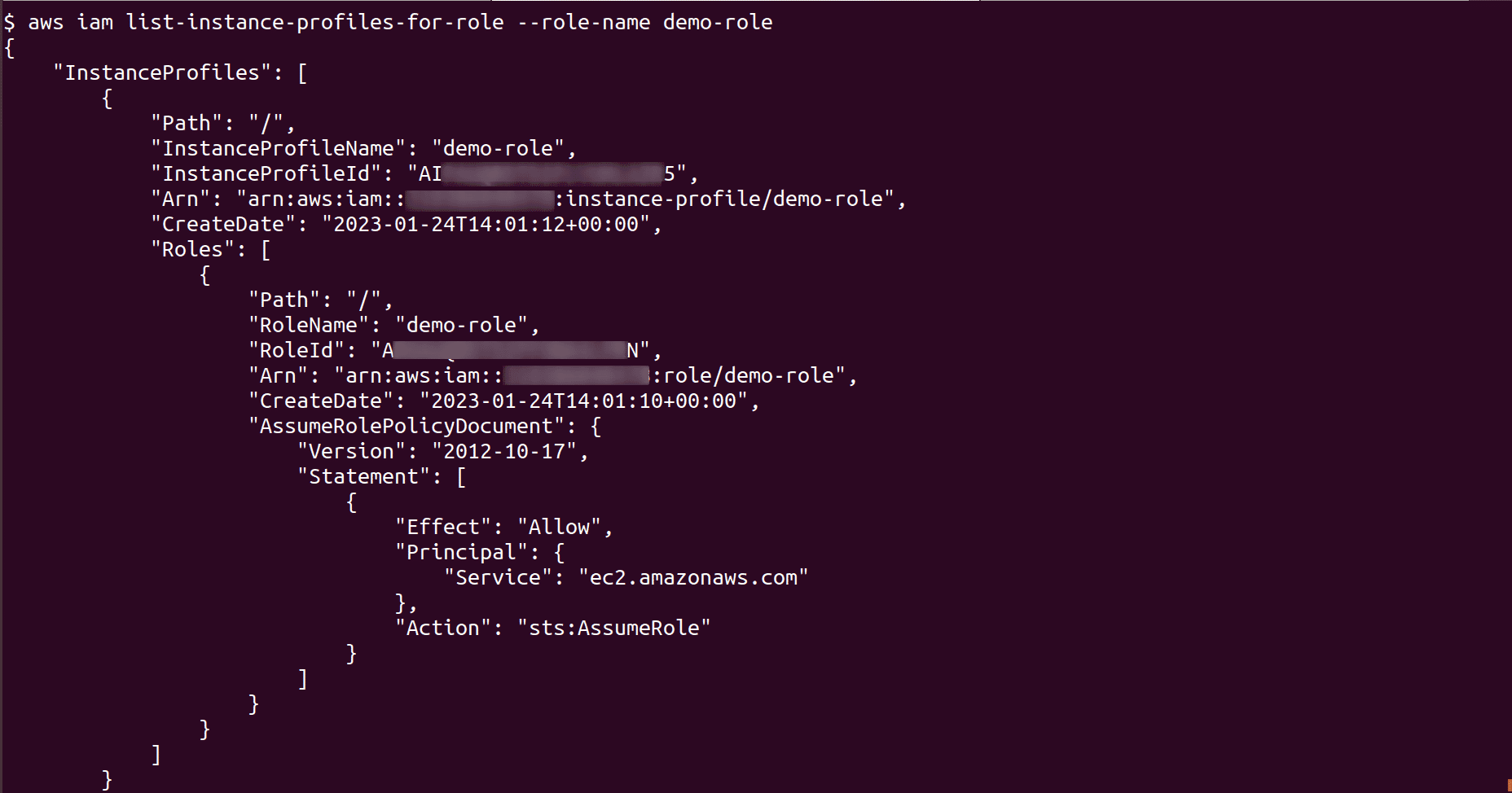
-
If an instance profile is attached to the role, remove it by running the following command
aws iam remove-role-from-instance-profile --instance-profile-name <Instance_profile_name> --role-name <Role_name>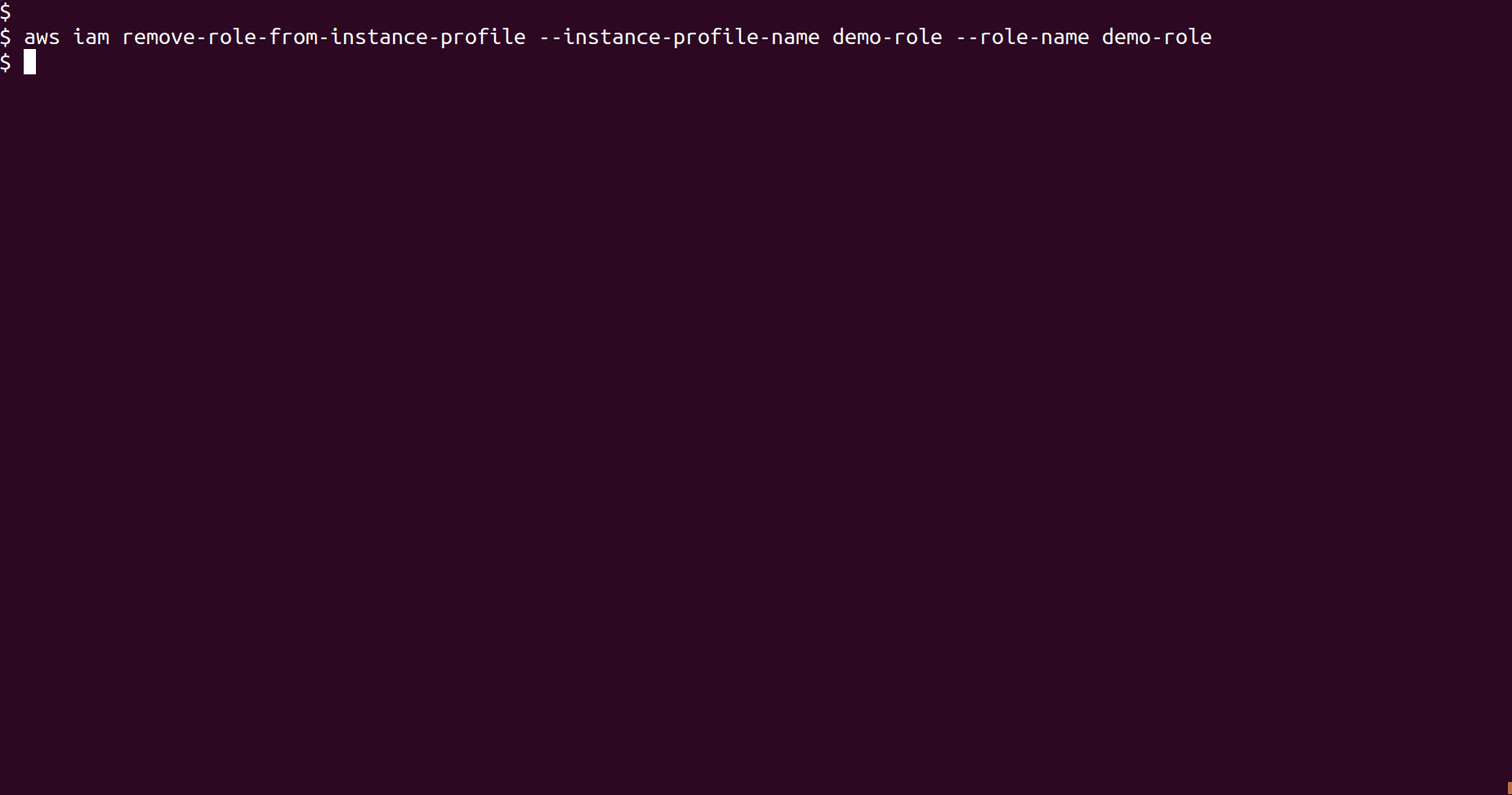
-
Before deleting the role check the policies attached to the role
aws iam list-attached-role-policies --role-name <Role_name>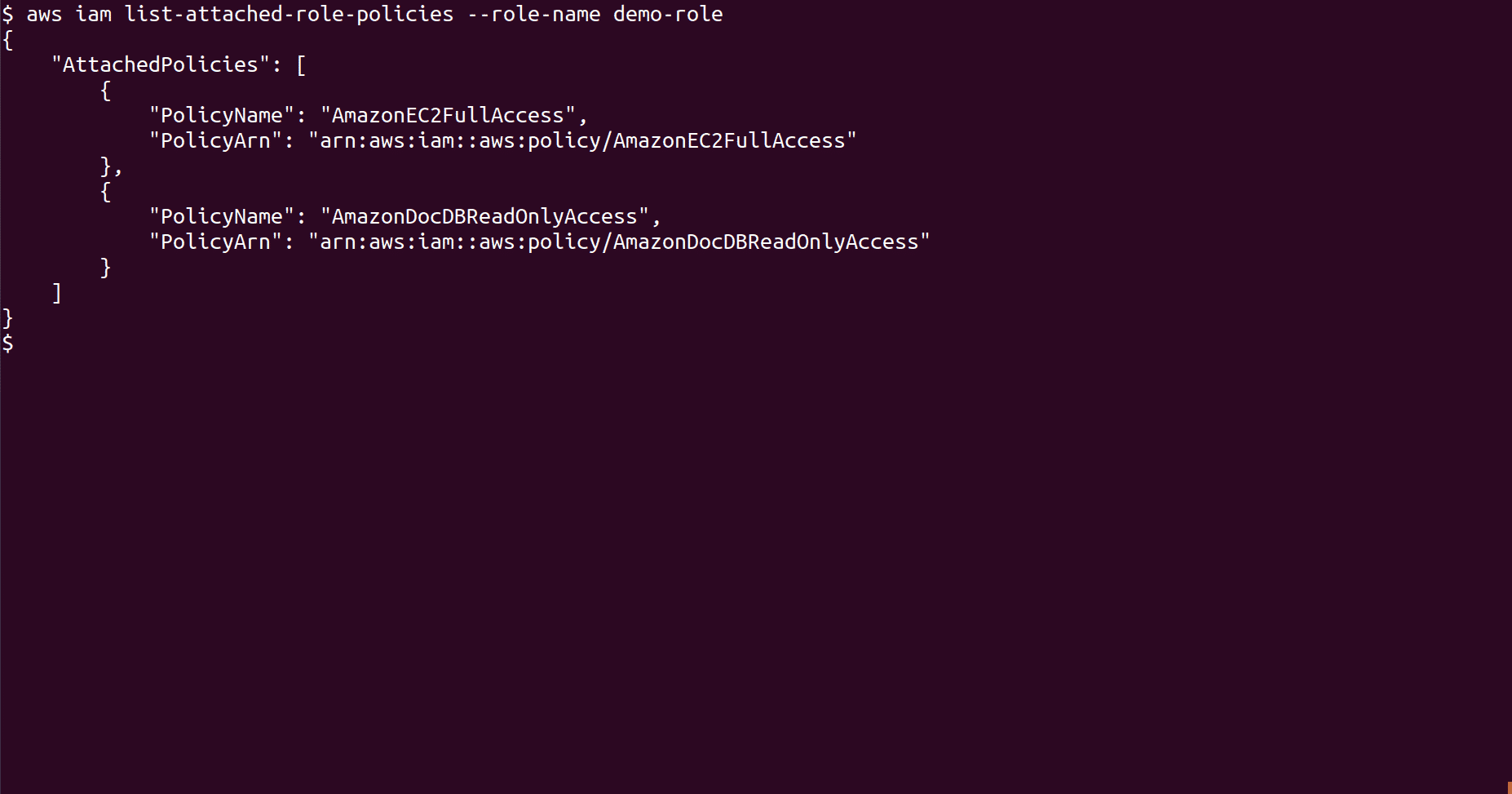
-
Detach the policies attached to the role by running the following command
aws iam detach-role-policy --role-name <Role_name> --policy-arn <Policy_ARN>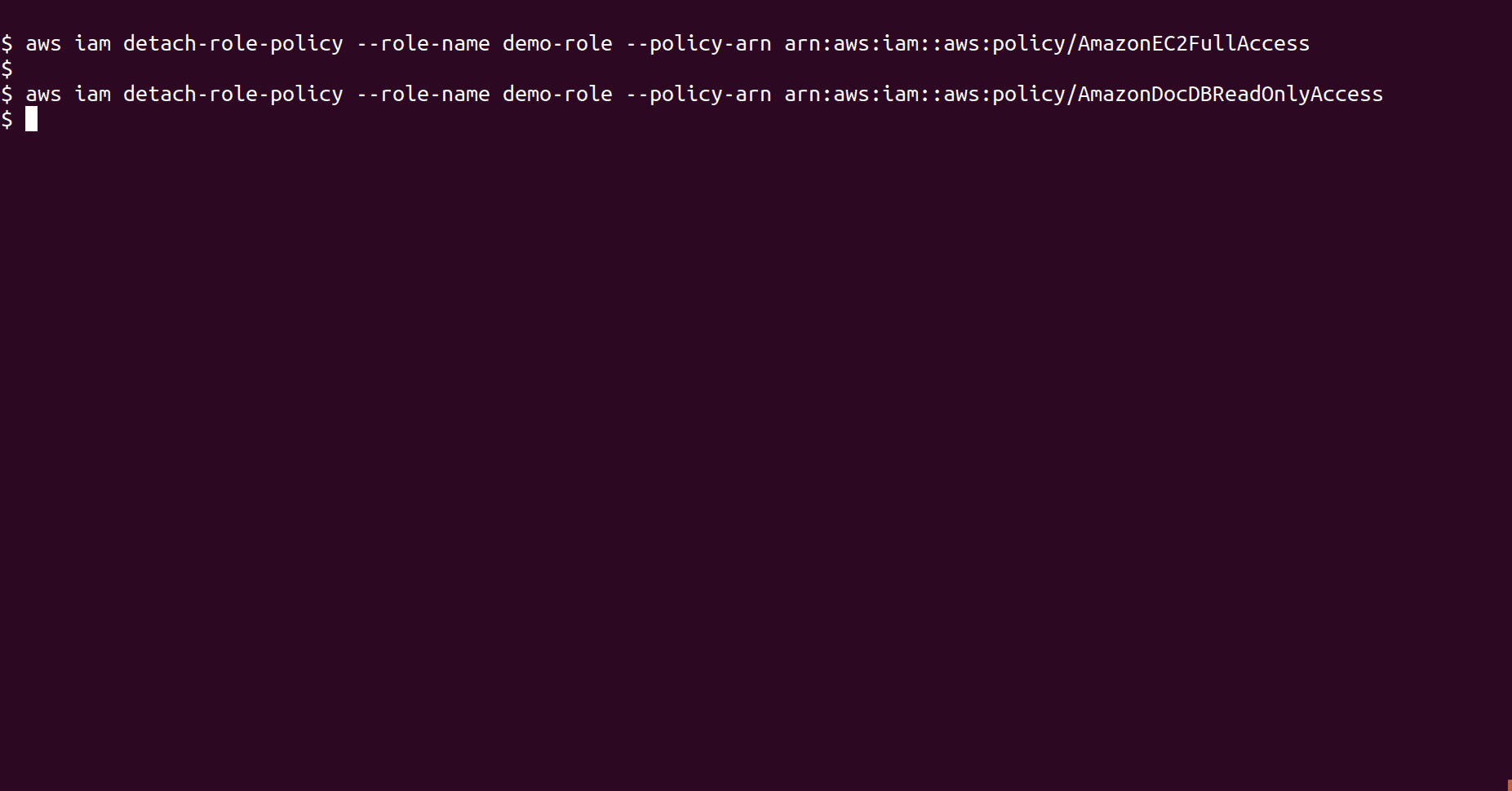
-
To delete the IAM role, run following command
aws iam delete-role --role-name <role_name>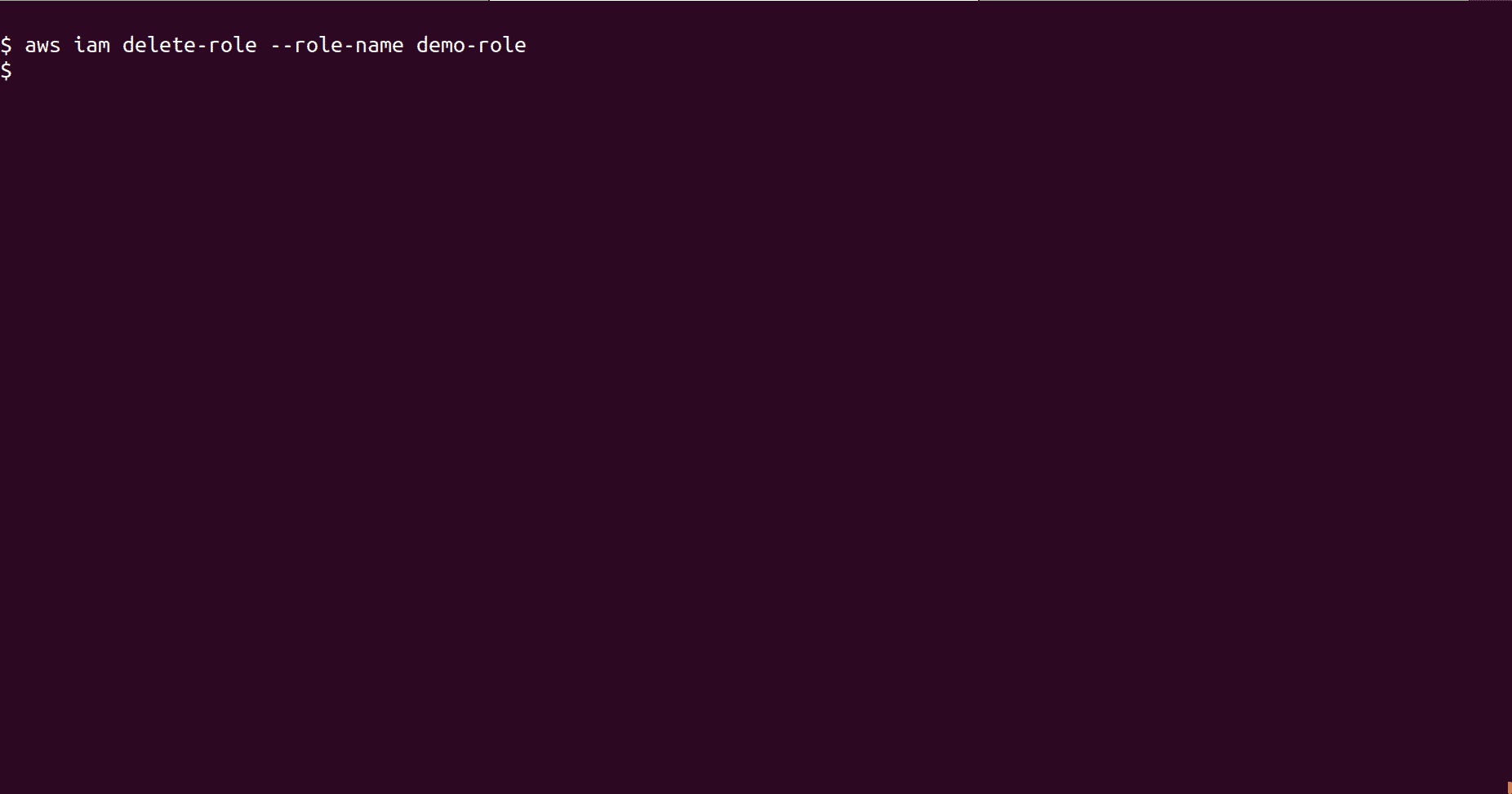

Riyaz Walikar
Founder & Chief of R&D
Riyaz is the founder and Chief of R&D at Kloudle, where he hunts for cloud misconfigurations so developers don’t have to. With over 15 years of experience breaking into systems, he’s led offensive security at PwC and product security across APAC for Citrix. Riyaz created the Kubernetes security testing methodology at Appsecco, blending frameworks like MITRE ATT&CK, OWASP, and PTES. He’s passionate about teaching people how to hack—and how to stay secure.

Riyaz Walikar
Founder & Chief of R&D
Riyaz is the founder and Chief of R&D at Kloudle, where he hunts for cloud misconfigurations so developers don’t have to. With over 15 years of experience breaking into systems, he’s led offensive security at PwC and product security across APAC for Citrix. Riyaz created the Kubernetes security testing methodology at Appsecco, blending frameworks like MITRE ATT&CK, OWASP, and PTES. He’s passionate about teaching people how to hack—and how to stay secure.