Introduction
The remote access option controls the execution of stored procedures from local or remote servers on which instances of SQL Server are running. This default value for this option is 1. This grants permission to run local stored procedures from remote servers or remote stored procedures from the local server. To prevent local stored procedures from being run from a remote server or remote stored procedures from being run on the local server, this must be disabled.
The remote access option controls the execution of local stored procedures on remote servers or remote stored procedures on local server. remote access functionality can be abused to launch a Denial-of-Service (DoS) attack on remote servers by off-loading query processing to a target, hence this should be disabled.
Steps to disable the “remote access” flag using Google Cloud UI
-
Login to GCP and navigate to the Cloud SQL Instances page in the Google Cloud Console by visiting https://console.cloud.google.com/sql/instances
-
Select the SQL Server for which you want to configure the database flag
-
Click on Edit button
-
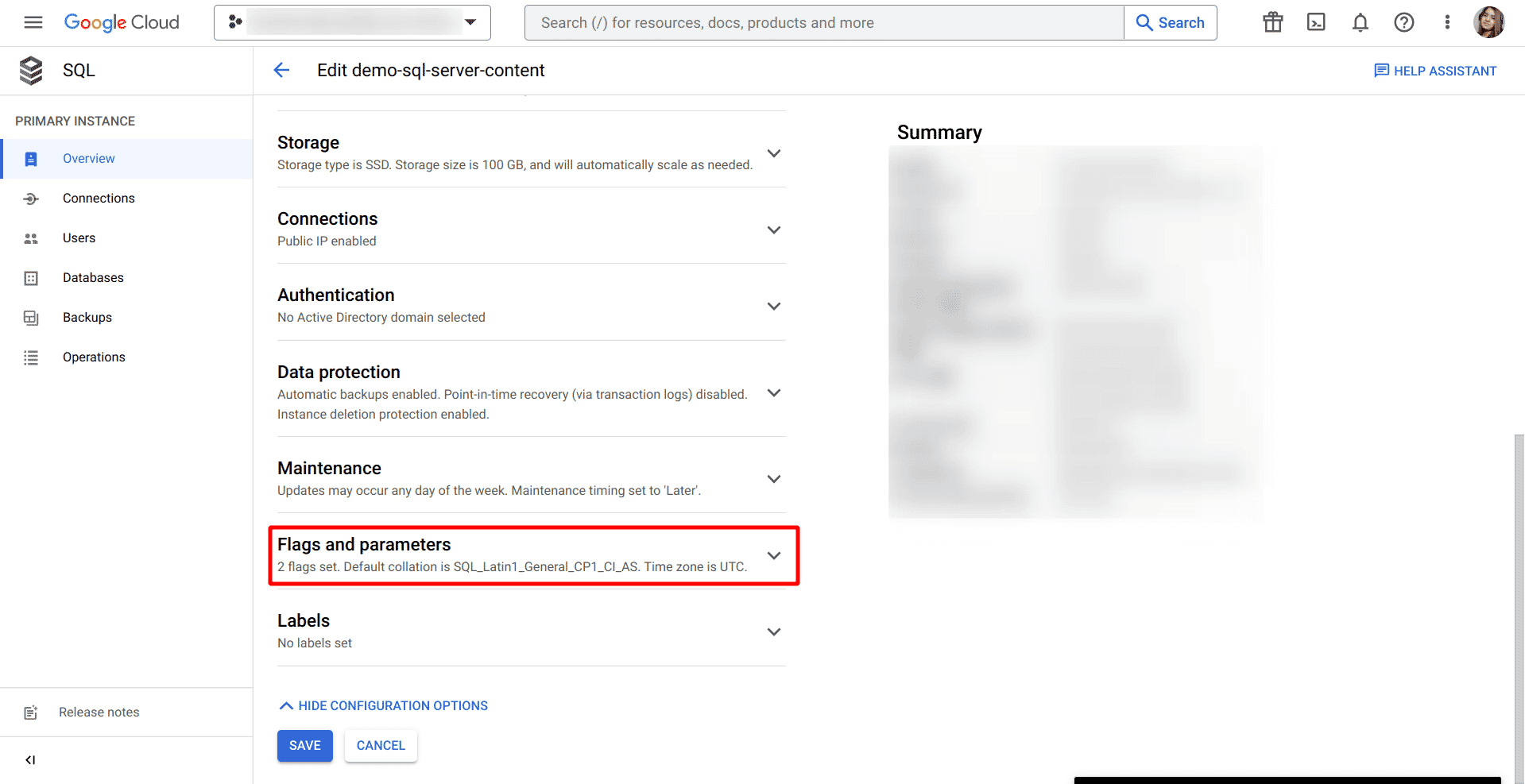
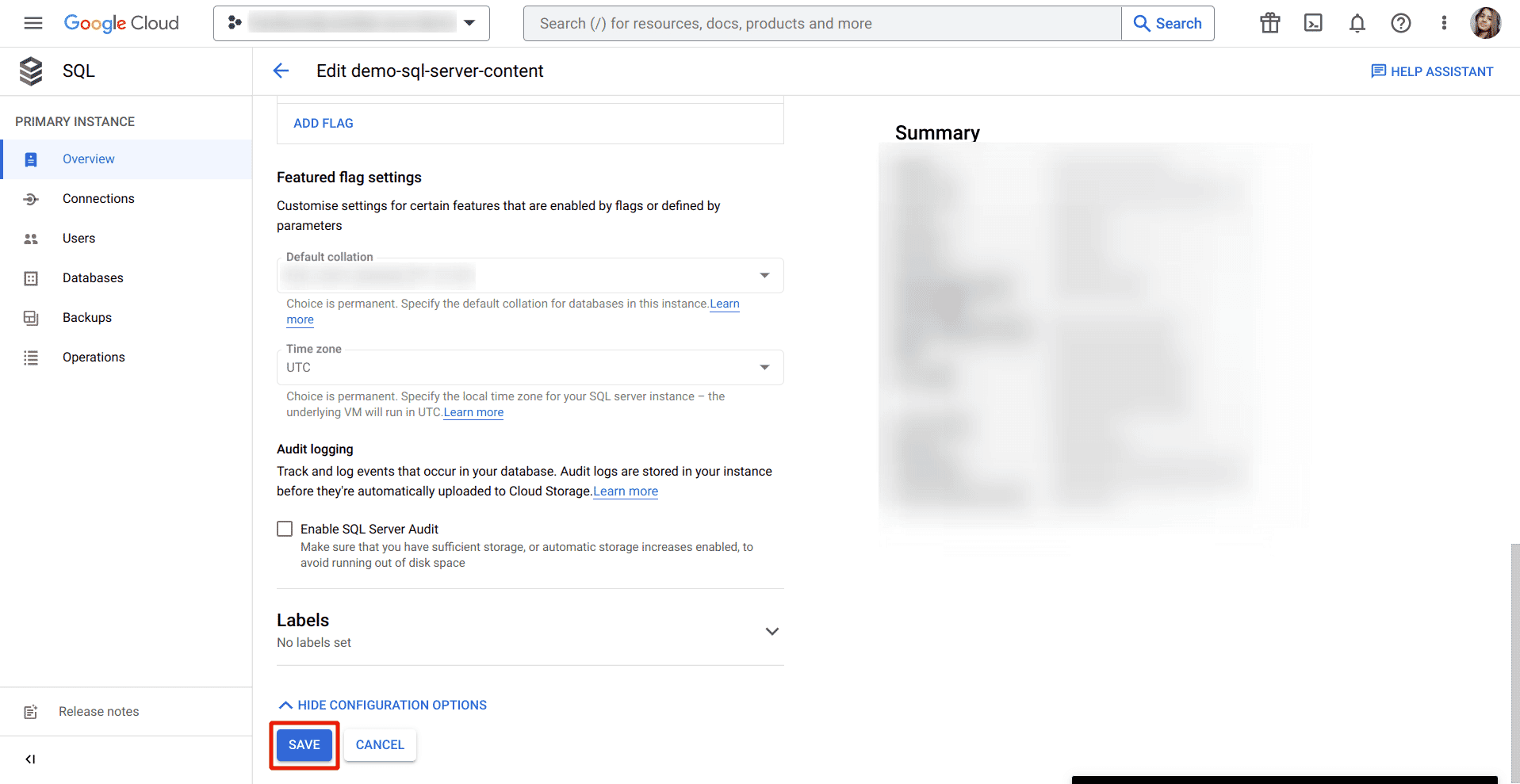
Scroll down to the Flags and parameters section
-
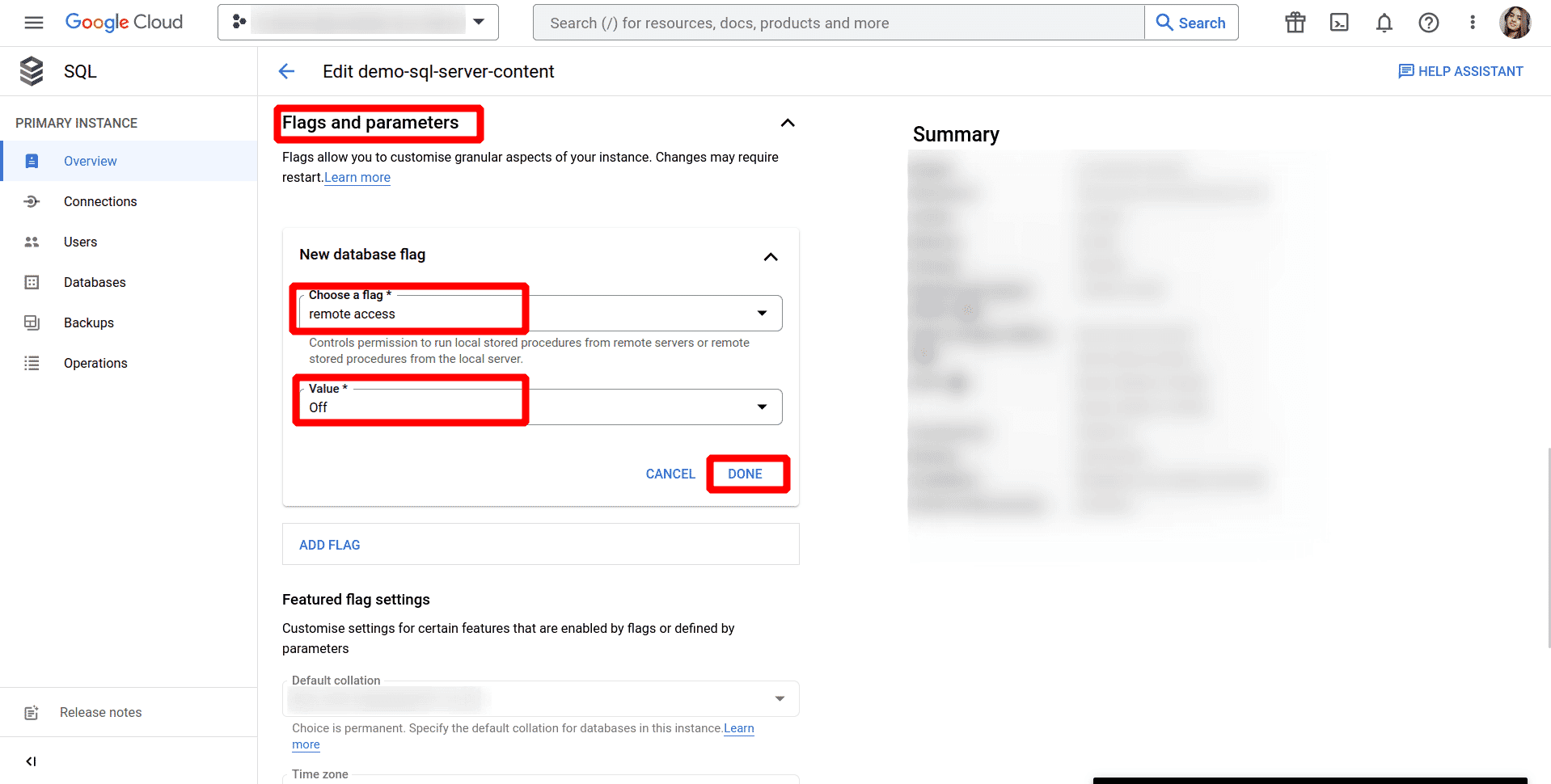
To set a flag that has not been set on the instance before, click Add Flag, choose the flag remote access from the drop-down menu, and set its value to off.
-
Click on Save button
-
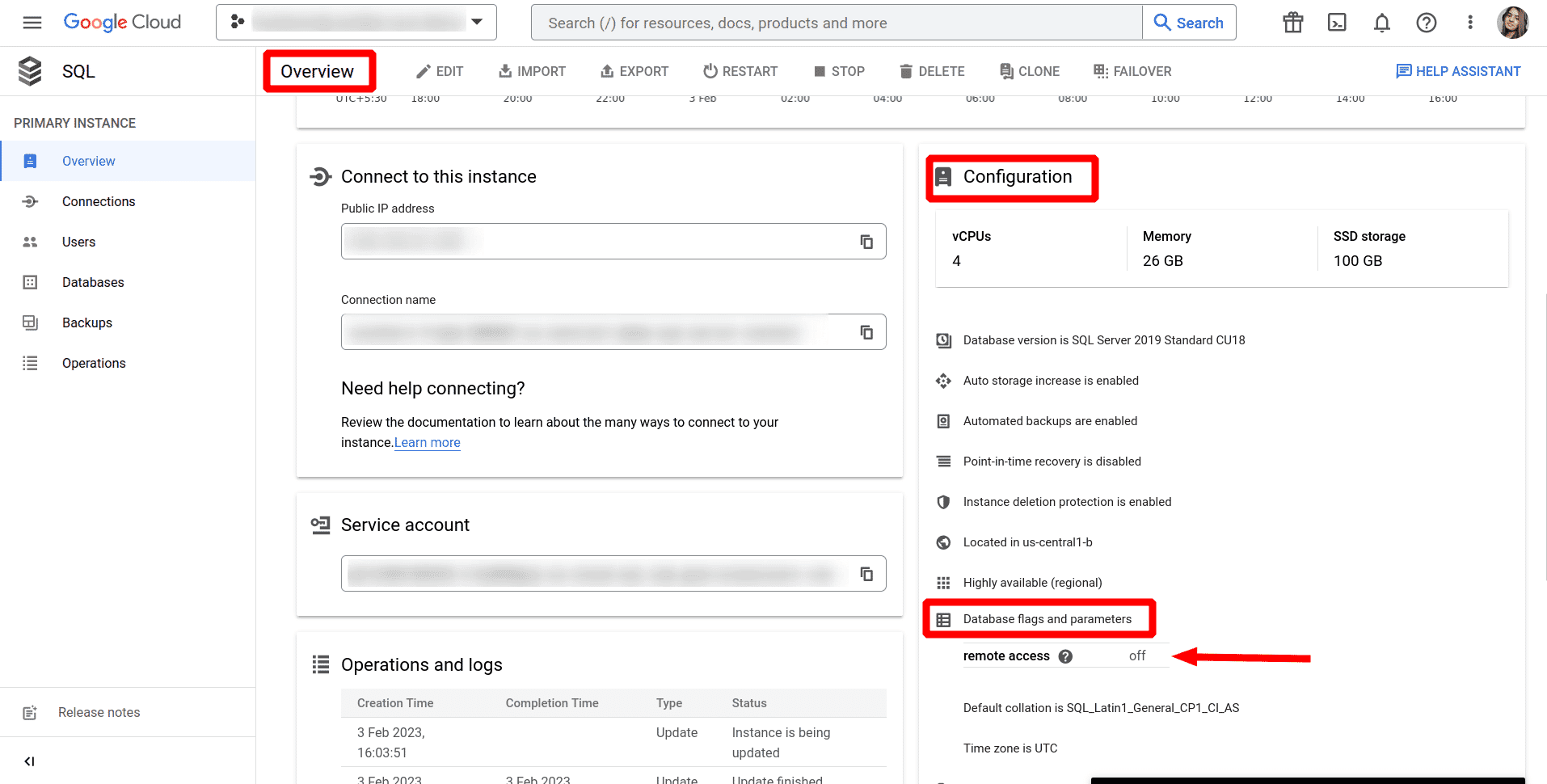
Confirm the changes under Database flags and parameters under Configuration section on the Overview page

Riyaz Walikar
Founder & Chief of R&D
Riyaz is the founder and Chief of R&D at Kloudle, where he hunts for cloud misconfigurations so developers don’t have to. With over 15 years of experience breaking into systems, he’s led offensive security at PwC and product security across APAC for Citrix. Riyaz created the Kubernetes security testing methodology at Appsecco, blending frameworks like MITRE ATT&CK, OWASP, and PTES. He’s passionate about teaching people how to hack—and how to stay secure.

Riyaz Walikar
Founder & Chief of R&D
Riyaz is the founder and Chief of R&D at Kloudle, where he hunts for cloud misconfigurations so developers don’t have to. With over 15 years of experience breaking into systems, he’s led offensive security at PwC and product security across APAC for Citrix. Riyaz created the Kubernetes security testing methodology at Appsecco, blending frameworks like MITRE ATT&CK, OWASP, and PTES. He’s passionate about teaching people how to hack—and how to stay secure.