Background
MongoDB is an open-source document-oriented database. It is used to store a larger amount of data and also allows you to work with that data. It is a cloud service with data distribution and mobility across AWS, Azure, and Google Cloud, built-in automation for resources and workload optimization. As it deals with important data of an organization or application there must be systematic evaluation of the company’s information system to confirm the security of the systems physical configuration and environment, software, information handling processes and user practices.
A security audit is a systematic evaluation of the security of a company’s information system by measuring how well it confirms an established set of criteria. Security audit is required since MongoDB Cloud is an integral part of the infrastructure and is essential to keep it secure.
Checklist For Mongo Cloud Audit
-
Verifying the number of clusters present in an organization.
A sharded cluster in MongoDB is a collection of datasets distributed across many shards (servers) in order to achieve horizontal scalability and better performance in read and write operations.
Steps:
-
On Home page Select
All Clusters -
The page will open with the list of
All Clusters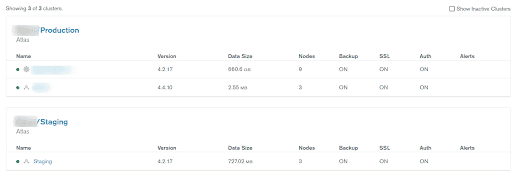
-
List all the users present in the individual projects.
Steps:
-
On Home page under the User’s name dropdown select
Organization’s -
The page with the list of organization’s will open.
-
Select the
Organizationyou want to list the Users. -
Page with the list of
Projectswill open. -
Select
usersand it will list all the users of the particular project along with Project Roles, Date of creation, Last Login details.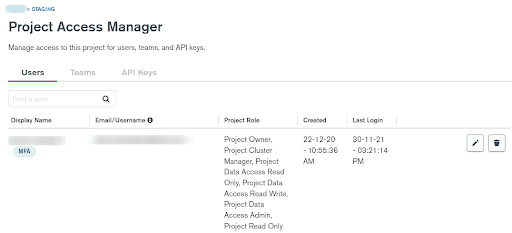
-
Database users and their permissions in Production projects. The permissions should be given according to the requirement of an individual user.
Steps:
-
From Home Page select
Atlas -
In the left pane under
SecurityselectDatabase Access -
All the users having database access are listed along with their
MongoDB Roles,Resources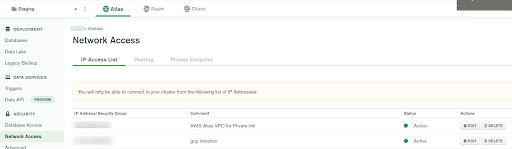
-
To check users having access to Network Access. This is the list of IPs/Security groups whitelisted for access to the clusters in the projects.
Steps:
-
From Home Page select
Atlas -
In the left pane under
SecurityselectNetwork Access -
A list will open with all the IP Address/ Security Group list along with
Status.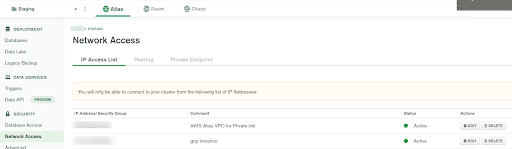
-
Check the Realm apps connected to Database
The apps are being used for taking actions based on different events in the database. The apps directly interact with the database and there are functions written to perform this activity which are executed based on triggers.
Steps:
-
From Home Page select
Realm -
The page with
Realm appswill open.
-
Third Party Services integration in Realm Apps
Steps:
- From Home Page select
Realm - On the left side pane select
3rd Party ServicesunderBuildSection. - The page with all the third party services will open along with
Service Name,Service Typeandlast modified date.
-
List the unused Third-Party services in Realm Apps
Steps:
-
From Home Page select
Realm -
On the left side pane select
3rd Party ServicesunderBuildSection. -
The Services with blank
Last Modifiedsection are unused.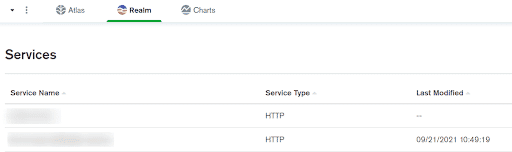
-
List the Users having access to the Realm app. Among all the users present for Realm application, the user which is currently in Enabled state will have the devices configured.The following should be verified,
- Team members who have access to these credentials
- Devices that have current session
- Team members who have access to the current devices
Steps:
-
From the Home Page select
Realm. -
On the left side pane select
App UsersunderData AccessSection. -
The list of Users will open.
-
To list the
devices, click on the user name dropdown and then click onDevicesdropdown.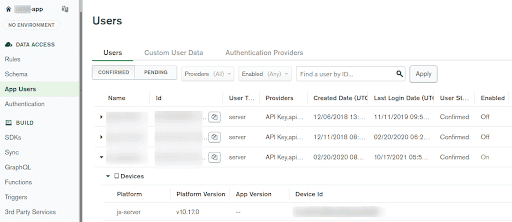
Conclusion
Mongo Cloud is a service which provides an organization or an application to manage the data. It is important to maintain the security of Mongo Cloud as the data which is stored is critical. Therefore it is required to verify any actions or the entities that performed certain actions and monitor the changes made to the Mongo Cloud on a regular basis through the security Audit.

Riyaz Walikar
Founder & Chief of R&D
Riyaz is the founder and Chief of R&D at Kloudle, where he hunts for cloud misconfigurations so developers don’t have to. With over 15 years of experience breaking into systems, he’s led offensive security at PwC and product security across APAC for Citrix. Riyaz created the Kubernetes security testing methodology at Appsecco, blending frameworks like MITRE ATT&CK, OWASP, and PTES. He’s passionate about teaching people how to hack—and how to stay secure.

Riyaz Walikar
Founder & Chief of R&D
Riyaz is the founder and Chief of R&D at Kloudle, where he hunts for cloud misconfigurations so developers don’t have to. With over 15 years of experience breaking into systems, he’s led offensive security at PwC and product security across APAC for Citrix. Riyaz created the Kubernetes security testing methodology at Appsecco, blending frameworks like MITRE ATT&CK, OWASP, and PTES. He’s passionate about teaching people how to hack—and how to stay secure.