Introduction
Elastic Load Balancers (ELBs) need to have logging enabled to ensure the logs are available for debugging, troubleshooting, and incident response activities. Access logs contain information such as the time the request was received, the client’s IP address, latencies, request paths, and server responses.
Each access log file is automatically encrypted using SSE-S3 before it is stored in your S3 bucket and decrypted when you access it. You do not need to take any action; the encryption and decryption is performed transparently. Each log file is encrypted with a unique key, which is itself encrypted with a master key that is regularly rotated.
Logging allows for an audit trail to be created in the event of an attack or malicious activity being detected. When logging is not enabled, this ability is absent which could allow potential attackers to hide within the traffic. This could allow attacks to go undetected, causing further loss in data and access.
Enable Access Logging for ELB using CLI
-
Create the S3 bucket that will store the ELB log files
aws s3api create-bucket --region <region_name> --bucket <bucket_name>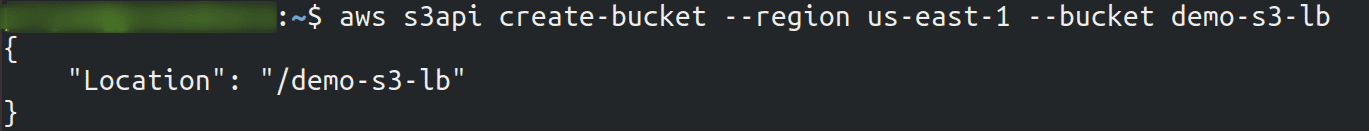
-
Attach the policy document that grants the ELB permission to write to the newly created bucket
aws s3api put-bucket-policy --bucket <bucket_name> --policy <policy_file_name>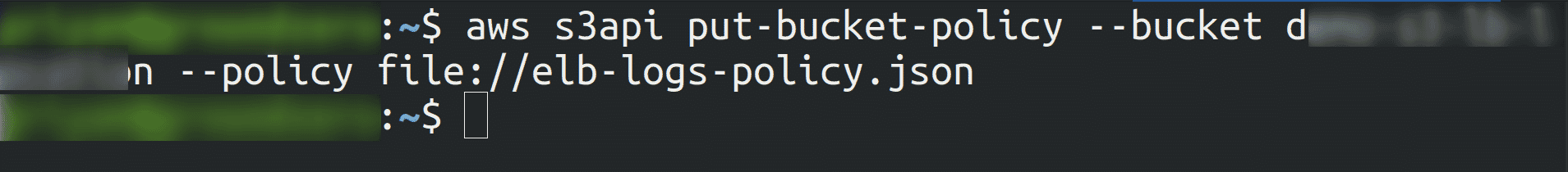
-
To enable access logging for the selected Elastic Load Balancer
aws elbv2 modify-load-balancer-attributes --load-balancer-arn <load_balancer_arn> --attributes Key=access_logs.s3.enabled,Value=true Key=access_logs.s3.bucket,Value=<bucket_name> Key=access_logs.s3.prefix,Value=<pefix> Key=idle_timeout.timeout_seconds,Value=60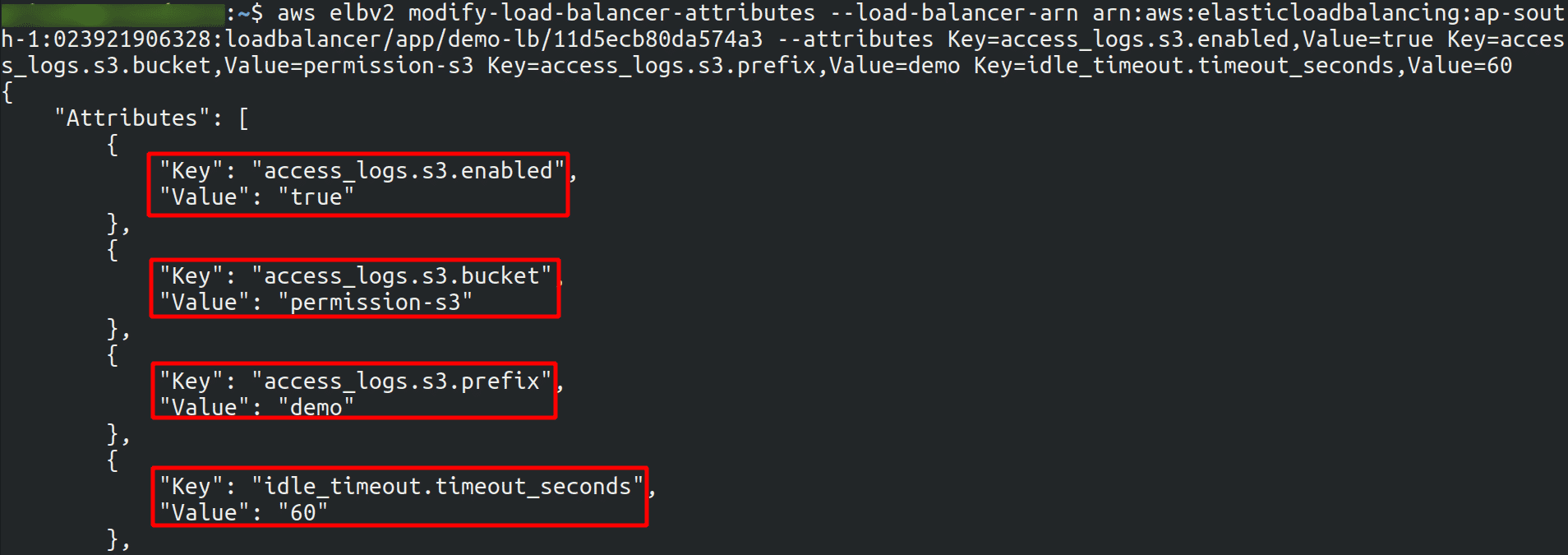

Riyaz Walikar
Founder & Chief of R&D
Riyaz is the founder and Chief of R&D at Kloudle, where he hunts for cloud misconfigurations so developers don’t have to. With over 15 years of experience breaking into systems, he’s led offensive security at PwC and product security across APAC for Citrix. Riyaz created the Kubernetes security testing methodology at Appsecco, blending frameworks like MITRE ATT&CK, OWASP, and PTES. He’s passionate about teaching people how to hack—and how to stay secure.

Riyaz Walikar
Founder & Chief of R&D
Riyaz is the founder and Chief of R&D at Kloudle, where he hunts for cloud misconfigurations so developers don’t have to. With over 15 years of experience breaking into systems, he’s led offensive security at PwC and product security across APAC for Citrix. Riyaz created the Kubernetes security testing methodology at Appsecco, blending frameworks like MITRE ATT&CK, OWASP, and PTES. He’s passionate about teaching people how to hack—and how to stay secure.