Introduction
In the event of a password theft or credential leakage, an attacker would be able to login into the AWS account of a user with only the password and gain access to the AWS account and services accessible to the user if MFA (multi-factor authentication) is disabled. The attacker could also run additional services or disrupt running operations based on their privileges.
AWS IAM provides MFA capabilities to its users. MFA provides an additional layer of security and must be enabled wherever possible. An attacker would not be able to login to an account, even if they had the password, as the account would require a multi factor authentication token to complete the login process.
In this article we will see how to enable MFA for an AWS IAM user.
Enable MFA for an IAM user
To enable MFA for a user in AWS IAM, make sure you have the permissions to do so. If not, contact the authorized team member who will enable and set up MFA for the given user.
Following are the steps to enable MFA for an AWS user:
-
Login to AWS management console and navigate to IAM service
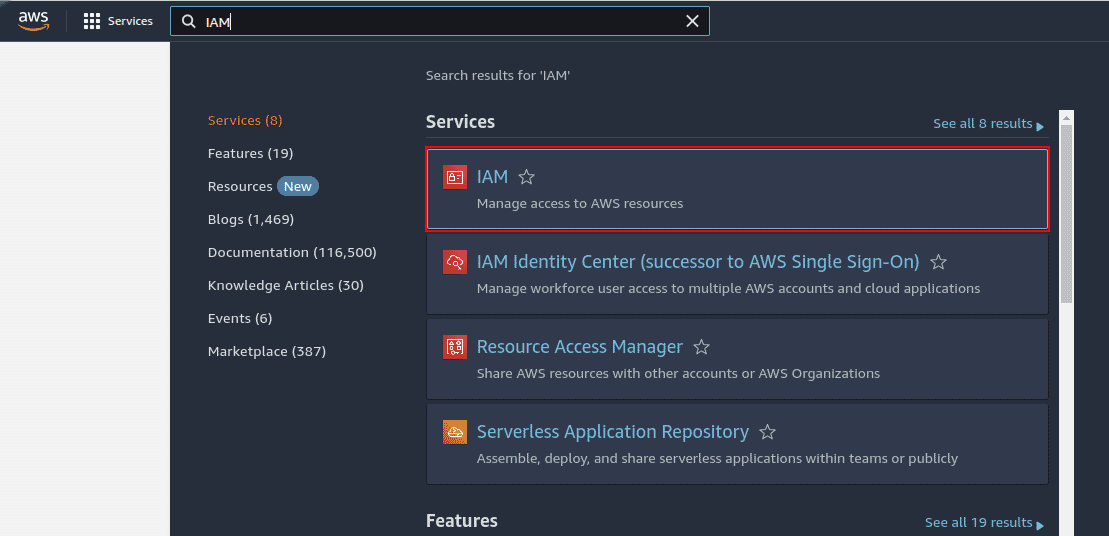
-
On the left navigation panel, click on Users under Access management
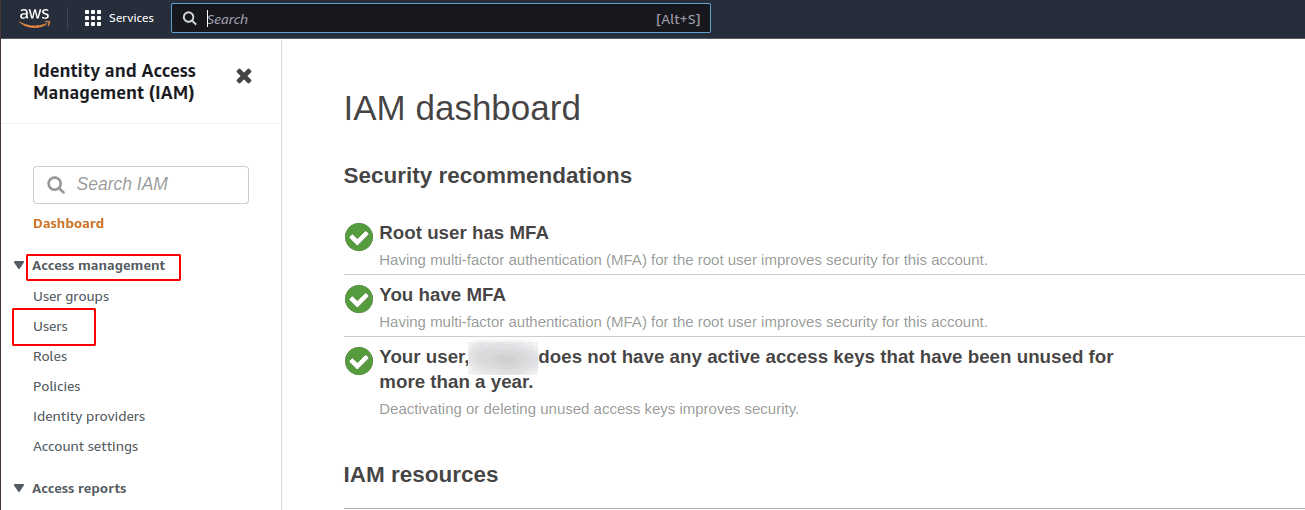
-
On the Users page we can see the MFA status for users under the MFA column. Click on user name for which you want to enable MFA
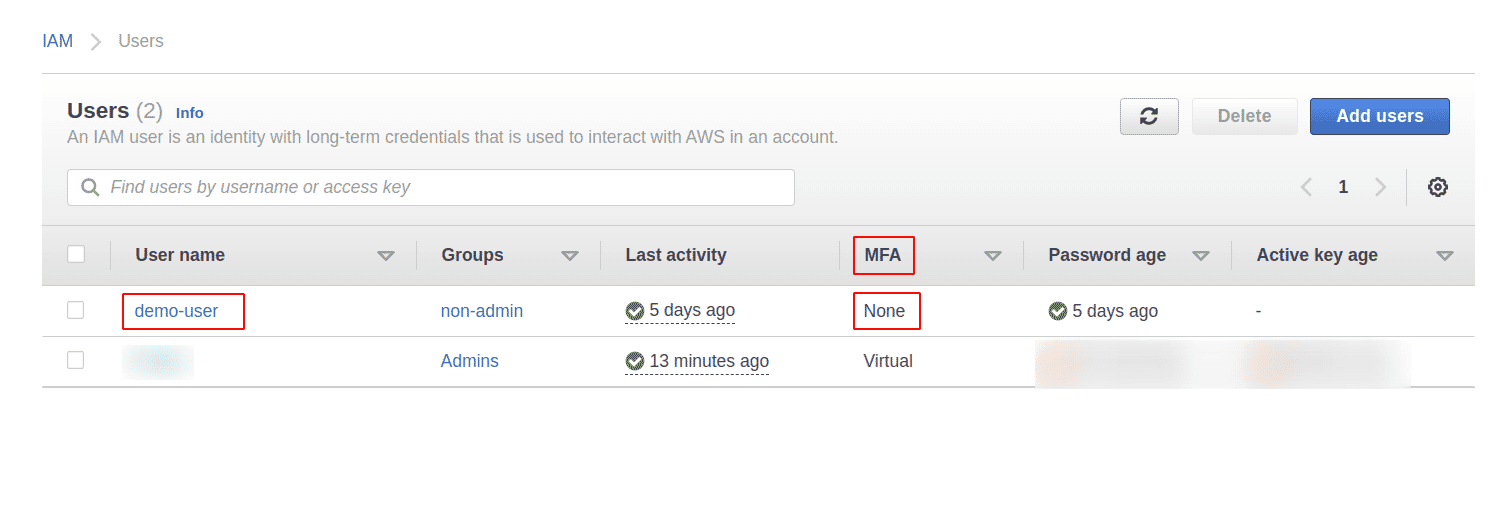
-
On the Summary page, go to Security credentials tab and click on Assign MFA device under Multi-factor authentication (MFA) section
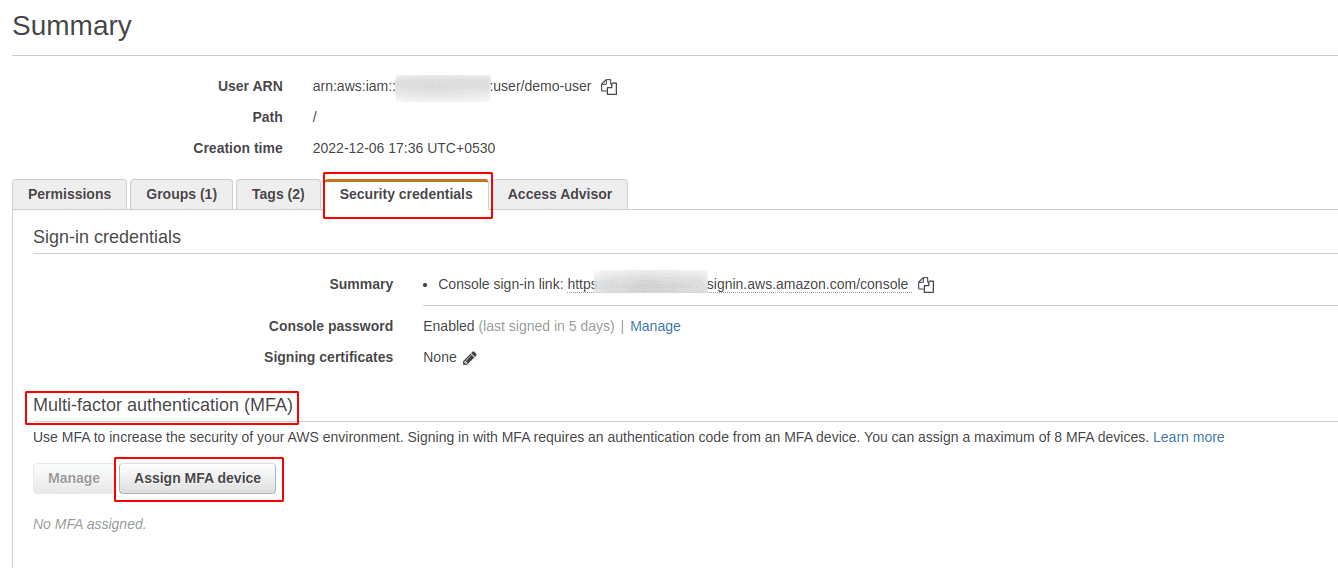
-
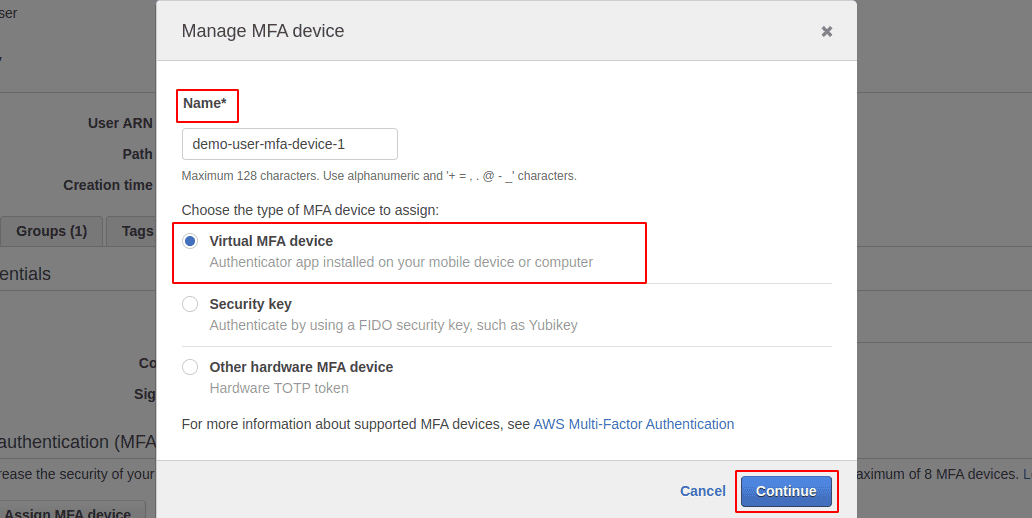
A pop-up will show up. Provide a name for the MFA device being assigned and select the type of MFA device that you want to assign. In this article we will select Virtual MFA device and click on Continue
-
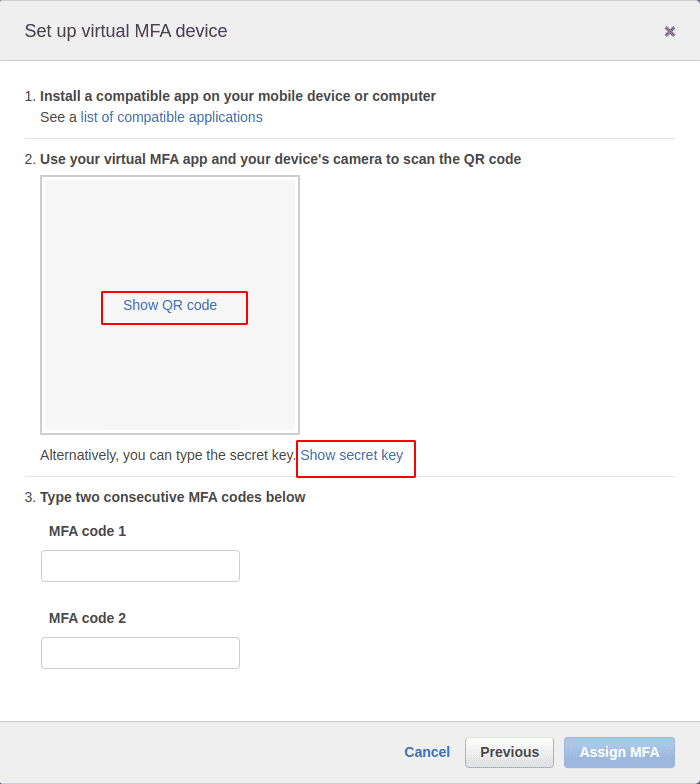
Depending on the mobile or computer application that will be used by the user for whom MFA is being set up, if they have the option of scanning QR code, click on Show QR code and scan it to proceed with the set up. MFA can be set up using the secret key also if they do not want to or have the option of scanning the QR code. Click on show secret key, then copy the key, and set up the MFA device
-
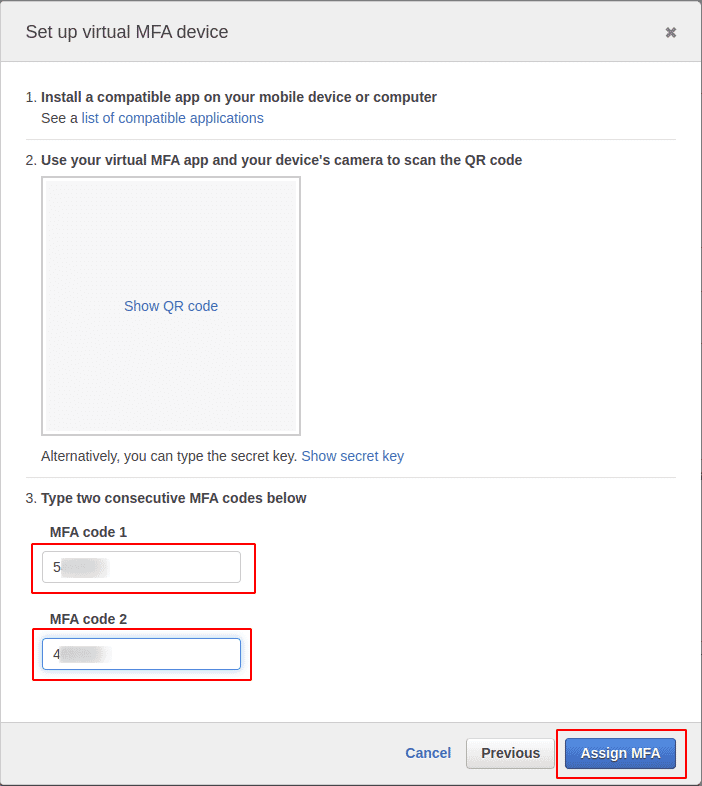
Now provide two consecutive MFA codes and click on Assign MFA. This will set up the virtual MFA device for the user
-
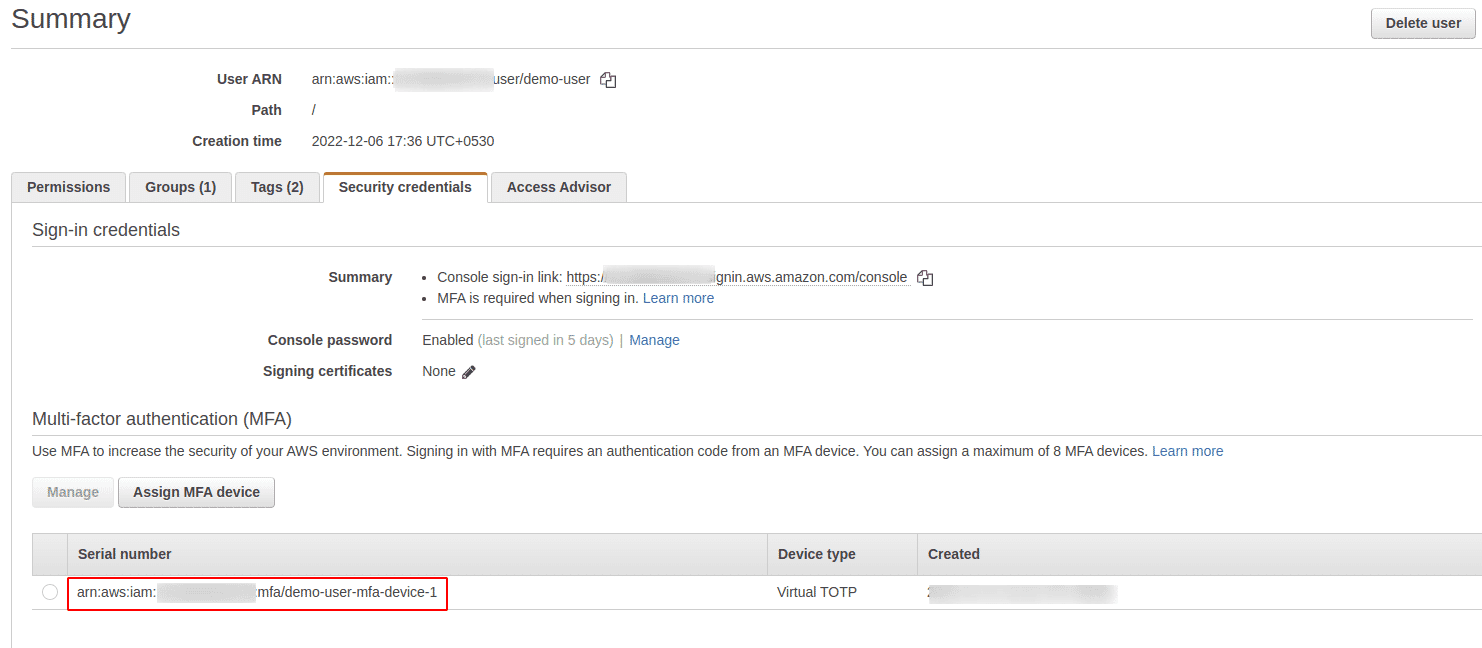
On the Summary page, we can now see that the MFA device has been successfully set up for the user

Riyaz Walikar
Founder & Chief of R&D
Riyaz is the founder and Chief of R&D at Kloudle, where he hunts for cloud misconfigurations so developers don’t have to. With over 15 years of experience breaking into systems, he’s led offensive security at PwC and product security across APAC for Citrix. Riyaz created the Kubernetes security testing methodology at Appsecco, blending frameworks like MITRE ATT&CK, OWASP, and PTES. He’s passionate about teaching people how to hack—and how to stay secure.

Riyaz Walikar
Founder & Chief of R&D
Riyaz is the founder and Chief of R&D at Kloudle, where he hunts for cloud misconfigurations so developers don’t have to. With over 15 years of experience breaking into systems, he’s led offensive security at PwC and product security across APAC for Citrix. Riyaz created the Kubernetes security testing methodology at Appsecco, blending frameworks like MITRE ATT&CK, OWASP, and PTES. He’s passionate about teaching people how to hack—and how to stay secure.