In the event of passwords being breached, a reused password can allow an attacker to take over a user account or compromise the entire AWS account.
Preventing password reuse increases account resiliency against brute force login attempts. AWS IAM password policies can prevent the reuse of a given password by the same user by enabling Prevent password reuse policy.
In the absence of this policy, there is no way to prevent users from reusing their old passwords after expiry or when password change operations are performed.
Here’s how you can enable Prevent Password Reuse policy on AWS via the console and CLI
https://www.youtube.com/watch?v=j4OO06TaQUs&t=17s
Sign in to the AWS Management console
Navigate to IAM service
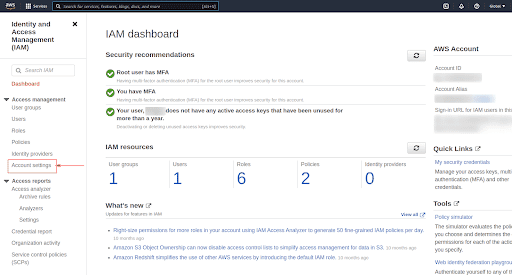
On the left menu, click on Account settings
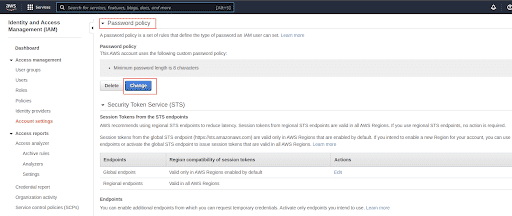
Under Password Policy section, click on Change password policy button
Check the Prevent password reuse checkbox
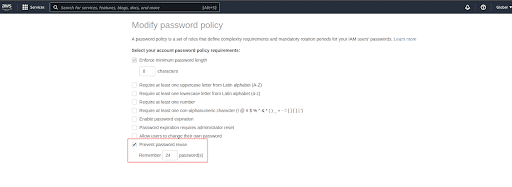
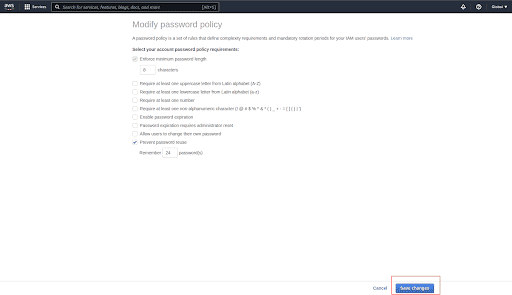
For the password history, we can set the value between 1 and 24. As per CIS benchmark we should set this value to 24 or you can set it up as per your organization’s policies and processes
Click on Save changes. This will enable the password policy to prevent reuse of old passwords
https://www.youtube.com/watch?v=QoYvhwoHSjA&t=2s
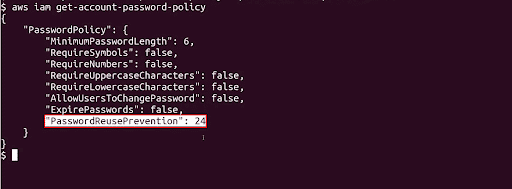
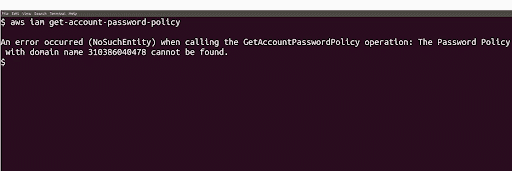
To check password policy manually, run get account password policy command
aws iam get-account-password-policyWe can see that this policy has not been enabled yet
Run update account password policy command on your terminal with password reuse prevention parameter value set to an integer between 1 and 24
aws iam update-account-password-policy \
--password-reuse-prevention 24(As per CIS benchmark we should set this value to 24 or you can set it up as per your organization’s policies and processes)
To check if the policy has been updated, run the command in step 1 again