Introduction
S3 buckets can be configured to allow the global principal to access the bucket via the bucket policy or through ACL. This policy should be restricted only to known users or accounts. Setting the bucket policy to public access would make all the contents in the bucket public.
AWS allows users to set visibility and access permissions for a bucket and the objects within at a granular level using bucket policies. One of the most dangerous configurations is to have a bucket with public Internet wide access with all objects within becoming public. An S3 bucket with full access to any Internet user has the All Users group permission, represented by http://acs.amazonaws.com/groups/global/AllUsers assigned to it. An attacker can simply browse to the HTTP address of the S3 bucket with a browser and download objects from within.
The most common cause of data breaches in AWS, the exposure of buckets and their contains will result in a data incident. Based on the quantity and type of data uncovered, it may be possible for additional attacks within the AWS target environment.
Steps to enable public access block for Bucket
-
Log in to your AWS account and navigate to S3 dashboard.
-
In the left navigation panel, choose Buckets to access the S3 buckets list
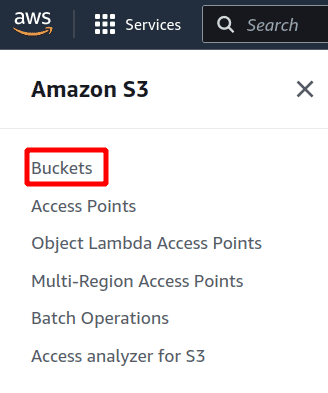
-
Select the bucket, click on Permissions tab and in the section Block public access (bucket settings) click on Edit
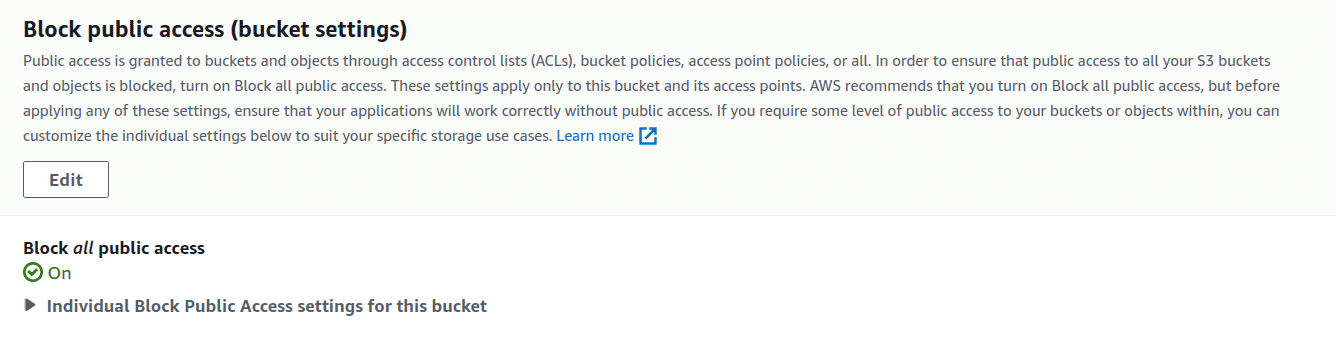
-
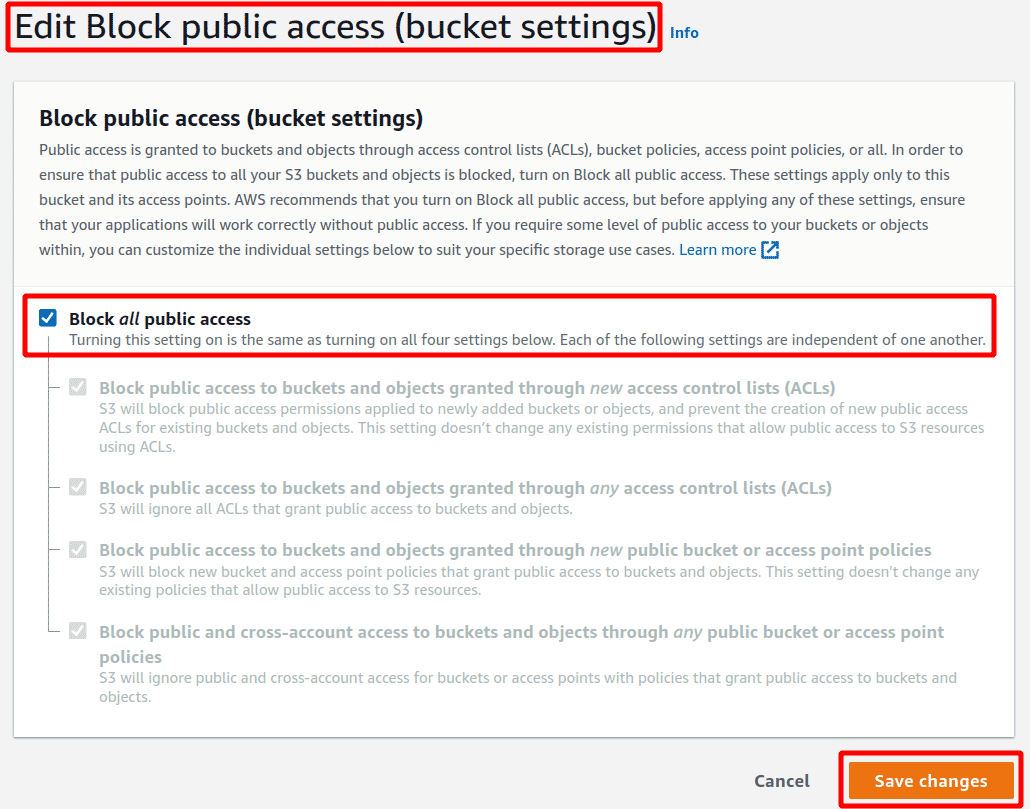
Check the checkbox Block all public access and click on Save changes

Riyaz Walikar
Founder & Chief of R&D
Riyaz is the founder and Chief of R&D at Kloudle, where he hunts for cloud misconfigurations so developers don’t have to. With over 15 years of experience breaking into systems, he’s led offensive security at PwC and product security across APAC for Citrix. Riyaz created the Kubernetes security testing methodology at Appsecco, blending frameworks like MITRE ATT&CK, OWASP, and PTES. He’s passionate about teaching people how to hack—and how to stay secure.

Riyaz Walikar
Founder & Chief of R&D
Riyaz is the founder and Chief of R&D at Kloudle, where he hunts for cloud misconfigurations so developers don’t have to. With over 15 years of experience breaking into systems, he’s led offensive security at PwC and product security across APAC for Citrix. Riyaz created the Kubernetes security testing methodology at Appsecco, blending frameworks like MITRE ATT&CK, OWASP, and PTES. He’s passionate about teaching people how to hack—and how to stay secure.