Introduction
Elastic Block Storage (EBS) snapshots are snapshots of the volume at a particular moment in time. These snapshots can be shared and recreated into volumes for other instances. AWS provides the provision to share these snapshots with other AWS customers via the “Permissions” tab of the snapshot.
Since a snapshot is equivalent to the EBS volume, an attacker with access to a snapshot can read and gain access to data within the snapshot if it is unencrypted. It is recommended to implement data encryption in order to protect it from attackers or unauthorised users.
In this article we will take a look at how to encrypt an EBS snapshot via AWS management console.
Encrypt AWS EBS snapshot
To encrypt an EBS snapshot, follow the steps below in the AWS management console:
-
Login to the AWS Management Console and navigate to EC2 dashboard
-
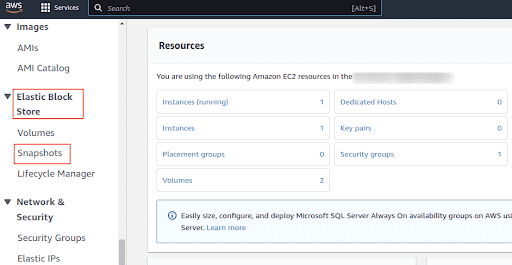
In the navigation panel, under Elastic Block Store, click Snapshots
-
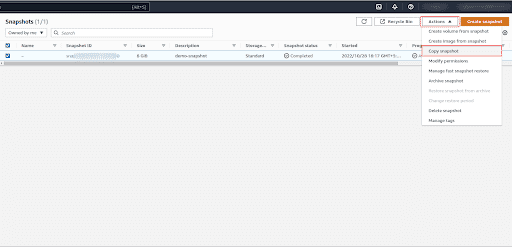
Select the unencrypted Snapshot that you want to update
-
Click on Actions dropdown and select Copy snapshot
-
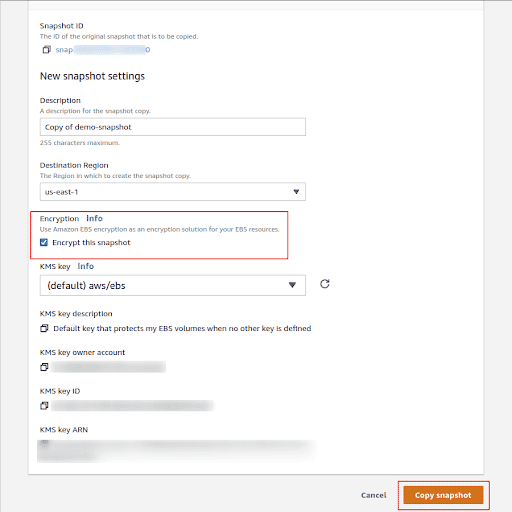
Define the Destination, Description and check the Encrypt this snapshot option, select the Customer Master Key (CMK) and click on Copy snapshot
-
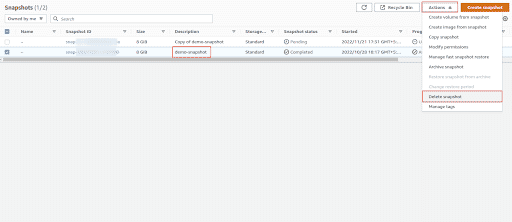
Delete the original unencrypted snapshot by selecting the snapshot and clicking on Actions dropdown button from the dashboard top menu and choose Delete

Riyaz Walikar
Founder & Chief of R&D
Riyaz is the founder and Chief of R&D at Kloudle, where he hunts for cloud misconfigurations so developers don’t have to. With over 15 years of experience breaking into systems, he’s led offensive security at PwC and product security across APAC for Citrix. Riyaz created the Kubernetes security testing methodology at Appsecco, blending frameworks like MITRE ATT&CK, OWASP, and PTES. He’s passionate about teaching people how to hack—and how to stay secure.

Riyaz Walikar
Founder & Chief of R&D
Riyaz is the founder and Chief of R&D at Kloudle, where he hunts for cloud misconfigurations so developers don’t have to. With over 15 years of experience breaking into systems, he’s led offensive security at PwC and product security across APAC for Citrix. Riyaz created the Kubernetes security testing methodology at Appsecco, blending frameworks like MITRE ATT&CK, OWASP, and PTES. He’s passionate about teaching people how to hack—and how to stay secure.