Introduction
AWS S3, apart from providing the ability to perform Server Side Encryption (SSE) for data, also provides the ability to send data over an encrypted transport layer to ensure data protection in transit. This is implemented via a bucket policy with an “Effect”: “Deny” along with the boolean condition “aws:SecureTransport”: “false”. This effectively prevents the bucket’s contents from being served over plaintext HTTP.
Steps to enforce SSL/TLS for S3 requests using CLI
-
Run the following command to fetch the bucket policy if it exists or not.
aws s3api get-bucket-policy --bucket <bucket_name>If the bucket policy does not exist and a
NoSuchBucketPolicyerror is returned.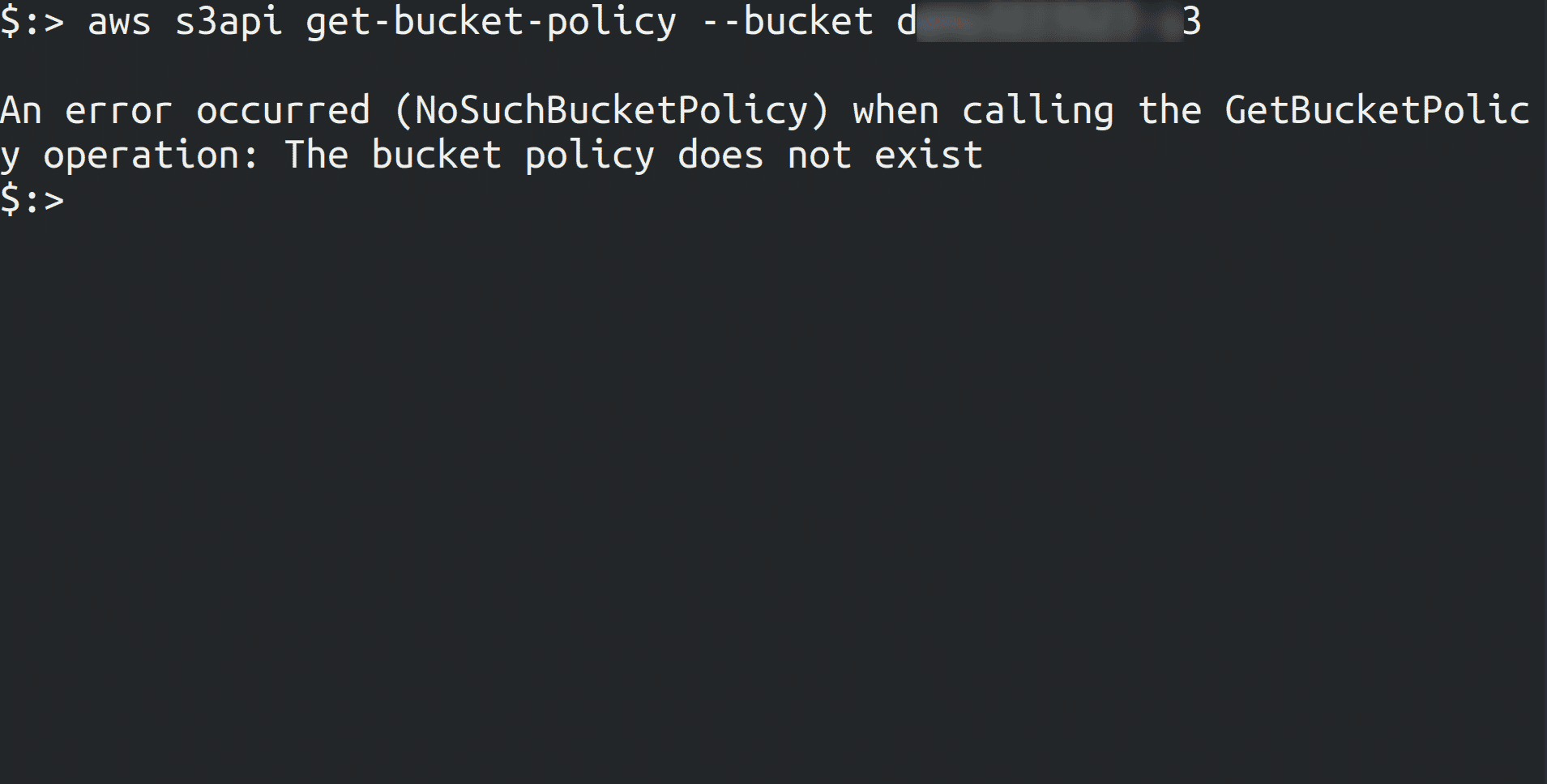
-
If the bucket policy exists but there is no statement with the following structure (only the “Condition” key segment, Action, resource, and effect keys can have different values) and
"Effect": "Allow"along with the condition segment then it is not the required policy for HTTPS requests on an S3 Bucket:"Statement": { "Effect": "Allow", "Action": "s3:*", "Resource": "arn:aws:iam::123412341234:user/*", "Condition": {"Bool": {"aws:SecureTransport": "true"}} # The line that matters for evaluating the misconfiguration } -
Set bucket policy to only allow HTTPS requests on an S3 Bucket
aws s3api put-bucket-policy --bucket <bucket_name> --policy '{"Version":"2012-10-17","Statement":[{"Effect":"Allow","Principal":{"AWS":["<AWS_account_ID>"]},"Action":"s3:Get*","Resource":"<bucket_ARN>/*"},{"Effect":"Deny","Principal":"*","Action":"*","Resource":"<bucket_ARN>/*","Condition":{"Bool":{"aws:SecureTransport":"false"}}}]}'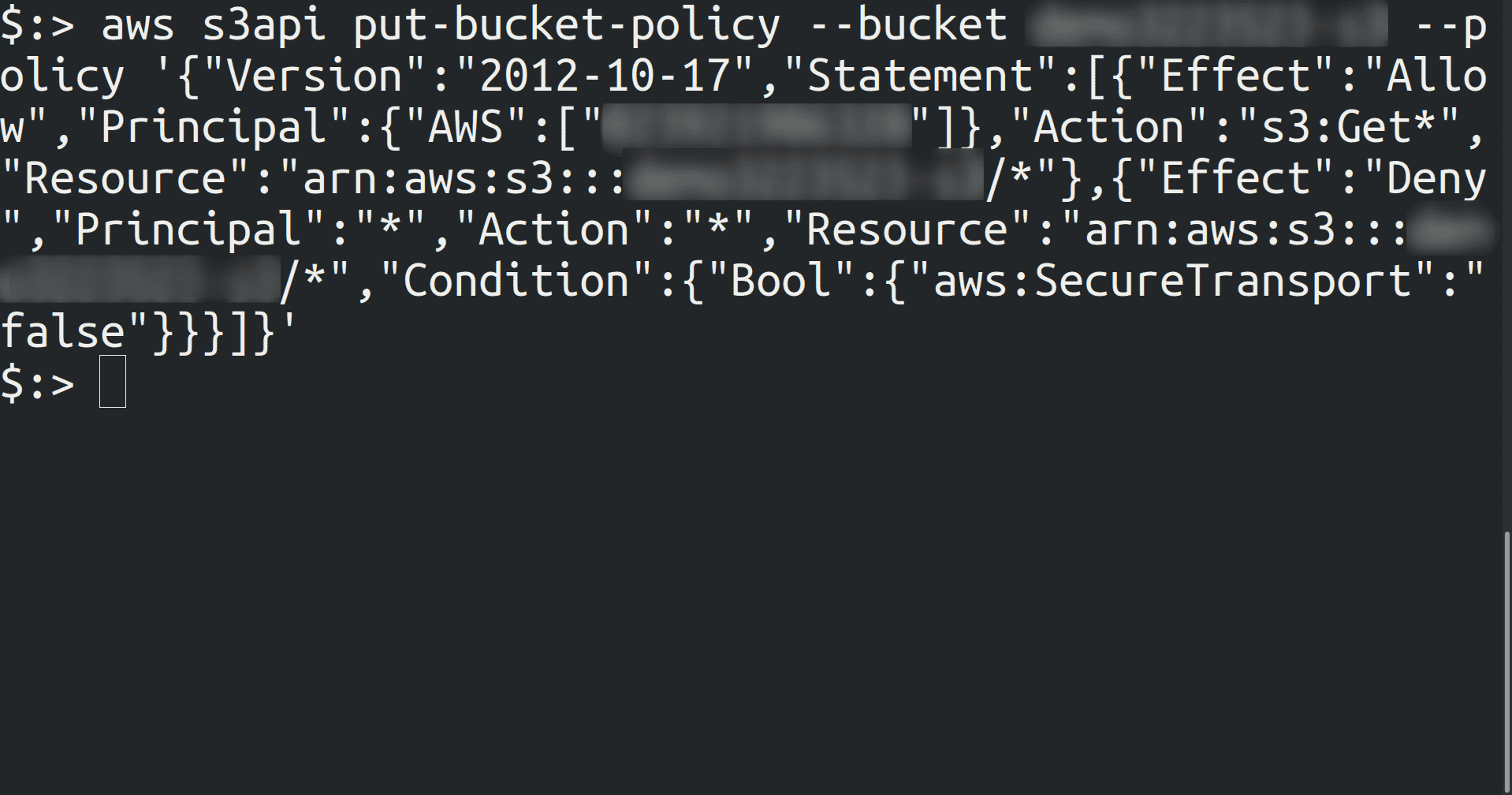

Riyaz Walikar
Founder & Chief of R&D
Riyaz is the founder and Chief of R&D at Kloudle, where he hunts for cloud misconfigurations so developers don’t have to. With over 15 years of experience breaking into systems, he’s led offensive security at PwC and product security across APAC for Citrix. Riyaz created the Kubernetes security testing methodology at Appsecco, blending frameworks like MITRE ATT&CK, OWASP, and PTES. He’s passionate about teaching people how to hack—and how to stay secure.

Riyaz Walikar
Founder & Chief of R&D
Riyaz is the founder and Chief of R&D at Kloudle, where he hunts for cloud misconfigurations so developers don’t have to. With over 15 years of experience breaking into systems, he’s led offensive security at PwC and product security across APAC for Citrix. Riyaz created the Kubernetes security testing methodology at Appsecco, blending frameworks like MITRE ATT&CK, OWASP, and PTES. He’s passionate about teaching people how to hack—and how to stay secure.