Background
AWS has a multitude of services, created to solve specific problems and in working with each other, run entire organisations and their businesses. From an attacker point of view, gaining access to any service within AWS can mean additional information leakage and potential access to customer data and intellectual property in the form of code and business intelligence.
From a technical standpoint, there are 2 attack approaches that can be used to compromise AWS resources.
- Enumerating externally visible footprint and exploiting a weakness therein
- Gaining access to access credentials of an AWS IAM user or role and then using that access to gain a foothold into the account.
Both of these approaches have various facets and can be used in conjunction with each other depending on what kind of information is available when beginning the attack.
In this article, we will look at various ways by which you can enumerate the public IP addresses within AWS, as that is a common facet that attackers use when launching attacks from the Internet. Attackers use public-facing IP addresses to run port scans to identify what services could potentially be listening on these IPs and then attack each of these services based on identified weaknesses.
Remember, as the sheer size of services in AWS is pretty large, not all services are covered. The ones listed below are the most common services within AWS that are used with an external endpoint.
AWS IP Ranges
AWS publishes its public IP address ranges in JSON format. You can download the latest current version from https://docs.aws.amazon.com/general/latest/gr/aws-ip-ranges.html.
Whenever AWS has an IP address range update, a new JSON is published for download. It is the user’s responsibility to maintain history for the JSON files, by saving successive versions locally.
Providing the IP ranges to customers allows customers to set up network level access control via firewalls or authentication servers. Basically, if you ever set up a system that can whitelist sources, this json file would give you the information needed to whitelist your traffic coming from the AWS platform.
All public IP addresses that are assigned by AWS across all services are present in this JSON. So if you ever created an Elastic IP, it came from the pools mentioned in this JSON.
Identifying AWS Public IP addresses for different services
This section will take you through various services that expose a public DNS record or IP address including the commonly used Elastic IPs for AWS Compute.
AWS EC2
AWS EC2 allows users to set up public access via various means. The most common configurations include an ephemeral public IP that changes when the EC2 is rebooted and an Elastic IP that remains static and can be assigned to other instances. Another common way to expose a service running on EC2 to the world is using a Load balancer but we will look at that in the next section.
Let’s look at enumerating public IPs via the EC2 service.
Ephemeral IP - Using the console
-
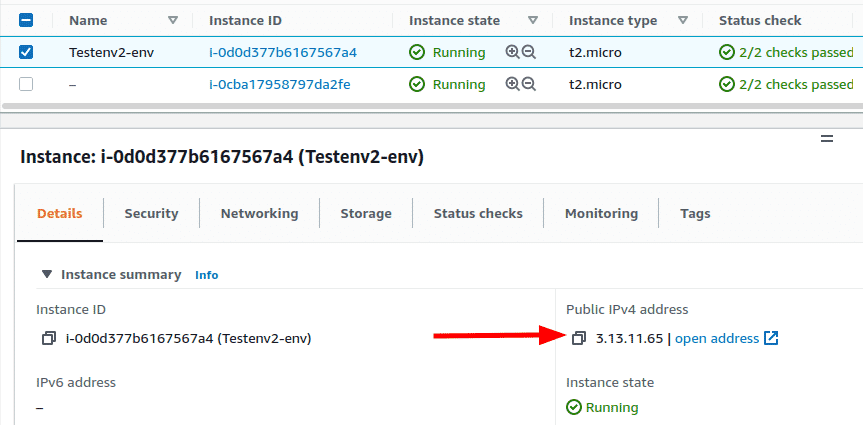
Login to the AWS console and navigate to the EC2 service
-
Select the instance and look at the “Public IPv4 address” field under “Instance summary” in the bottom pane
-
This needs to be repeated for every instance in every region in case you want complete cloud coverage.
Ephemeral IP - Using the command line
Note: The command line makes no distinction between Elastic IPs and Ephemeral IPs
-
Configure your AWS command line profile
-
Run the following command, to fetch the public IP of an instance with instance ID “i-0d0d377b6167567a4” and in the “us-east-2” region. Change the value of “—region” to fetch IPs from other regions.
aws ec2 describe-instances --instance-ids i-0d0d377b6167567a4 --query=Reservations[].Instances[].PublicIpAddress --region us-east-2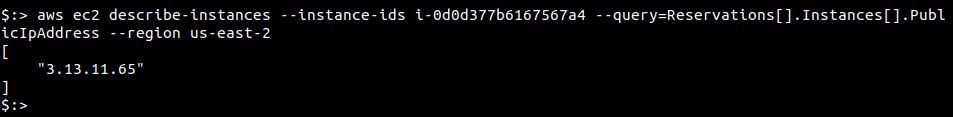
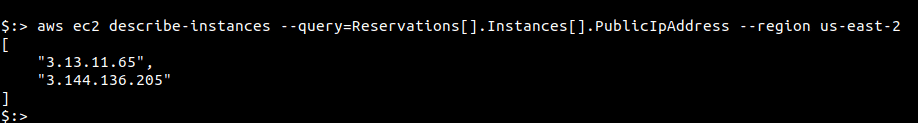
You can also remove the instance Ids to fetch IP information for all the instances in one command. However, this is still region restricted.
Elastic IP - Using the console
-
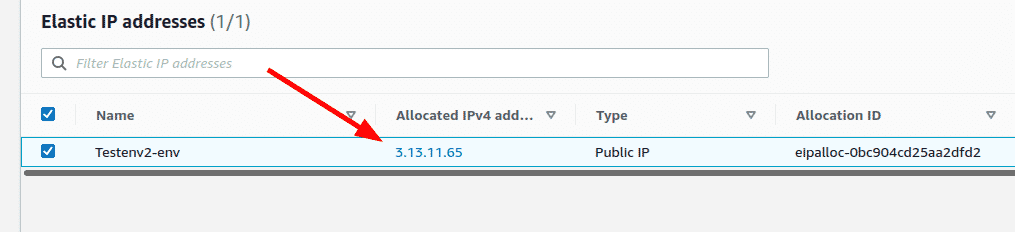
Login to the AWS console and navigate to Elastic IP under “Network & Security” under EC2 service.
-
Click on the IP address listed in the console page to see more information about the Elastic IP including if it is associated with any EC2 instance
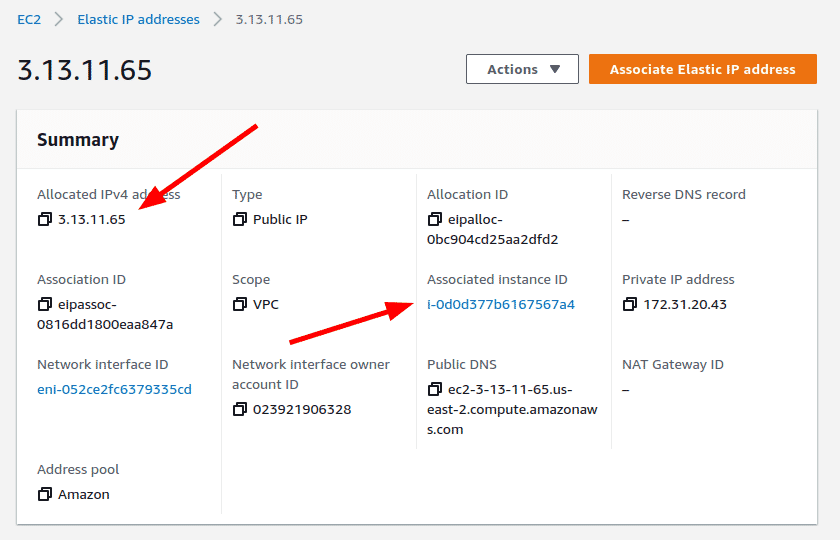
Elastic IP - Using the command line
Note: This command exclusively fetches the Elastic IP but does not list any Ephemeral IPs that may be assigned
-
Configure your AWS command line profile
-
Run the following command to fetch Elastic IPs in the “us-east-2” region. Change the value of “—region” to fetch IPs from other regions.
aws ec2 describe-addresses --query Addresses[*].PublicIp --region us-east-2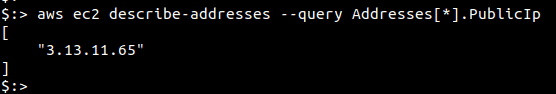
AWS EC2 Load Balancers
Elastic Load Balancing automatically distributes incoming traffic across multiple targets, such as EC2 instances, containers, and IP addresses, in one or more Availability Zones.
We can enumerate Load Balancer IP addresses using the following steps via the console and the command line.
Load Balancer IPs via Console
-
Login to the AWS console and navigate to “Load Balancers” under “Load Balancing” under EC2 service in the left pane.
-
Select the Load Balancer whose public IP you want to enumerate
-
Under the “Description” pane copy the DNS name of the Load Balancer. This is the public DNS name to which external communication can be made
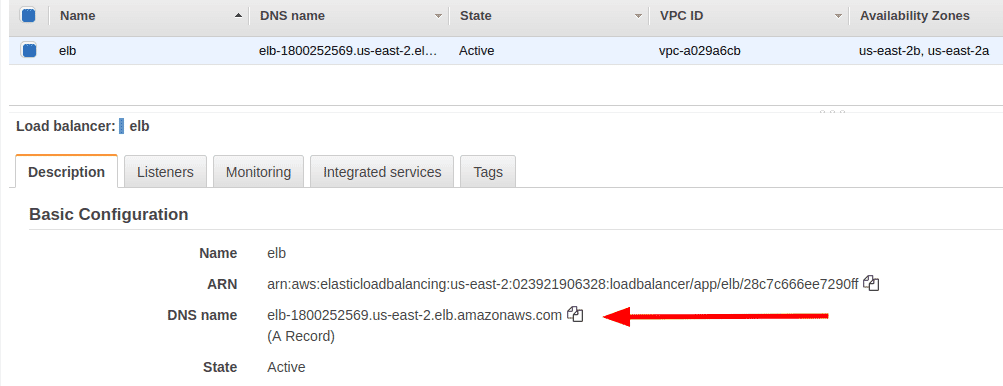
-
To find its IP address, you can run the nslookup or the dig command as shown below
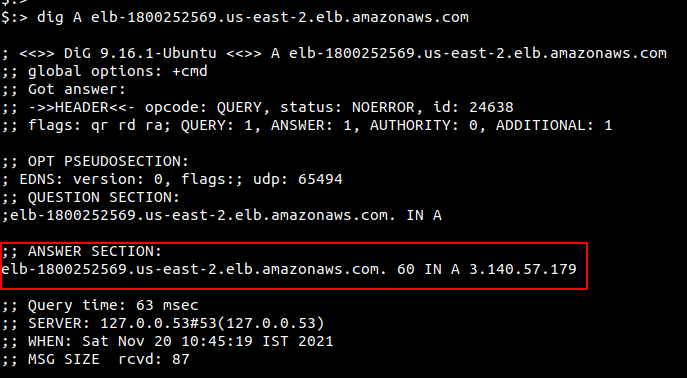
Load Balancer IPs via AWS Command Line
-
Configure your AWS command line profile
-
Run the following command to fetch the Load Balancer DNS name in the “us-east-2” region. Change the value of “—region” to fetch IPs from other regions.
aws elbv2 describe-load-balancers --query LoadBalancers[*].DNSName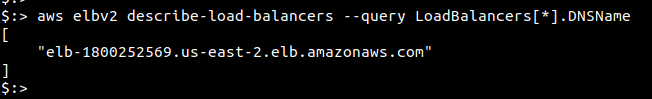
-
You can then use nslookup or dig to fetch the IP address from the DNS name as shown in the previous section.
AWS RDS
Amazon Relational Database Service (RDS) makes it easy to set up, operate, and scale a relational database in the cloud. When a RDS instance is created, it can be set up to be publicly accessible. The AWS console and CLI provide the public DNS endpoint for the RDS instance.
Although a different service within AWS, other database related services like DynamoDB and ElastiCache would also expose an external hostname for consumption.
RDS Instance IPs via Console
-
Login to the AWS console and navigate to “Databases” under the “Amazon RDS” service.
-
Select a database whose public endpoint you wish to identify. The endpoint is visible under the “Connectivity & security” tab on the page
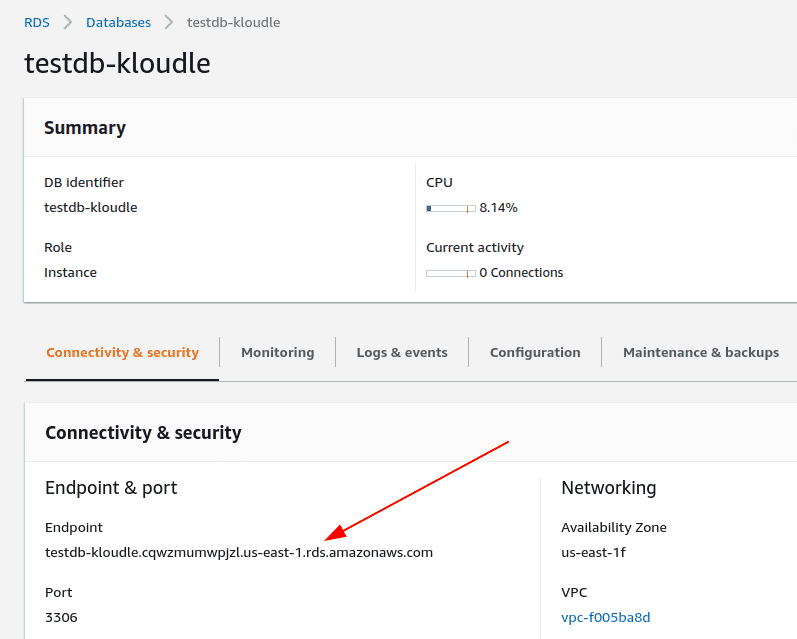
-
To find its IP address, you can run the nslookup or the dig command as shown below
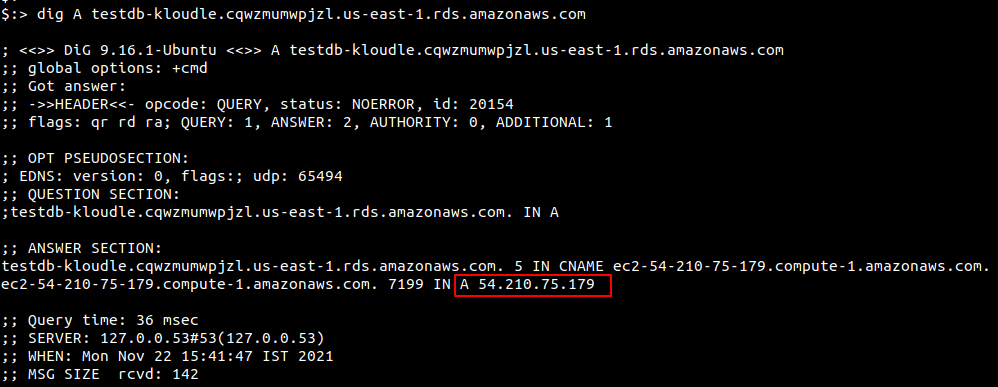
RDS IPs via AWS Command Line
-
Configure your AWS command line profile
-
Run the following command to fetch the RDS DNS name in the “us-east-2” region. Change the value of “—region” to fetch the DNS name for RDS in other regions.
aws rds describe-db-instances --query=DBInstances[*].Endpoint.Address --region us-east-2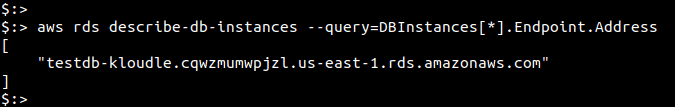
-
You can then use nslookup or dig to fetch the IP address from the DNS name as shown in the previous section.
AWS API Gateway
Amazon API Gateway is an AWS service for creating, publishing, maintaining, monitoring, and securing REST, HTTP, and WebSocket APIs at any scale. API developers can create APIs that access AWS or other web services, as well as data stored in the AWS Cloud.
AWS API Gateway supports API types for HTTP, WebSocket and REST APIs. Each of these published endpoints have a DNS name created which can be accessed publicly over the Internet.
The AWS CLI does not have a way to list HTTP API or WebSocket API endpoints, so we resort to only using the web console.
HTTP API Gateway IPs via Console
-
Login to the AWS console and navigate to “API Gateway”
-
Click “APIs” in the left pane and select the HTTP API whose public endpoint you wish to identify. The endpoint is visible under the “Stages for
section 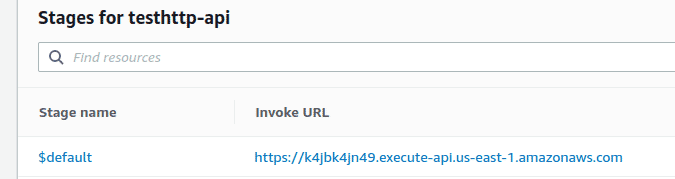
-
To find its IP address, you can run the nslookup or the dig command as shown below
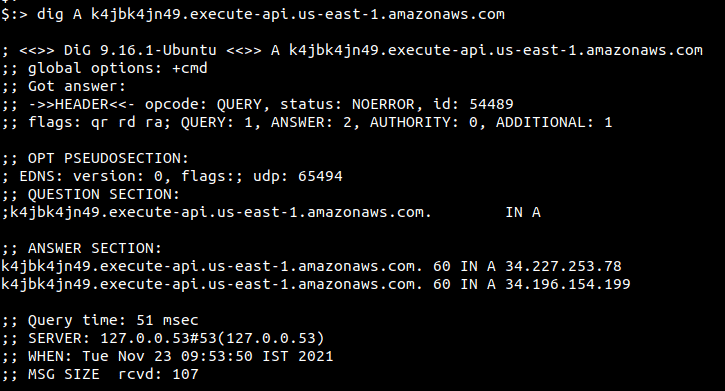
WebSocket API Gateway IPs via Console
-
Login to the AWS console and navigate to “API Gateway”
-
Click “APIs” in the left pane and select the WebSocket API whose public endpoint you wish to identify.
-
Click on “Stages” on the left and select a Stage (production for example). The endpoint will be listed as “WebSocket URL:” on the top half of the page
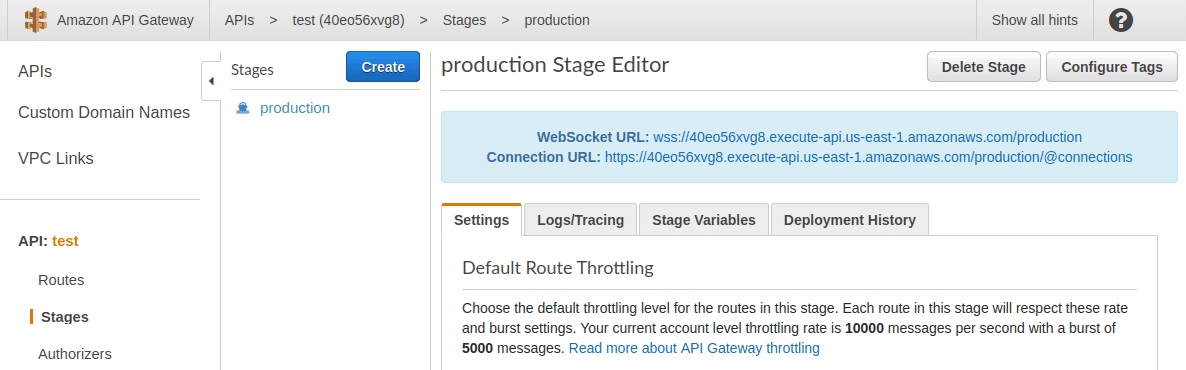
-
To find its IP address, you can run the nslookup or the dig command as shown below
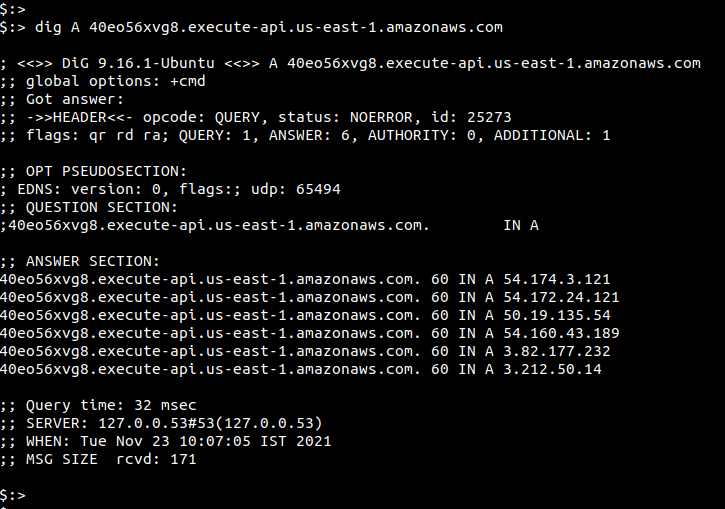
REST API Gateway IPs via Console
-
Login to the AWS console and navigate to “API Gateway”
-
Click “APIs” in the left pane and select the REST API whose public endpoint you wish to identify
-
Click on “Stages” on the left and select a Stage (production for example). The endpoint will be listed as “Invoke URL:” on the top half of the page
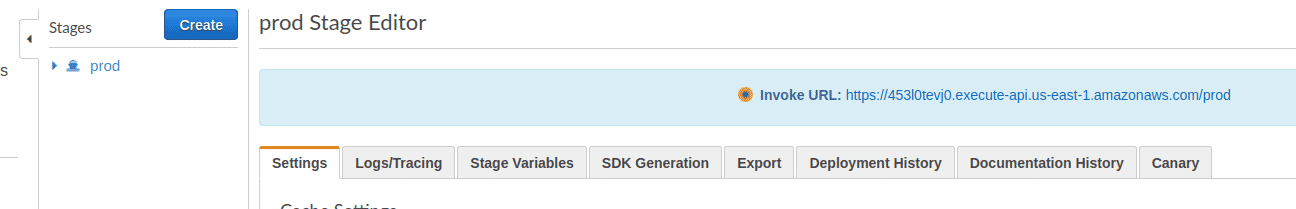
-
To find its IP address, you can run the nslookup or the dig command as shown below

REST API Gateway IPs via AWS Command Line
-
Configure your AWS command line profile
-
Run the following command to fetch all REST API details in the “us-east-1” region. Change the value of “—region” to fetch the data from other regions.
aws apigateway get-rest-apis --region us-east-1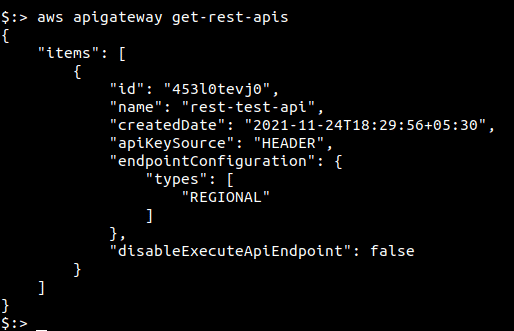
-
The DNS name can be constructed from the values of REST API id and the AWS region using the following format:
<id>.execute-api.<region>.amazonaws.com -
The IP address can then be obtained via a dig or nslookup command as shown in the previous section.
AWS Elastic Beanstalk
Amazon Elastic Beanstalk is an easy-to-use service for deploying and scaling web applications and services developed with Java, .NET, PHP, Node.js, Python, Ruby, Go, and Docker on familiar servers such as Apache, Nginx, Passenger, and IIS.
AWS Elastic Beanstalk public IPs via Console
-
Login to the AWS console and navigate to “Elastic Beanstalk”
-
Click “Environments” from the left pane
-
In the list of environments, identify the Environment that has a “URL”
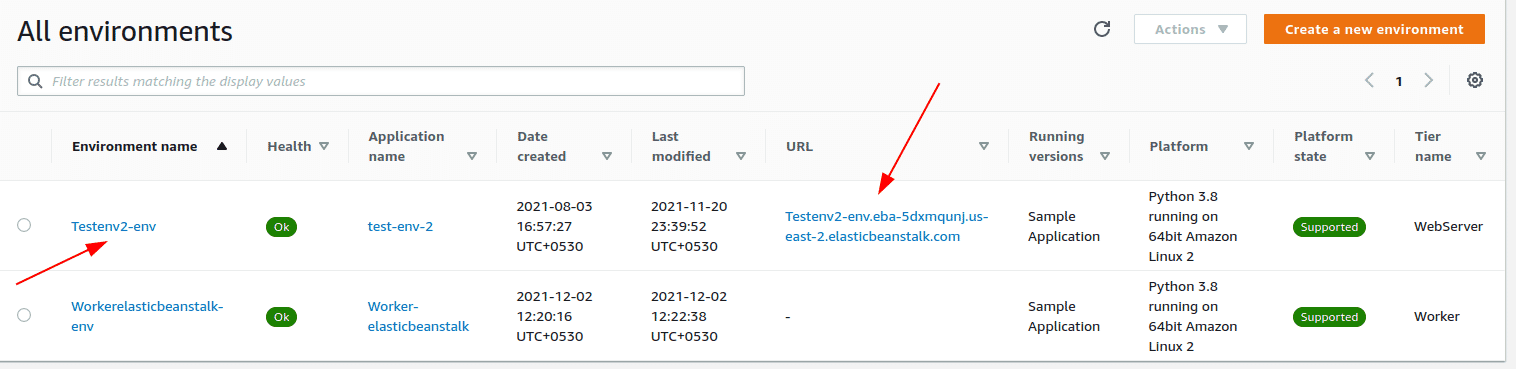
-
Copy the URL from the page or click the Environment name to see a different view from which the URL can be copied
-
To find its IP address, you can run the nslookup or the dig command as shown below
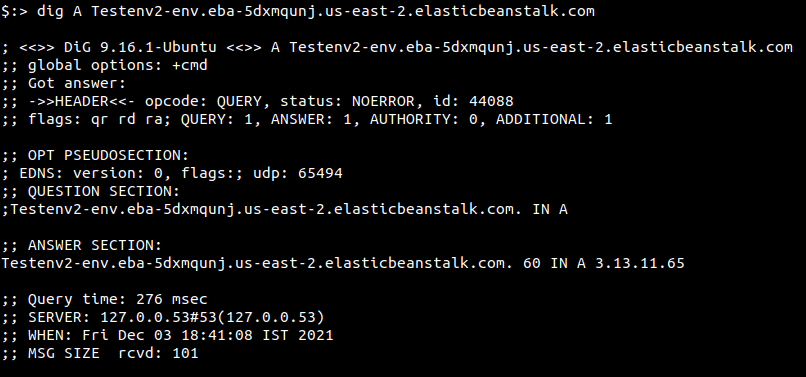
AWS Elastic Beanstalk public IPs via AWS Command Line
-
Configure your AWS command line profile
-
Run the following command to fetch details of all the Elastic Beanstalk instances in the “us-east-1” region. Change the value of “—region” to fetch the data from other regions.
aws elasticbeanstalk describe-environments --query Environments[*].EndpointURL --region us-east-1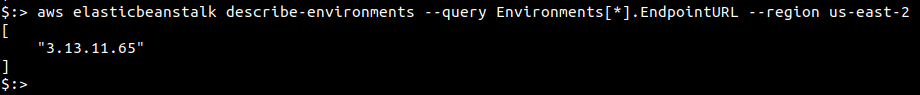
Conclusion
Identifying your attack surface is the key to defending your account from malicious actors, bots and targeted threats. Externally accessible endpoints of an organisation are a very important facet of the attack surface. Knowledge of external IP addresses and hostnames allows attackers to poke around what is hosted and identify potential weaknesses beyond the network layer.
On the other hand, knowledge of the external attack surface, public IPs and accessible hostnames allows SREs and Ops to take measures to strengthen their defences to thwart attacks. Although many of the services within AWS are completely managed, which reduces the risks arising from misconfigurations, there may be instances where exposure of the IP addresses and hostnames allows attackers to gain footholds within your account.
This article presents various ways of enumerating the IP address information for common services within AWS and can be used to enumerate them for your account for visibility purposes.
***
This article is brought to you by Kloudle Academy, a free e-resource compilation, created and curated by Kloudle. Kloudle is a cloud security platform that uses the power of automation and simplifies human requirements in cloud security. If you wish to give your feedback on this article, you can write to us here.

Riyaz Walikar
Founder & Chief of R&D
Riyaz is the founder and Chief of R&D at Kloudle, where he hunts for cloud misconfigurations so developers don’t have to. With over 15 years of experience breaking into systems, he’s led offensive security at PwC and product security across APAC for Citrix. Riyaz created the Kubernetes security testing methodology at Appsecco, blending frameworks like MITRE ATT&CK, OWASP, and PTES. He’s passionate about teaching people how to hack—and how to stay secure.

Riyaz Walikar
Founder & Chief of R&D
Riyaz is the founder and Chief of R&D at Kloudle, where he hunts for cloud misconfigurations so developers don’t have to. With over 15 years of experience breaking into systems, he’s led offensive security at PwC and product security across APAC for Citrix. Riyaz created the Kubernetes security testing methodology at Appsecco, blending frameworks like MITRE ATT&CK, OWASP, and PTES. He’s passionate about teaching people how to hack—and how to stay secure.