Background
Google Cloud allows administrators to create projects which can be used to create and host resources that are aligned with a need. For example, if you want to setup a production deployment pipeline, you can create a new project called kloudle-prod and have your GKE clusters, VMs, storage, databases, Firestore etc. all under this project.
However, there are instances where you would want to access the resources of one project from another. A typical use case would be when you set up a new Google Cloud project for internal tooling and monitoring of other Google Cloud resources.
Google Cloud’s IAM allows you to create a new IAM Service Account and use that to provision access across a new project or even a project in a different account.
How to setup access cross project using Service Accounts
Slight modification but this works now
- Create a new SA in
kloudle-internal-tools(createdcross-project-access@kloudle-internal-tools.iam.gserviceaccount.com) - Give it
OwnerANDEditoraccess (Editor access is explicitly required even ifOwneris provided else the compute can’t use it as an SA, weird).Owneraccess is optional. - Update the VM compute service account (stop and edit the instance) to the SA created in Step 1. Start the VM
- Go to the project that you want to monitor, in our case
app-kloudle-com. Go to IAM. - Use
GRANT ACCESSto add the full email of the SA from step 1 to this account withOwnerprivs. - SSH to the VM in
kloudle-internal-toolsand run the following commands to confirm you have cross project access using the SA account.
gcloud config set project app-kloudle-com
gcloud compute instances list
Consider 2 Google Cloud Projects - kloudle-internal-tools and app-kloudle-com. The task is to set up a compute instance in the kloudle-internal-tools project with access to resources in app-kloudle-com
Create a service account and assign IAM privileges
As access is required from kloudle-internal-tools to app-kloudle-com, we will create a Service Account in kloudle-internal-tools and assign it IAM permissions so that a compute instance can use the Service Account as
Create a new SA
-
Navigate to Service Accounts under IAM at https://console.cloud.google.com/iam-admin/serviceaccounts and click
CREATE SERVICE ACCOUNT -
Create a new Service Account. We are using
cross-project-saas an example.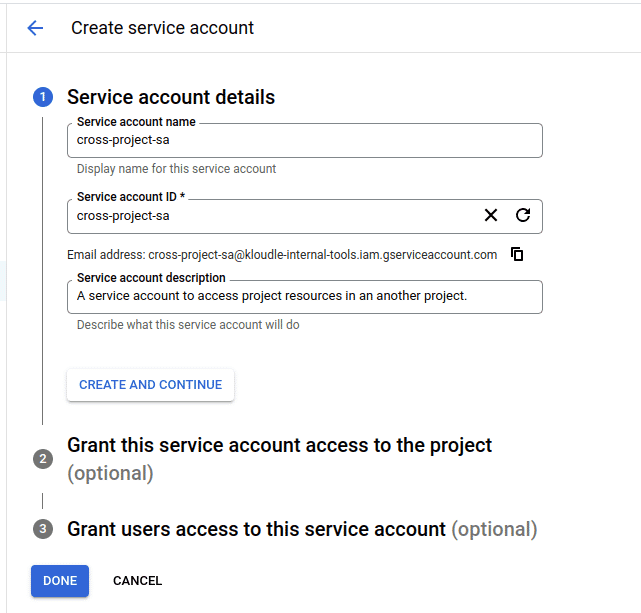
-
Note the email address of the SA. In our case it is -
cross-project-sa@kloudle-internal-tools.iam.gserviceaccount.com
Assign privileges
To use this service account as a compute vm instance’s service account, assign it Editor privileges. This is the default privilege assigned to the default compute service account.
-
Navigate to IAM and admin and click on
GRANT ACCESSto open theAdd principalsection -
Add
cross-project-sa@kloudle-internal-tools.iam.gserviceaccount.comas the new principal and assign itEditorrole.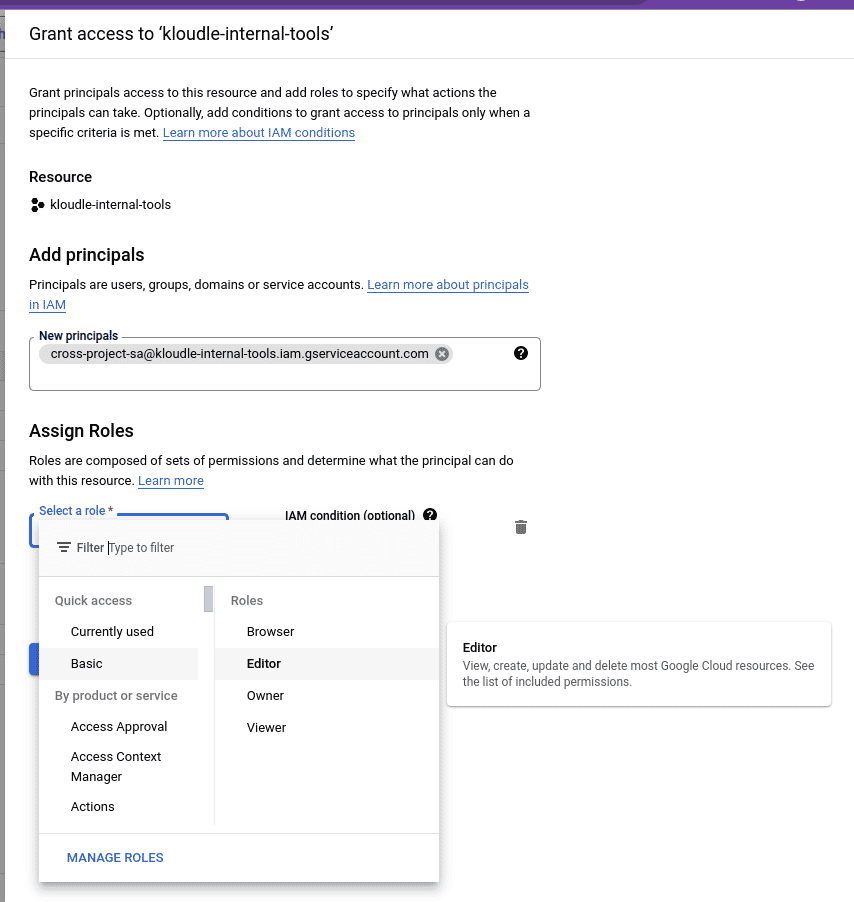
-
This service account now has Editor privileges to the current project,
kloudle-internal-tools. We can now assign this SA to any virtual machine, new or already running to access the service accounts token to perform actions within the current project.
Making the Service Account available via a compute
This section shows how you can add the newly created service account to a Google compute instance (instead of the default account).
For a new VM instance
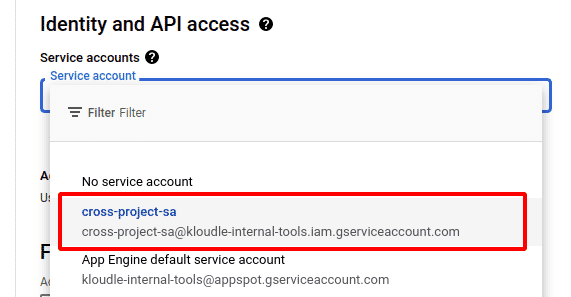
- When creating a new VM instance, select the newly created
cross-project-sa@kloudle-internal-tools.iam.gserviceaccount.comas the service account underIdentity and API accesssection.
For an existing running VM
By design, service accounts cannot be changed for a running VM. The machine should be stopped before edits can be made.
- Identify the VM that will be used to interact with other Google cloud projects
- Stop the VM, either through a SSH shutdown or by using the
STOPbutton - Click on the VM and click on
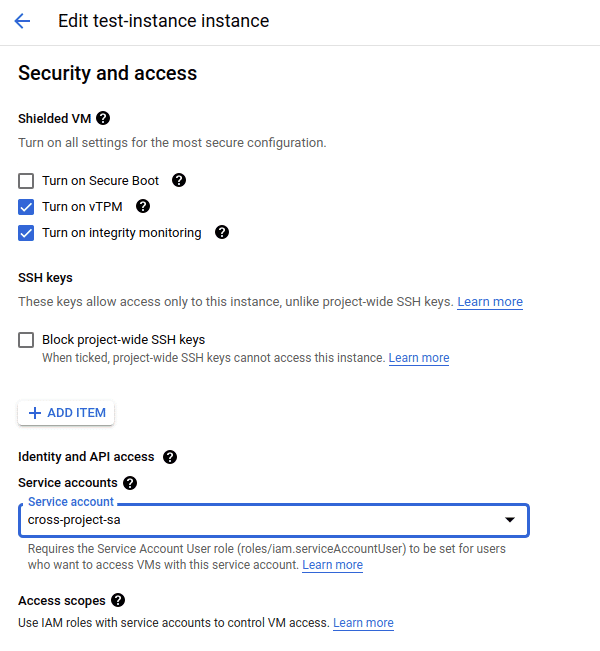
EDIT. - Scroll down to find the
Security and accesssection and select the service account from the drop down. The service account can be updated only when the machine is in stopped state.
Verifying the service accounts availability in your VM
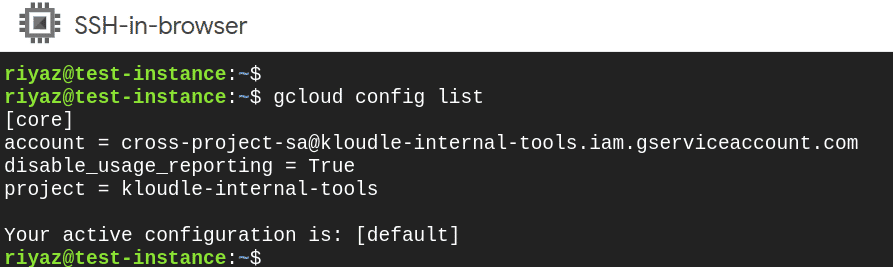
After adding the service account to the VM, we can SSH to the VM and run gcloud commands to check if the service account is set up properly.
- SSH to the VM
- Run the following commands to see that the SA is set up properly
gcloud config list
Setting up cross account access via IAM
We can now set up access to a different project so that the service account can be used to interact with the resources of another project.
Our target Google Cloud project in this example will be app-kloudle-com.
- Switch projects to
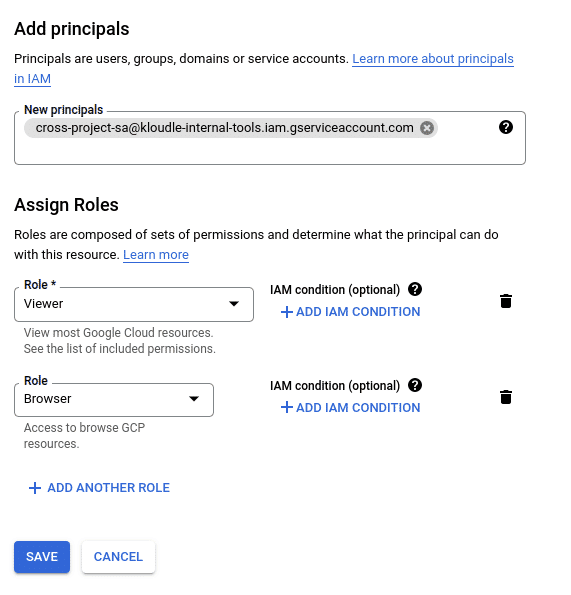
app-kloudle-comand head over toIAM and Admin - Click on
GRANT ACCESSand add the email address of the SA account as a new principal that you want to add to this project. In our casecross-project-sa@kloudle-internal-tools.iam.gserviceaccount.com - Give the principal the permission you want it to have. To be able to read all aspects of the Google Cloud account, a
ViewerandBrowserrole will suffice.
Verifying cross account project access
Once the Service Account has been added to the target project, we can use our VM to now run gcloud commands cross project.
-
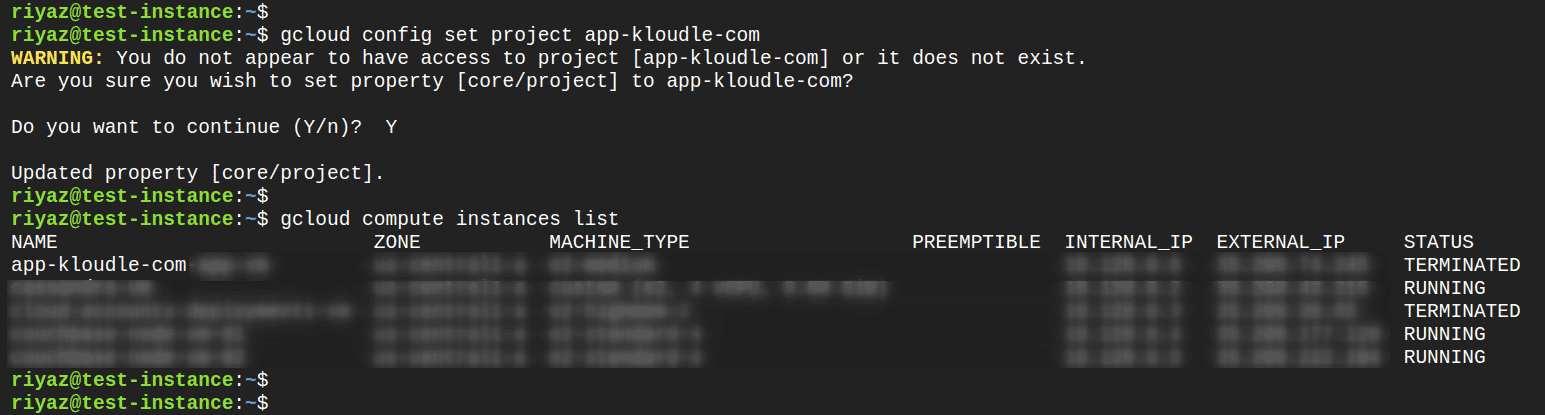
SSH to the VM in
app-kloudle-com -
Set target project for
gcloudusing the following commandsgcloud config set project app-kloudle-com -
Ignore the warning and continue adding the project to the configuration
-
The set up is now ready to access resources from the target project
The access can even be set across projects across a different Google Cloud account as well.
Conclusion
The article shows how you can set up a cross project service account that allows you to manage and read resources across Google Cloud accounts and projects.
***
This article is brought to you by Kloudle Academy, a free e-resource compilation, created and curated by Kloudle. Kloudle is a cloud security platform that uses the power of automation and simplifies human requirements in cloud security. If you wish to give your feedback on this article, you can write to us here.

Riyaz Walikar
Founder & Chief of R&D
Riyaz is the founder and Chief of R&D at Kloudle, where he hunts for cloud misconfigurations so developers don’t have to. With over 15 years of experience breaking into systems, he’s led offensive security at PwC and product security across APAC for Citrix. Riyaz created the Kubernetes security testing methodology at Appsecco, blending frameworks like MITRE ATT&CK, OWASP, and PTES. He’s passionate about teaching people how to hack—and how to stay secure.

Riyaz Walikar
Founder & Chief of R&D
Riyaz is the founder and Chief of R&D at Kloudle, where he hunts for cloud misconfigurations so developers don’t have to. With over 15 years of experience breaking into systems, he’s led offensive security at PwC and product security across APAC for Citrix. Riyaz created the Kubernetes security testing methodology at Appsecco, blending frameworks like MITRE ATT&CK, OWASP, and PTES. He’s passionate about teaching people how to hack—and how to stay secure.