Introduction
AWS Root user has unrestricted access in the account. This user should only be used for those activities that require Root level access, like Billing or adding other AWS accounts to Organisations. For day-to-day activities in the account, users with required permissions must be created.
Having an access key for the Root user becomes a liability and poses the additional risk of being misused or stolen. If an attacker gains access to the root user access keys, they could take over the entire AWS account compromising every single piece of data, access to virtual machines or even the entire operations of the Organisation.
Removing access keys for Root User
Following is the step-by-step guide to remove access keys for a Root User on AWS:
-
Sign in to the AWS management console using the account root user credentials
-
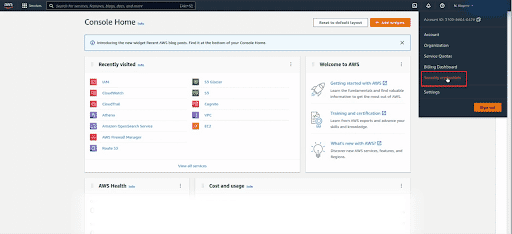
Click on the account name or number in the upper right corner and select Security Credentials from the drop down
-
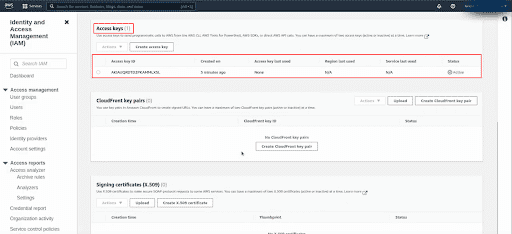
Select the Access Keys section
-
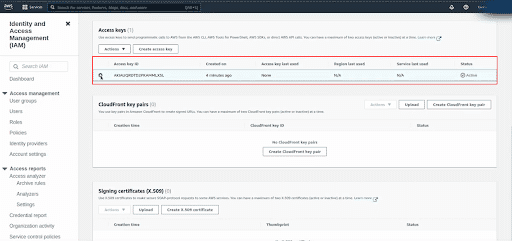
To delete the access key, select the radio button
-
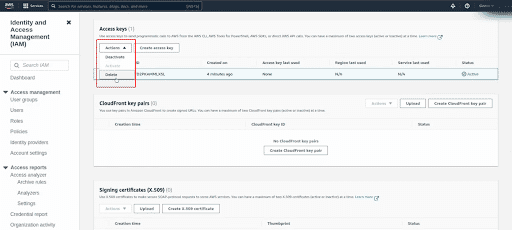
From the Actions dropdown, select Delete
-
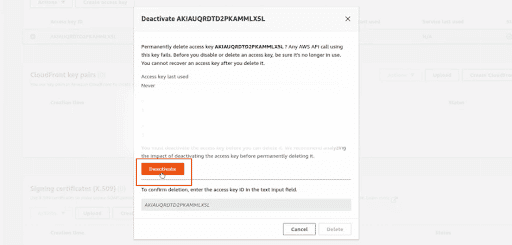
This will display a pop up. Click on Deactivate
-
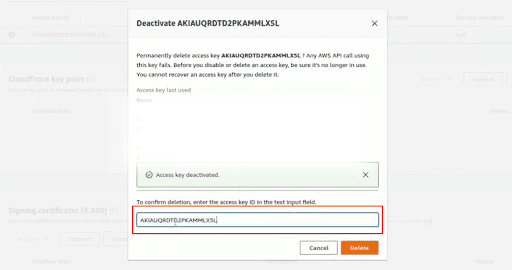
Provide the Access Key ID
-
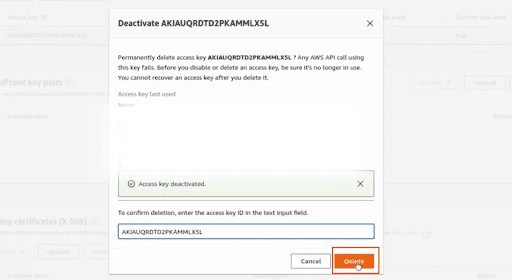
Click on Delete to remove the access key

Riyaz Walikar
Founder & Chief of R&D
Riyaz is the founder and Chief of R&D at Kloudle, where he hunts for cloud misconfigurations so developers don’t have to. With over 15 years of experience breaking into systems, he’s led offensive security at PwC and product security across APAC for Citrix. Riyaz created the Kubernetes security testing methodology at Appsecco, blending frameworks like MITRE ATT&CK, OWASP, and PTES. He’s passionate about teaching people how to hack—and how to stay secure.

Riyaz Walikar
Founder & Chief of R&D
Riyaz is the founder and Chief of R&D at Kloudle, where he hunts for cloud misconfigurations so developers don’t have to. With over 15 years of experience breaking into systems, he’s led offensive security at PwC and product security across APAC for Citrix. Riyaz created the Kubernetes security testing methodology at Appsecco, blending frameworks like MITRE ATT&CK, OWASP, and PTES. He’s passionate about teaching people how to hack—and how to stay secure.