Introduction
In general, the database instances should not have public IP addresses. They should only be accessible to other application components using private IP addresses. In case a database instance must be assigned a public IP address to communicate with remote services or application components, one must ensure that a proper allowlist is applied to the database to accept connections only from trusted /known IP addresses.
A publicly exposed database instance can fall prey to password brute force attacks. Additionally, in the event of unauthorised access to configuration, valid credentials to the database may become accessible to the attackers. This would allow an attacker to connect to the database from an internet located source and completely compromise all data within the database.
In this article we will see how to restrict access to a public Cloud SQL database instance.
Restricting access to public Cloud SQL database instance
This section provides a step by step walkthrough of how we can restrict access to a publicly exposed Cloud SQL database instance.
Following are the steps to restrict access via the Google Cloud console
-
Login to Google Cloud console and navigate to the Cloud SQL Instances page by visiting https://console.cloud.google.com/sql/instances
-
Click the instance name for which you want to restrict public access and then click on Edit to open its Instance info page
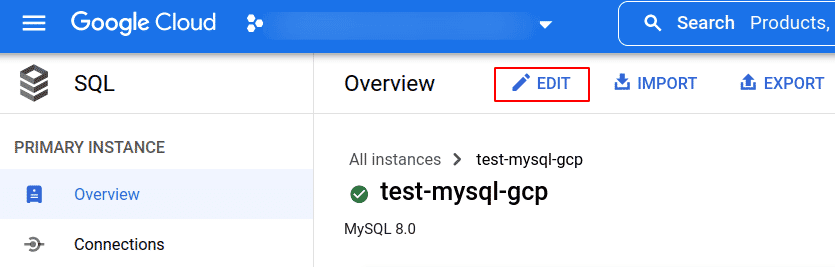
-
Expand the Connections section
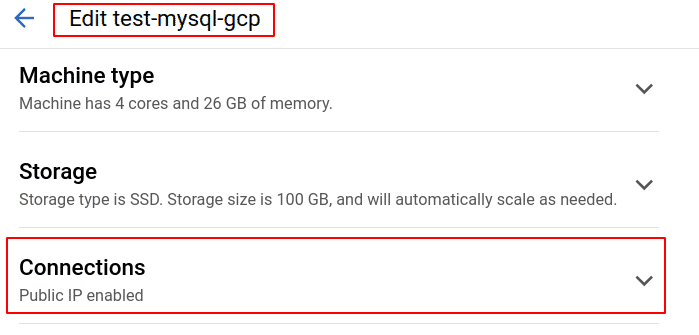
-
Check if any of the authorised networks allow 0.0.0.0/0. If yes, click on delete icon to remove it.
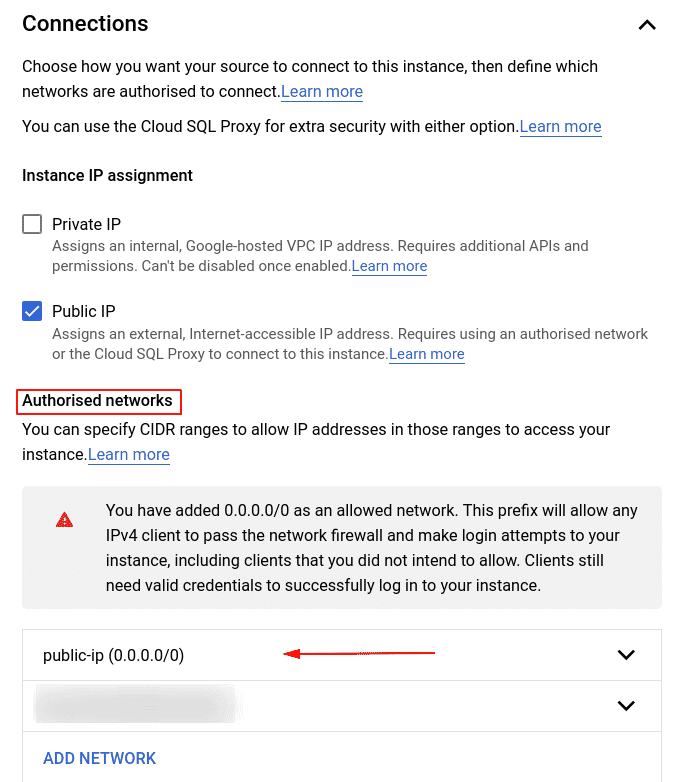
-
Add the trusted/known IP address(s) to which you want to allow access over the internet. Then click Save to update the instance.
Restrict access via the gcloud command line
To update the authorised network list via gcloud, perform the following steps:
-
Run the following command to check if the authorised networks allow public access to everyone on the internet
gcloud sql instances list --format=json -
Update the authorised networks list by running the following command
gcloud sql instances patch INSTANCE_NAME / --authorized-networks=IP_ADDR1,IP_ADDR2...

Riyaz Walikar
Founder & Chief of R&D
Riyaz is the founder and Chief of R&D at Kloudle, where he hunts for cloud misconfigurations so developers don’t have to. With over 15 years of experience breaking into systems, he’s led offensive security at PwC and product security across APAC for Citrix. Riyaz created the Kubernetes security testing methodology at Appsecco, blending frameworks like MITRE ATT&CK, OWASP, and PTES. He’s passionate about teaching people how to hack—and how to stay secure.

Riyaz Walikar
Founder & Chief of R&D
Riyaz is the founder and Chief of R&D at Kloudle, where he hunts for cloud misconfigurations so developers don’t have to. With over 15 years of experience breaking into systems, he’s led offensive security at PwC and product security across APAC for Citrix. Riyaz created the Kubernetes security testing methodology at Appsecco, blending frameworks like MITRE ATT&CK, OWASP, and PTES. He’s passionate about teaching people how to hack—and how to stay secure.