Introduction
AWS RDS allows you to expose database instances to the Internet. This is generally a bad security practice. Exposing the database invites bots that attempt brute force logins creating unnecessary logs and potentially lowering the database’s performance. As a security best practice, RDS should only be exposed internally via its VPC and security group only to the instances that need to communicate with the database.
Unless there is a specific business requirement, RDS instances should not have a public endpoint and should be accessed from within a VPC only.
In this article we will go through the steps to restrict access to your publicly accessible RDS Instance.
Steps to restrict public access to RDS Instance
Using AWS console
-
Login to the AWS account.
-
Navigate to RDS and select the RDS instance that you want to update. Click on the Modify button.
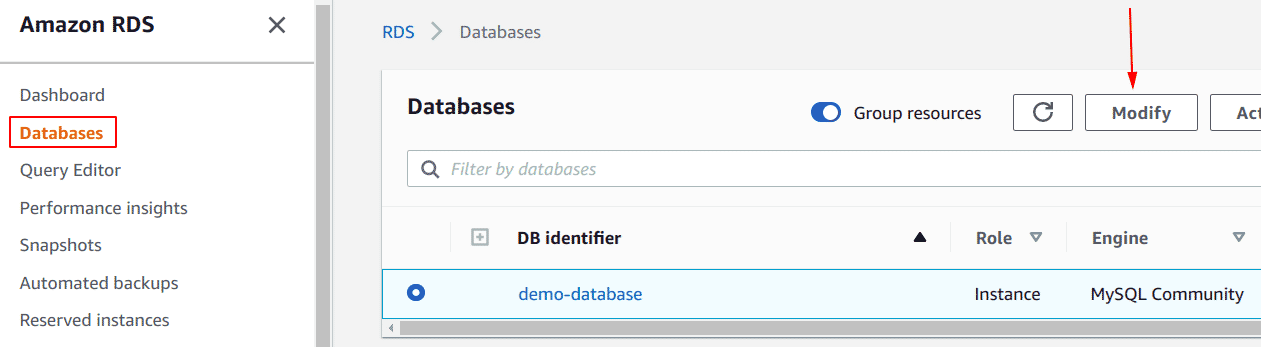
-
On the Modify DB Instance page, In Connectivity section, under Additional configuration, select Not publicly accessible to restrict public access.
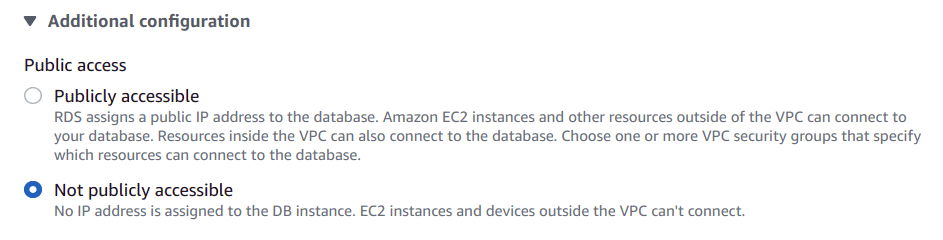
-
Click Continue and at the bottom of the next page, check Apply Immediately.
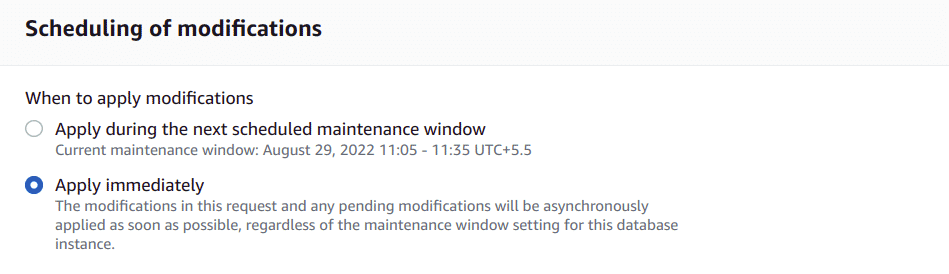
-
Click Modify DB Instance. Once the configuration changes are applied.
-
Click on the Instance name and Summarypage will open with all the details.
-
Under the Connectivity & Security section in the bottom panel, click on the active VPC security groups name to select it for editing.
-
On the VPC Security Groups page, select the Inbound rules tab from the bottom panel and click the Edit inbound rules button to edit the selected security group ingress rules.
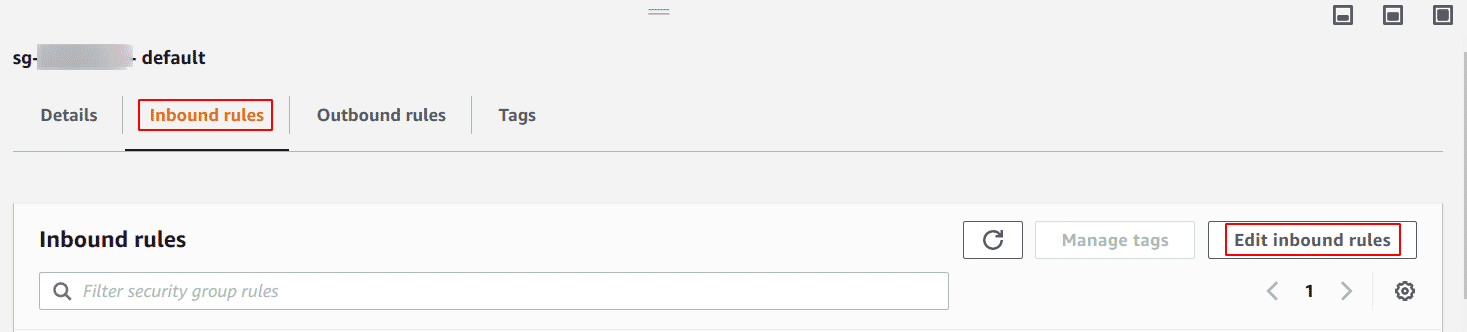
-
In the Edit inbound rules dialog box, identify any inbound rules which have set the Source to Anywhere (0.0.0.0/0) and update them by using one of the following actions:
- To grant access to a certain IP address
- Select Custom IP from the Source dropdown list.
- Enter the IP address CIDR that you want to authorize in the Source field.
- Click the Save button to save the changes.
- To grant access to an EC2 Security Group
- Select Custom IP from the Source dropdown list.
- Enter the EC2 security group ID that you want to authorize in the Source field.
- Click the Save button to save the changes.
- To grant access to a certain IP address
Using AWS CLI
-
To list all RDS database names in a particular region
aws rds describe-db-instances --region <region> -
To modify the selected RDS instance connection configuration.
aws rds modify-db-instance --region <region> --db-instance-identifier <name of db> --no-publicly-accessible --apply-immediately -
To fetch the VPC security group ID associated with the instance:
aws rds describe-db-instances --region <region> --db-instance-identifier <name of db> --query 'DBInstances[*].VpcSecurityGroups' -
To revoke the VPC security group inbound rule with the CIDR set to 0.0.0.0/0 that grants access to everyone
aws ec2 revoke-security-group-ingress --region <region> --group-id <value> --protocol <value> --port <value> --cidr 0.0.0.0/0 -
To authorize custom access based on IP/CIDR to the instances associated with the selected VPC security group
aws ec2 authorize-security-group-ingress --region <value> --group-id <value> --protocol <value> --port <value> --cidr <value> -
To authorize custom access based on existing EC2 security groups
aws ec2 authorize-security-group-ingress --region <value> --group-id <value> --protocol <value> --port 3<value> --source-group <value>
Conclusion
An Internet exposed RDS can fall prey to password brute force attacks. Additionally, in the event of unauthorized access to configuration, valid credentials to the DB may become accessible. This would allow an attacker to connect to the DB from an Internet located source and completely compromise all data within the database. In general, databases are used for storing data that is not required to be openly accessible to the world, hence, as a security best practice, one must restrict access to their database to only allow connections from required instances.

Riyaz Walikar
Founder & Chief of R&D
Riyaz is the founder and Chief of R&D at Kloudle, where he hunts for cloud misconfigurations so developers don’t have to. With over 15 years of experience breaking into systems, he’s led offensive security at PwC and product security across APAC for Citrix. Riyaz created the Kubernetes security testing methodology at Appsecco, blending frameworks like MITRE ATT&CK, OWASP, and PTES. He’s passionate about teaching people how to hack—and how to stay secure.

Riyaz Walikar
Founder & Chief of R&D
Riyaz is the founder and Chief of R&D at Kloudle, where he hunts for cloud misconfigurations so developers don’t have to. With over 15 years of experience breaking into systems, he’s led offensive security at PwC and product security across APAC for Citrix. Riyaz created the Kubernetes security testing methodology at Appsecco, blending frameworks like MITRE ATT&CK, OWASP, and PTES. He’s passionate about teaching people how to hack—and how to stay secure.