Introduction
IAM Access key rotation is a healthy security practice as it ensures that any keys that may have been leaked either due to a reuse, or breach, or inadvertently by the user, become irrelevant. The AWS CIS Foundations Benchmark also flags a user whose key has not been rotated in the last 90 days as non-compliant. It is recommended to ensure safe usage of Access keys and to follow security hygiene like not hardcoding the key in code, not sharing the key over email, etc.
In this article, we will go through the steps required to rotate an Access key for a user in AWS.
Note: Before rotating an Access key make sure you know and have access to all the places where the Access key is being used currently so that you can ensure that no applications or access is broken due to key rotation.
Rotate the Access key for an IAM user
Following are the steps to rotate the Access key for an IAM user in AWS:
-
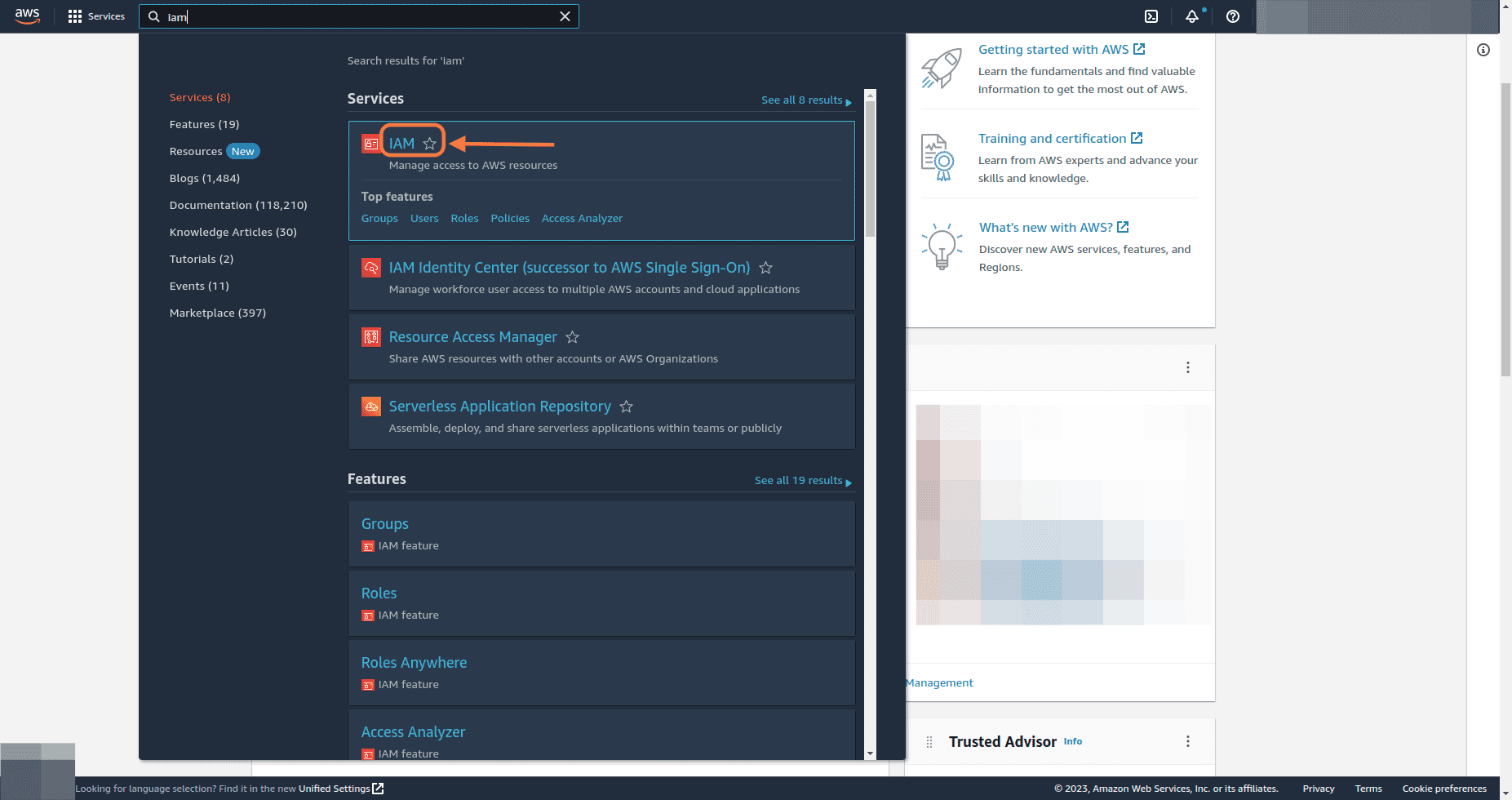
Login to AWS Management Console and navigate to IAM service
-
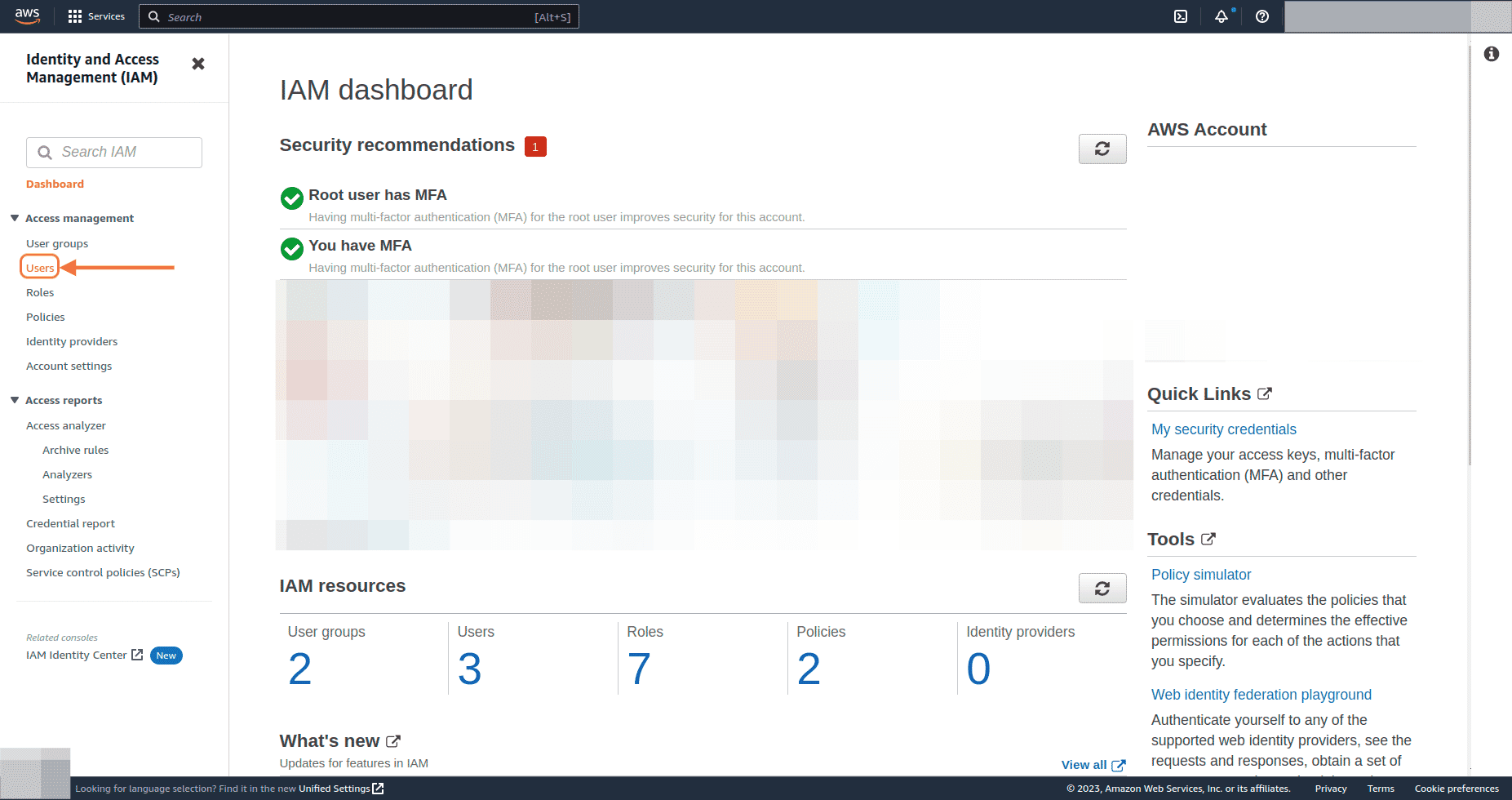
Under Access management on IAM dashboard, go to Users
-
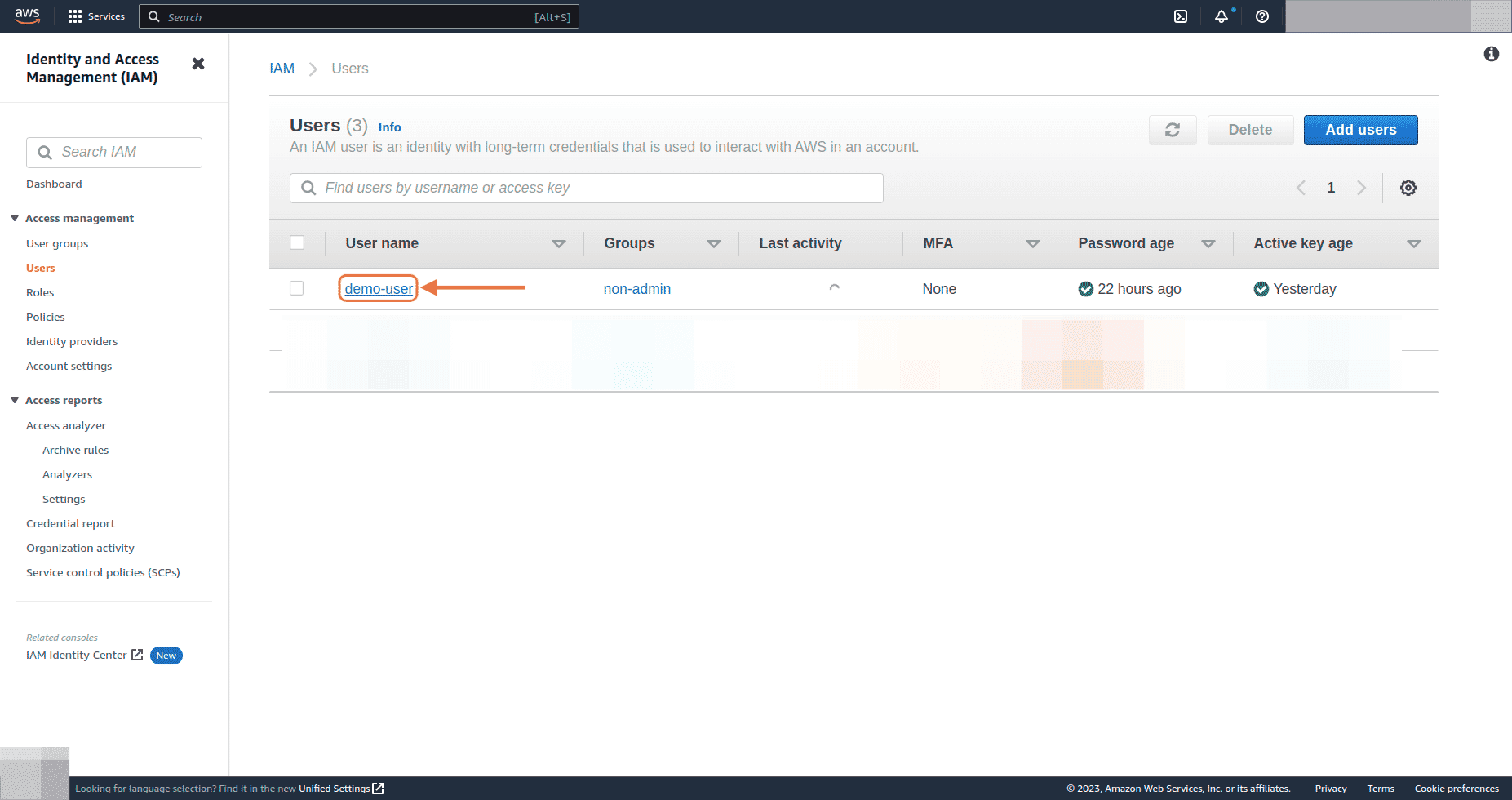
Select the user from the list for whom you want to rotate the Access key
-
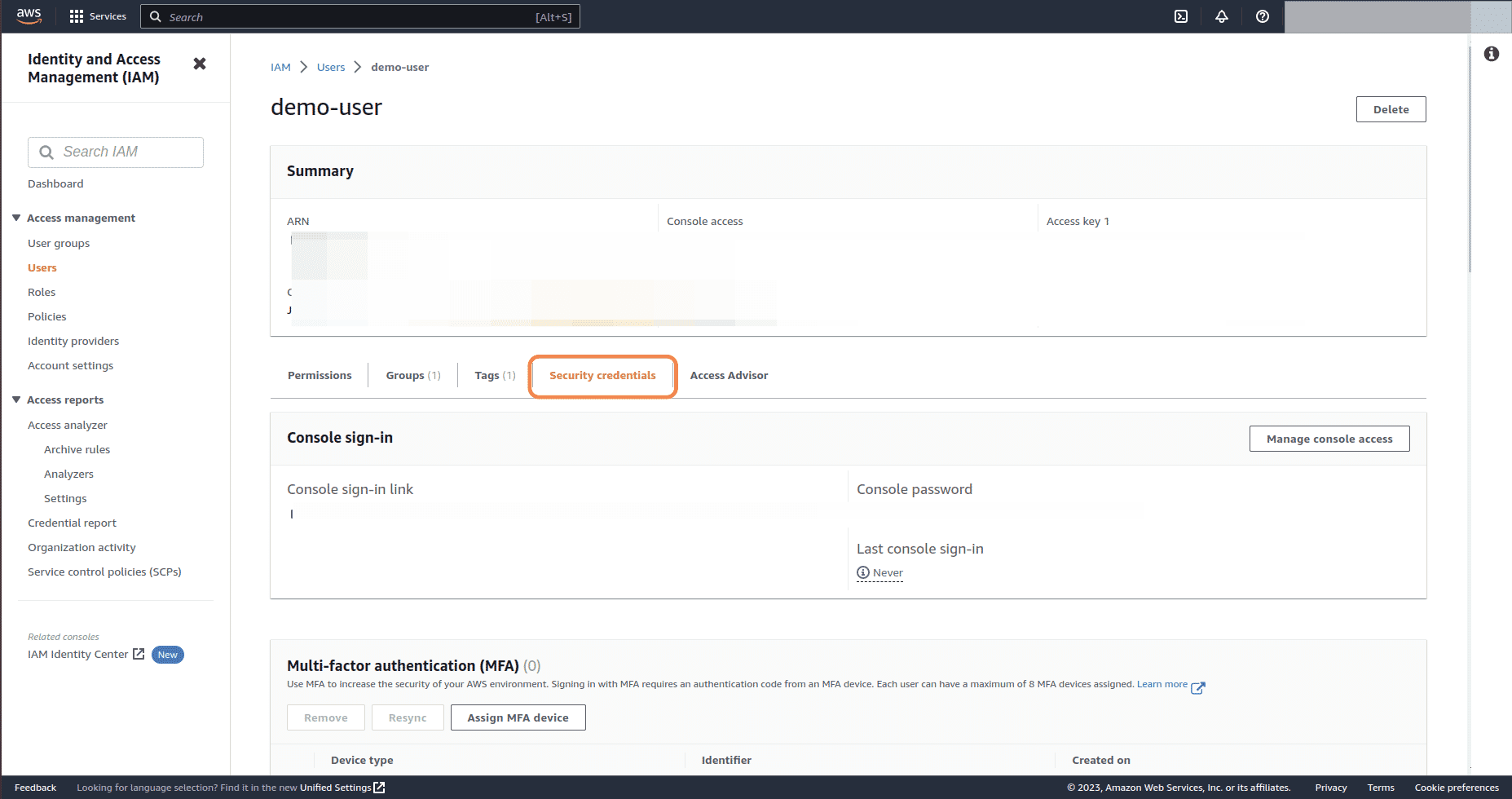
On Summary page, click on Security credentials tab
-
Under Access keys section, we can see the access keys and their status for the user
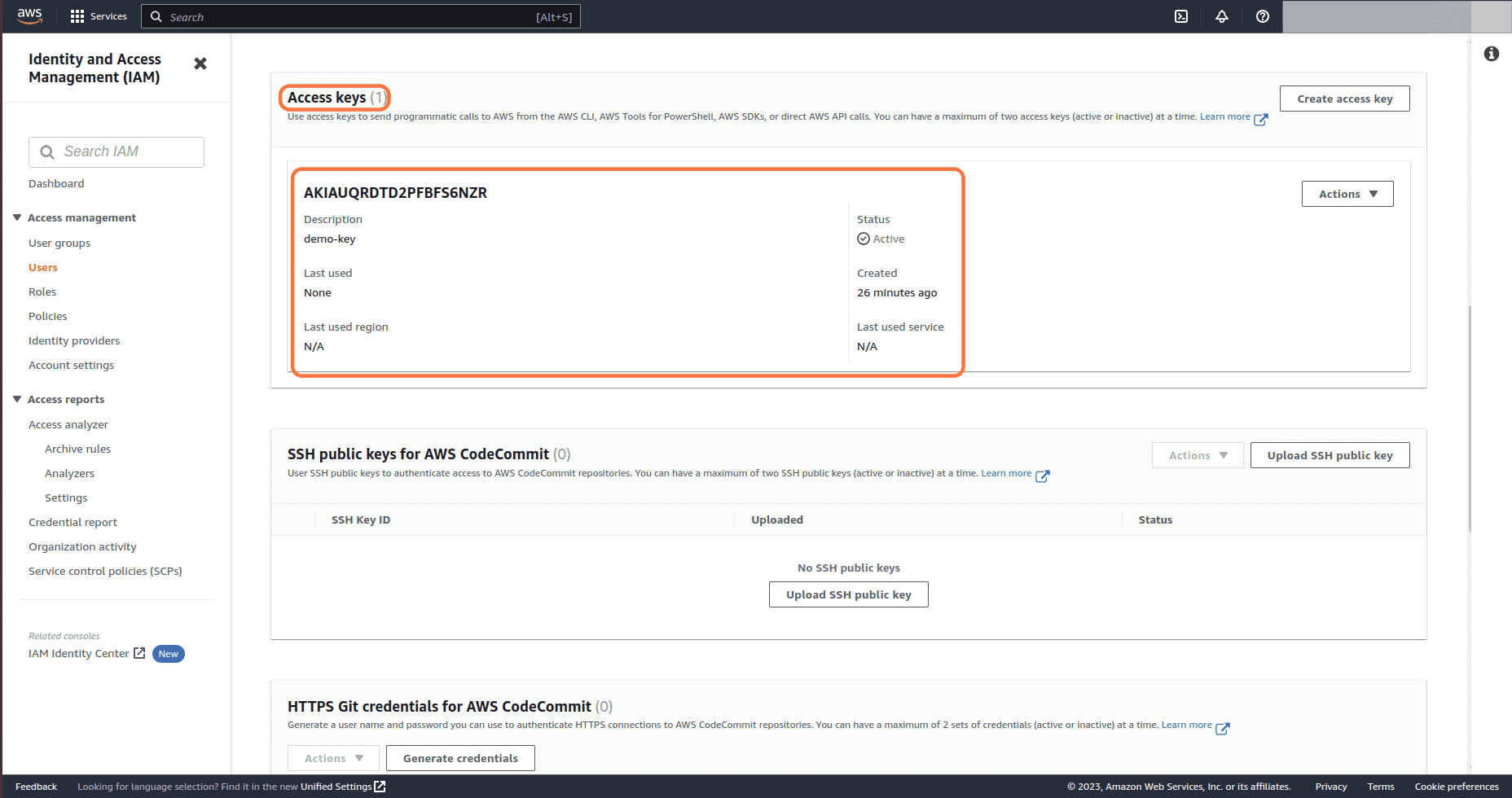
-
Click on Create access key to create a new access key for the user
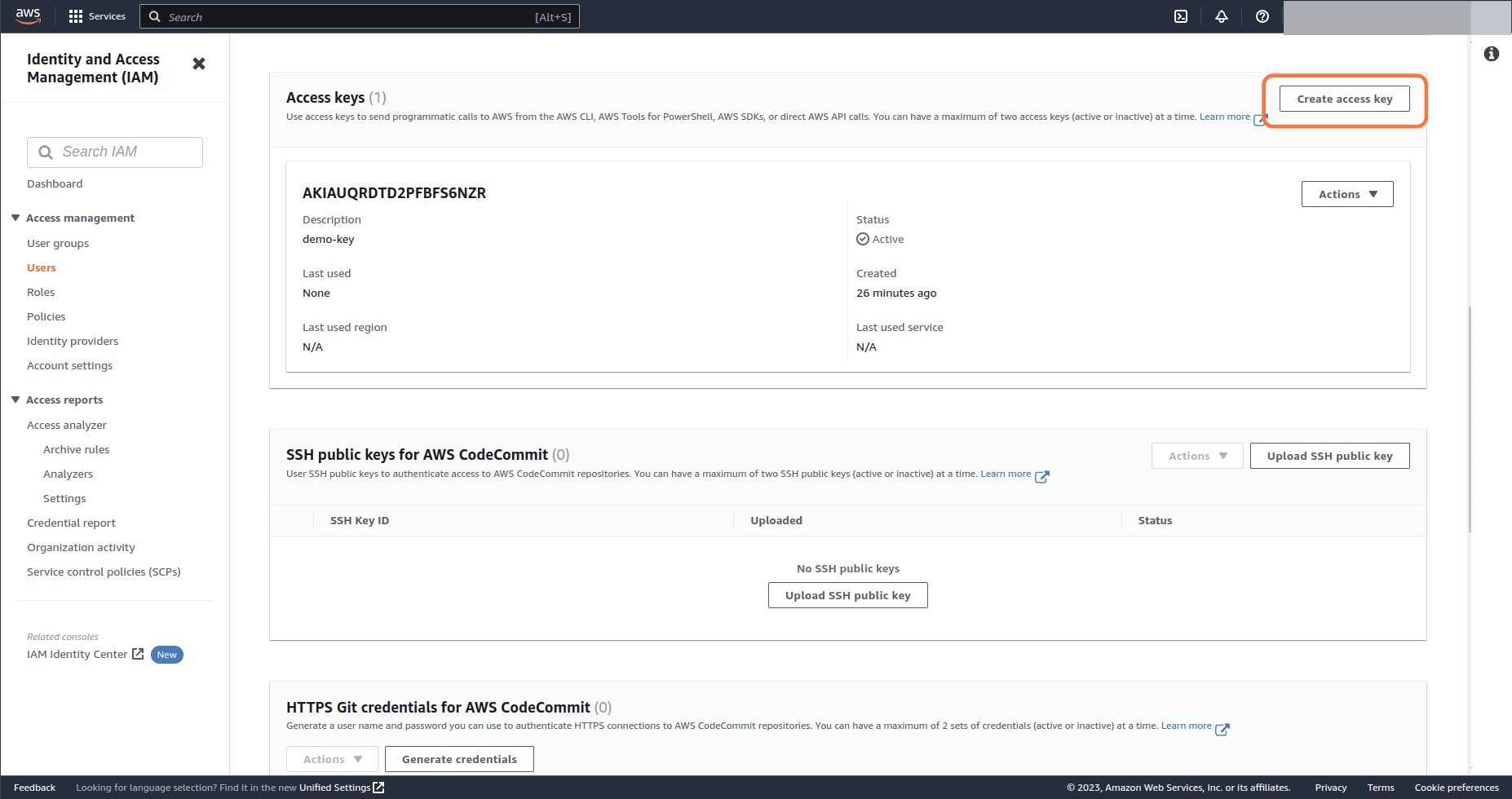
-
Select the appropriate option under Access key best practices and alternatives and click on Next button
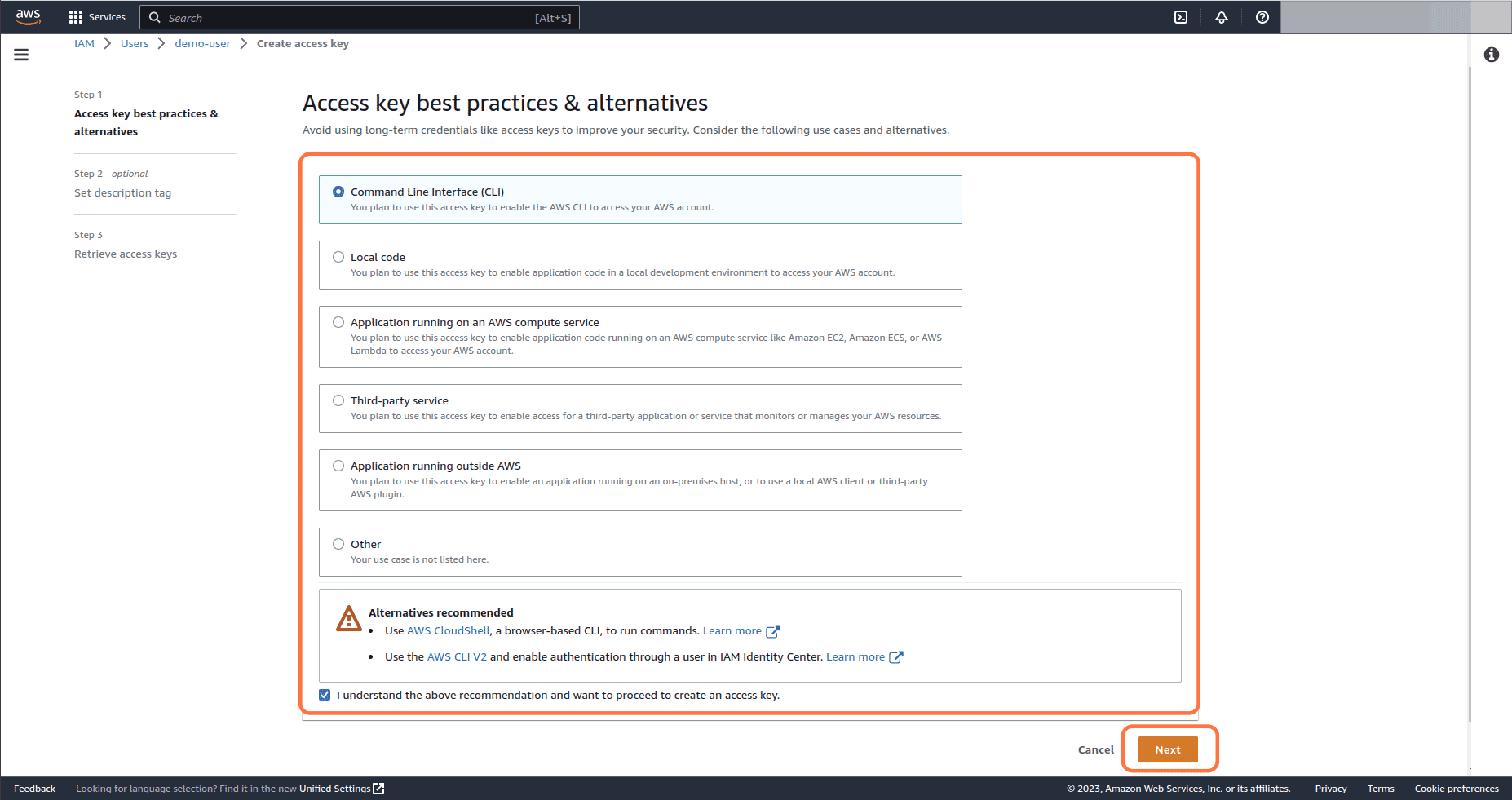
-
Set a description tag for the new access key and click on Create access key button
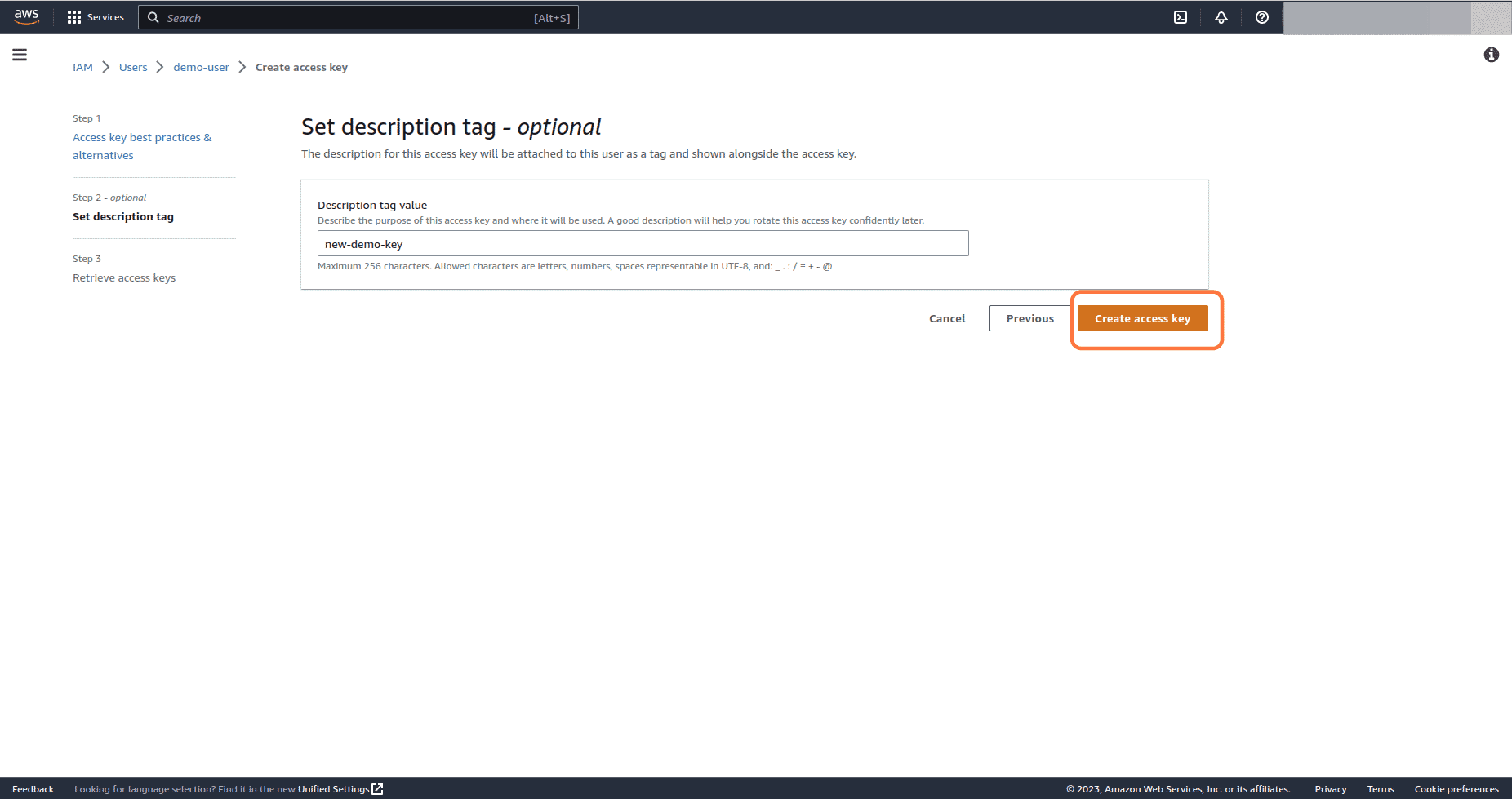
-
Note down the Access key ID and Secret access key or Download csv file and keep it in a secure place. Click on Done button
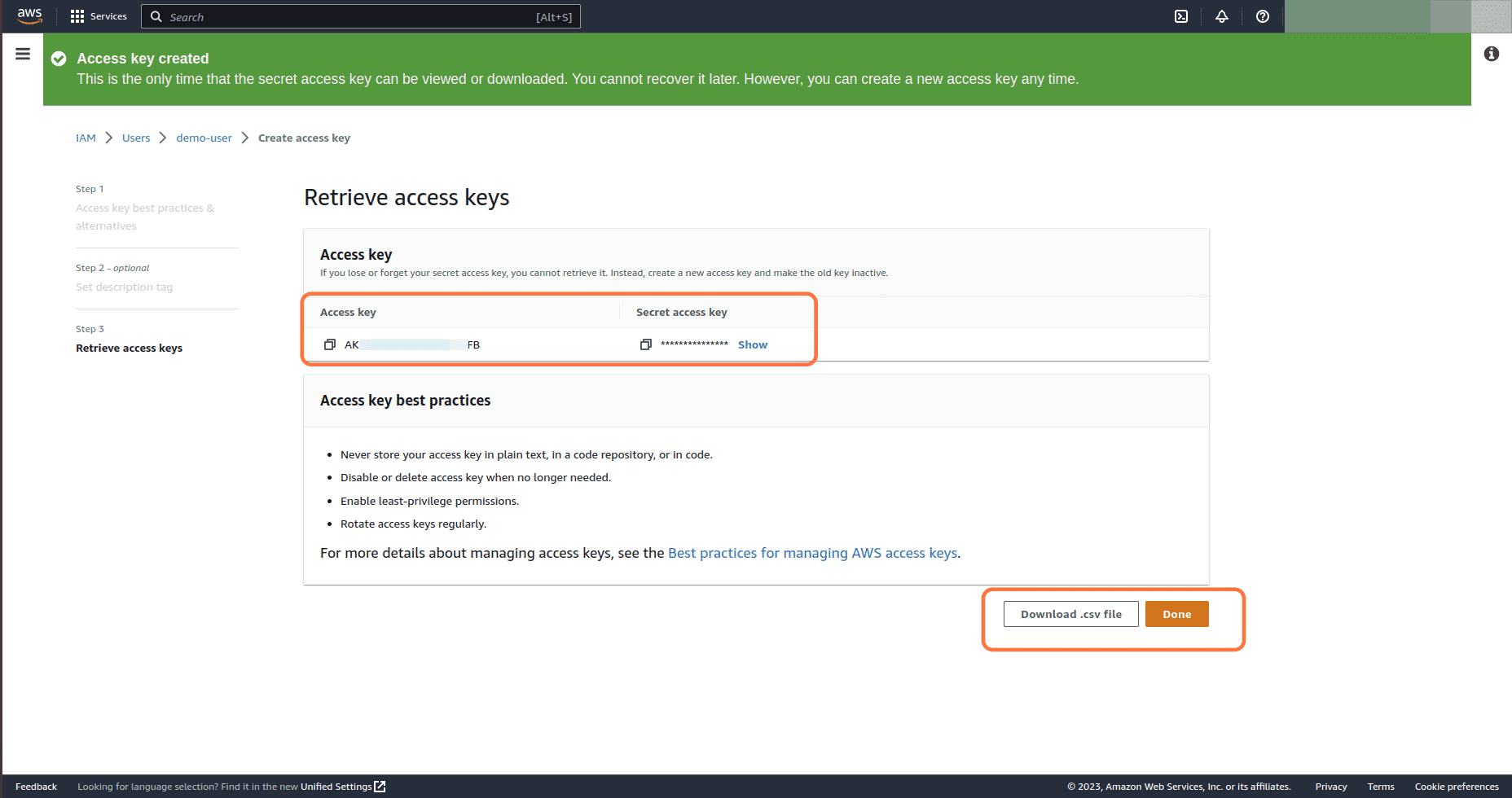
-
Update the new Access key in place of the older one wherever the old Access key is being used. Make sure the new Access key is working in all those places
-
Now deactivate the old Access key. Click on Actions dropdown button and select Deactivate
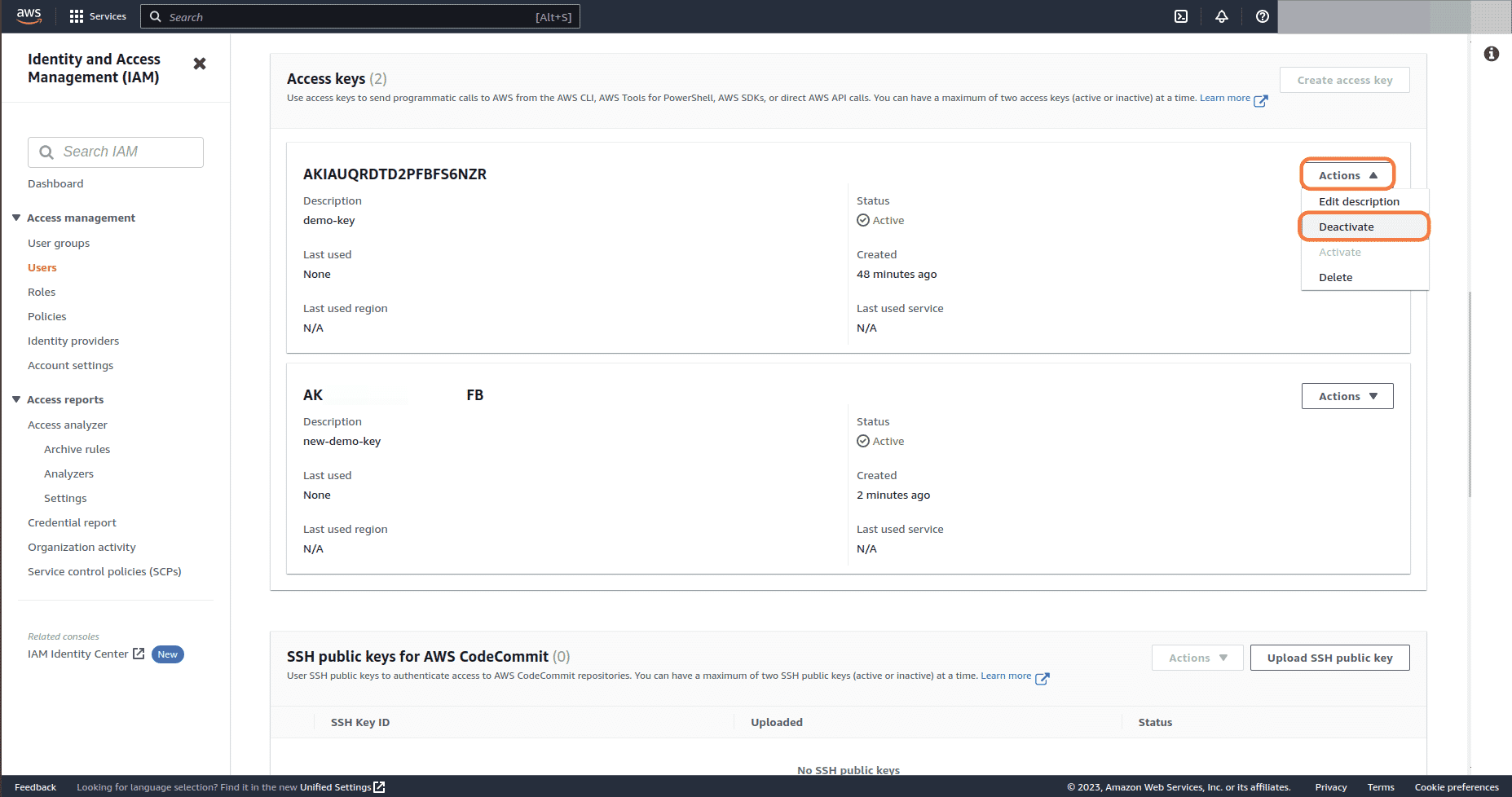
-
Click on Deactivate button
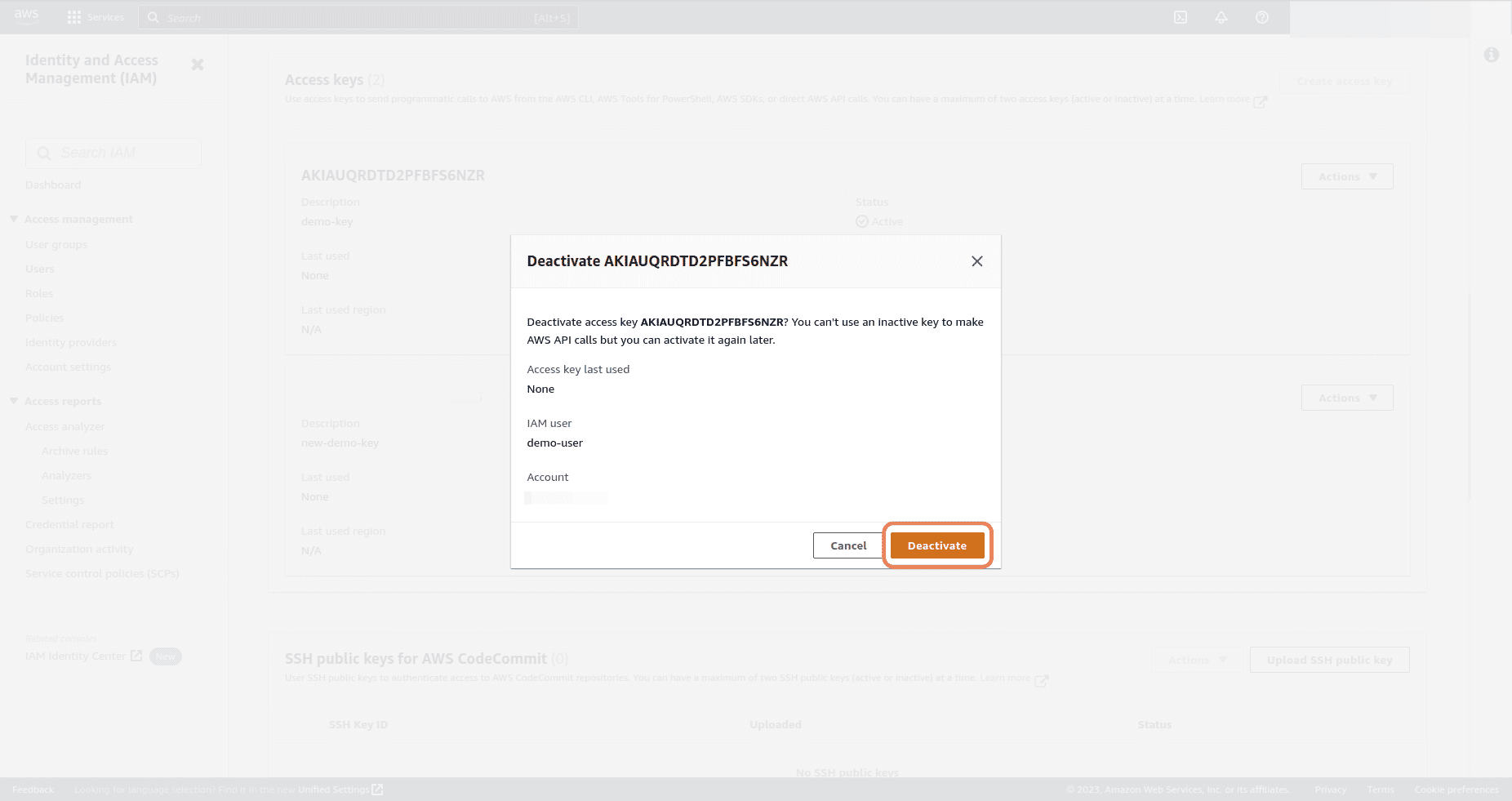
-
Once the old key has been deactivated, make sure that all your access is working as expected after adding the new key in its place and that you have not missed out any place to update the new key
-
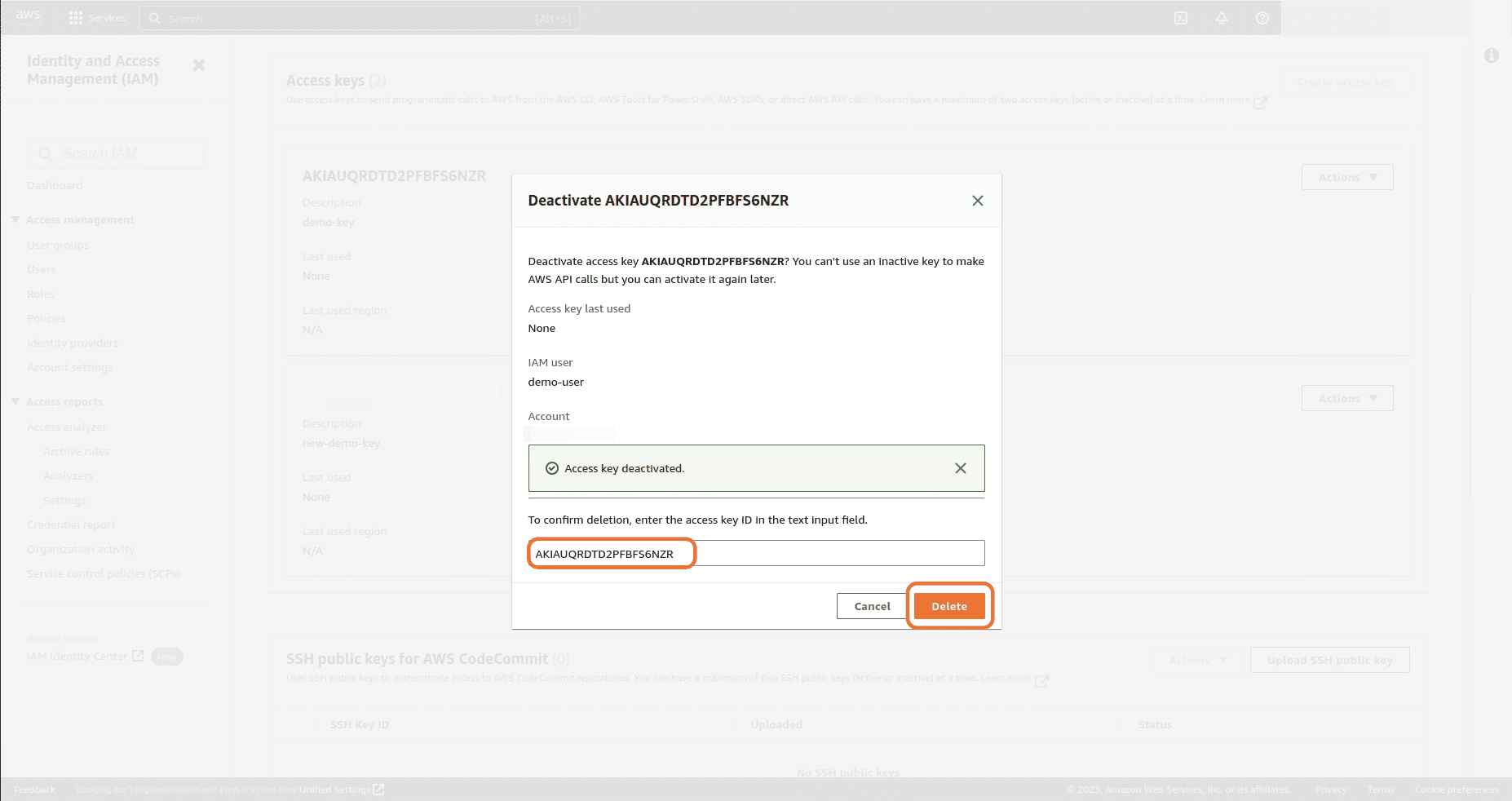
If all the access is working as expected with the new key, we can now delete the old Access key. Click on Actions dropdown button for the old Access key and select Delete
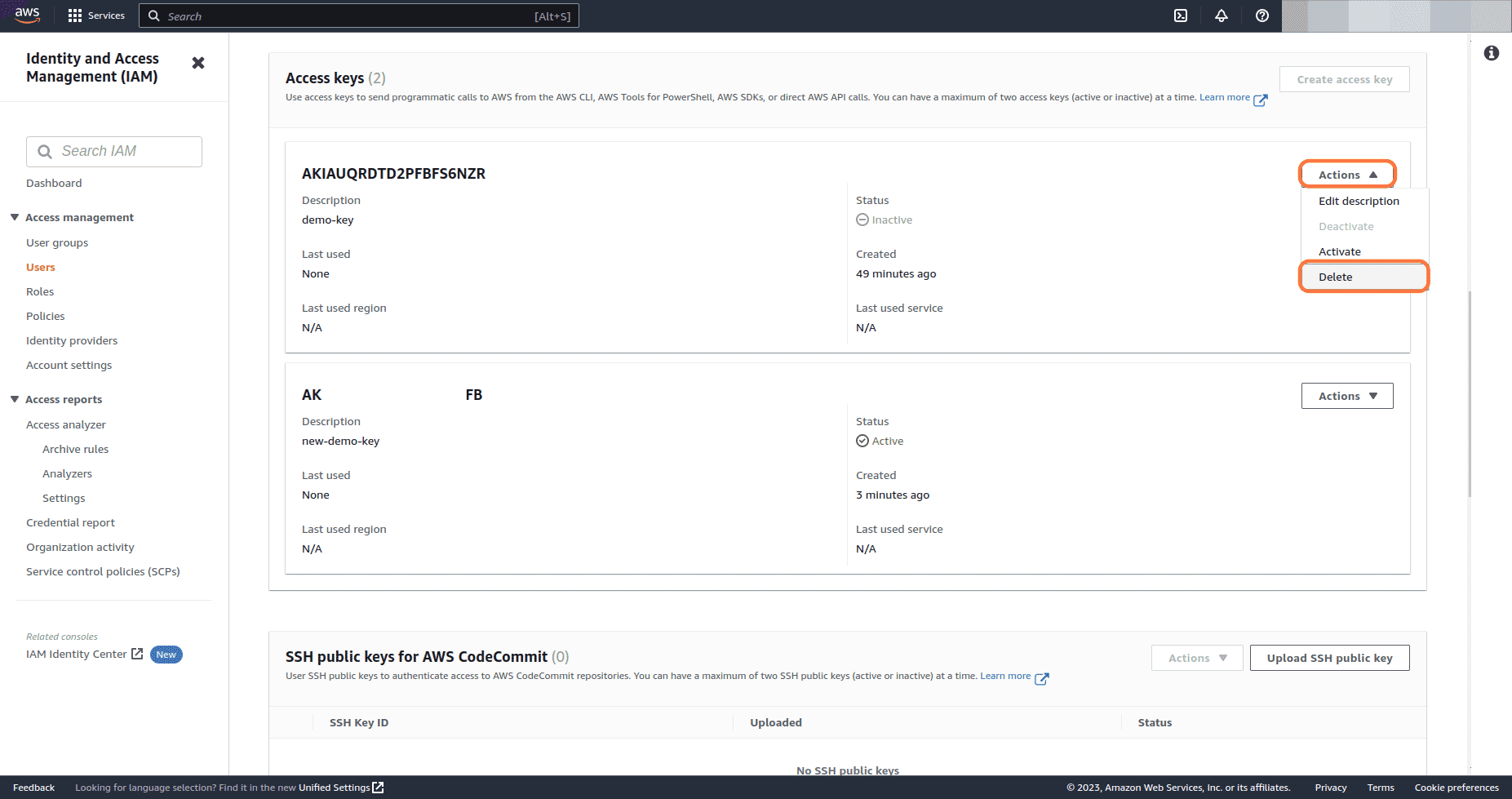
-
Provide the Access key ID of the old key and click on Delete button
-
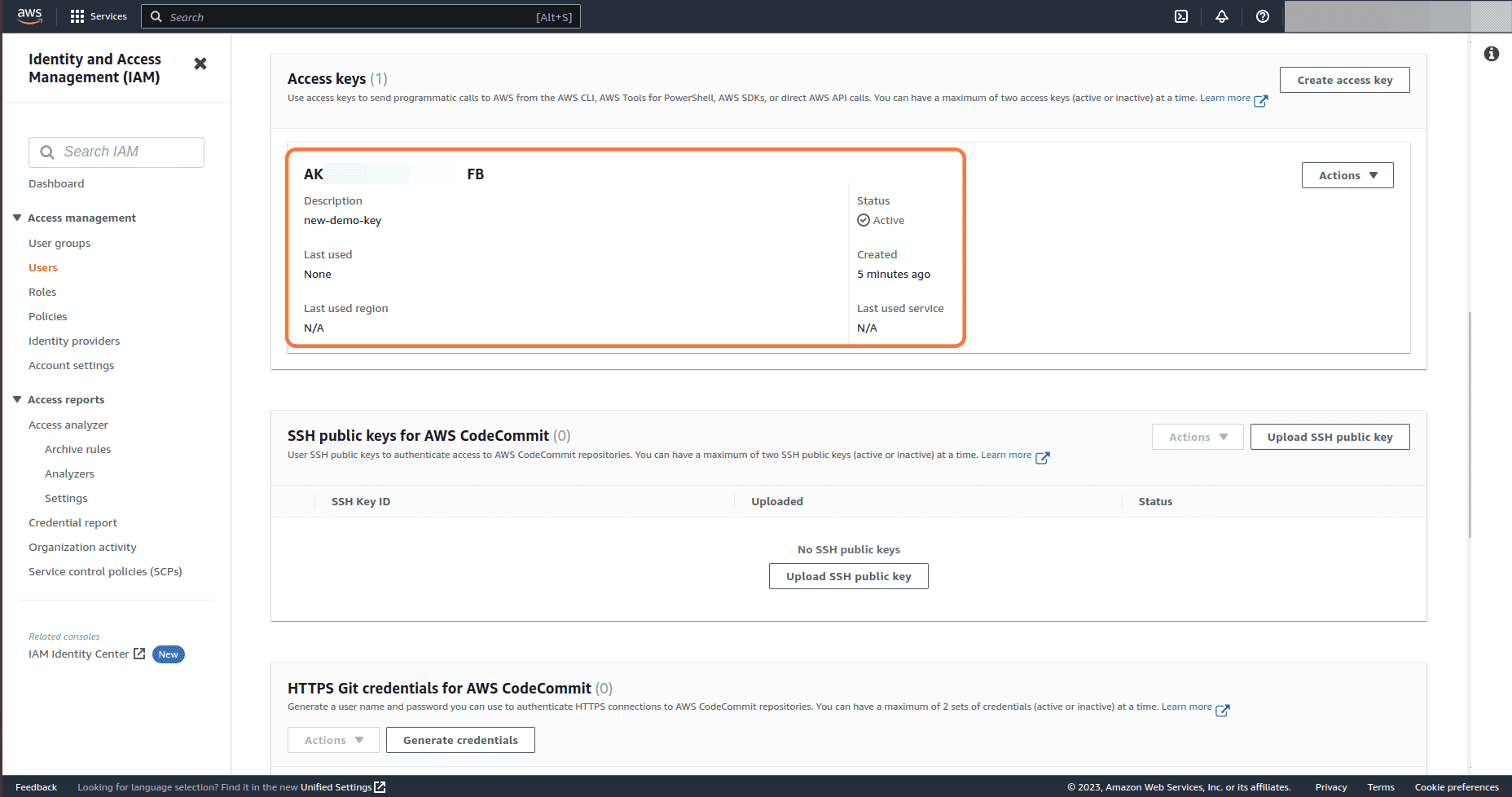
The old Access key is now deleted and we can only see the newly created access key

Riyaz Walikar
Founder & Chief of R&D
Riyaz is the founder and Chief of R&D at Kloudle, where he hunts for cloud misconfigurations so developers don’t have to. With over 15 years of experience breaking into systems, he’s led offensive security at PwC and product security across APAC for Citrix. Riyaz created the Kubernetes security testing methodology at Appsecco, blending frameworks like MITRE ATT&CK, OWASP, and PTES. He’s passionate about teaching people how to hack—and how to stay secure.

Riyaz Walikar
Founder & Chief of R&D
Riyaz is the founder and Chief of R&D at Kloudle, where he hunts for cloud misconfigurations so developers don’t have to. With over 15 years of experience breaking into systems, he’s led offensive security at PwC and product security across APAC for Citrix. Riyaz created the Kubernetes security testing methodology at Appsecco, blending frameworks like MITRE ATT&CK, OWASP, and PTES. He’s passionate about teaching people how to hack—and how to stay secure.