Introduction
Linux terminal can be used to manage and interact with AWS resources apart from the AWS console. In this article we will see how setup AWS CLI and also configuration of AWS CLI. AWS CLI is an essential tool to automate and interact with AWS services.
Steps to install the AWS CLI
Step 1 - Sign up into your AWS account
Step 2 - Navigate to IAM and create an IAM user account
Step 3 - Create an access key ID and secret access key for the user
Step 4 - After creating an AWS account, IAM credentials, and an IAM access key pair, to use the AWS CLI. Install the latest release of the AWS CLI version 2.
curl "https://awscli.amazonaws.com/awscli-exe-linux-x86_64.zip" -o "awscliv2.zip"
unzip awscliv2.zip
sudo ./aws/install
Below are the ways to configure AWS CLI on linux
- Configure AWS CLI using aws configure
The aws configure command is used to set up your AWS CLI installation by providing below details
- Access key ID
- Secret access key
- AWS Region
- Output format
AWS CLI stores the above provided information’s as profile which will be named as default or you can specify your own profile name as aws configure --profile <name>
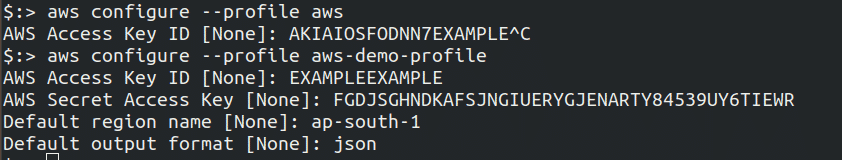
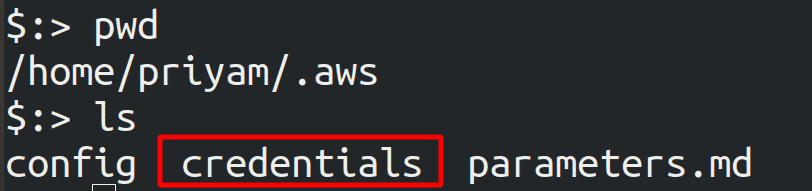
Configuration swttings are stored in a local file named credentials in the folder named as .aws in the home directory
How to switch between multiple profiles?
To run the commands for a particular profile you need to switch to that particular profile. For example there are two profiles as aws-account-profile1 and aws-account-profile2. Then run the below command to switch for profiles.
export AWS_PROFILE=<profile-name>
- To configure the AWS CLI using Environment variables
Export the below environment variables in the terminal.
export AWS_ACCESS_KEY_ID=AKIAIOSFODNN7EXAMPLE
export AWS_SECRET_ACCESS_KEY=erjwrXUtnerjw/K7MDENG/bPxRfiCYEXAMPLEKEY
export AWS_DEFAULT_REGION=us-west-2
If you specify an option by using the environment variables mentioned above, it overrides any value loaded from a profile in the configuration file.

Riyaz Walikar
Founder & Chief of R&D
Riyaz is the founder and Chief of R&D at Kloudle, where he hunts for cloud misconfigurations so developers don’t have to. With over 15 years of experience breaking into systems, he’s led offensive security at PwC and product security across APAC for Citrix. Riyaz created the Kubernetes security testing methodology at Appsecco, blending frameworks like MITRE ATT&CK, OWASP, and PTES. He’s passionate about teaching people how to hack—and how to stay secure.

Riyaz Walikar
Founder & Chief of R&D
Riyaz is the founder and Chief of R&D at Kloudle, where he hunts for cloud misconfigurations so developers don’t have to. With over 15 years of experience breaking into systems, he’s led offensive security at PwC and product security across APAC for Citrix. Riyaz created the Kubernetes security testing methodology at Appsecco, blending frameworks like MITRE ATT&CK, OWASP, and PTES. He’s passionate about teaching people how to hack—and how to stay secure.