Introduction
For validating the secure configuration of Amazon Web Services against CIS Amazon Web Services Foundations Benchmark Version 1.2.0 we run the Inspec profile.
Once the scan is done it will list the misconfigurations present in the AWS account and the check is from Amazon CIS benchmark.
Steps to setup the AWS foundations CIS baseline tool
Prerequisites
-
Install the latest version of InsPec and supporting Ruby language component.
-
Install the latest version of AWS Command Line Interface (CLI).
-
At least AWS IAM “ReadOnlyAccess” Managed Policy should be attached to the IAM account user used to run this profile against the AWS environment.
Steps of configuring credentials in the CLI
- AWS CLI environment should have the right environment variables set. The variables required are your AWS region, access key, secret access key and session token to use the AWS CLI and InSpec resources in the AWS environment.
If MFA is enabled then we need to fetch the session token using the below command
aws sts get-session-token \
--duration-seconds 900 \
--serial-number <YourMFADeviceSerialNumber> \
--token-code <6 digit token value>
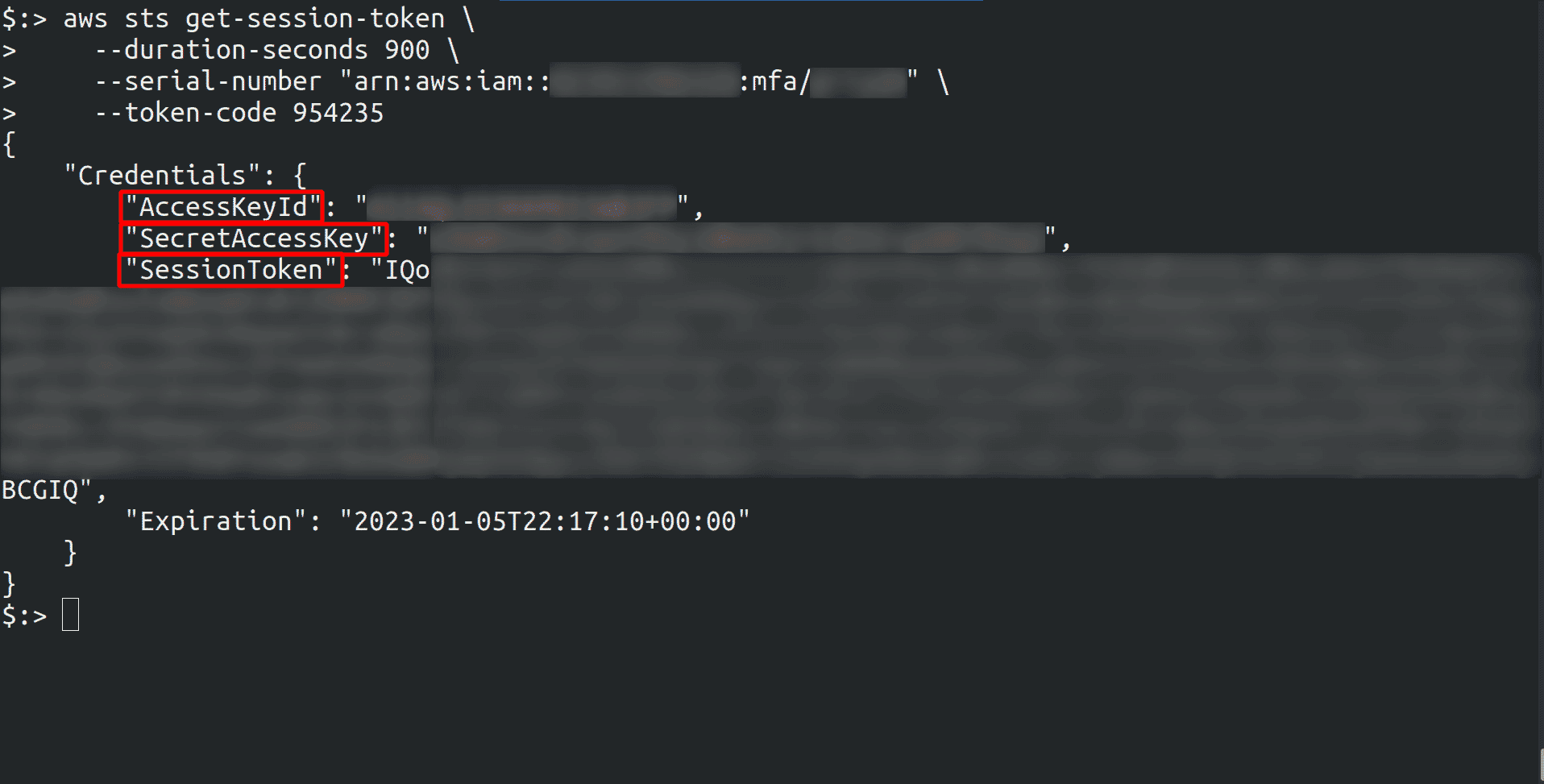
Once you have got the value then export it to the environment variables as below:
export AWS_ACCESS_KEY_ID=<access-key generated by above command>
export AWS_SECRET_ACCESS_KEY=<secret-access-key generated by above command>
export AWS_SESSION_TOKEN=<session_token generated by above command>
export AWS_REGION=<region>
Steps to run the scan
Running this Baseline from a local Archive copy
mkdir profiles
cd profiles
git clone https://github.com/mitre/aws-foundations-cis-baseline
inspec archive aws-foundations-cis-baseline
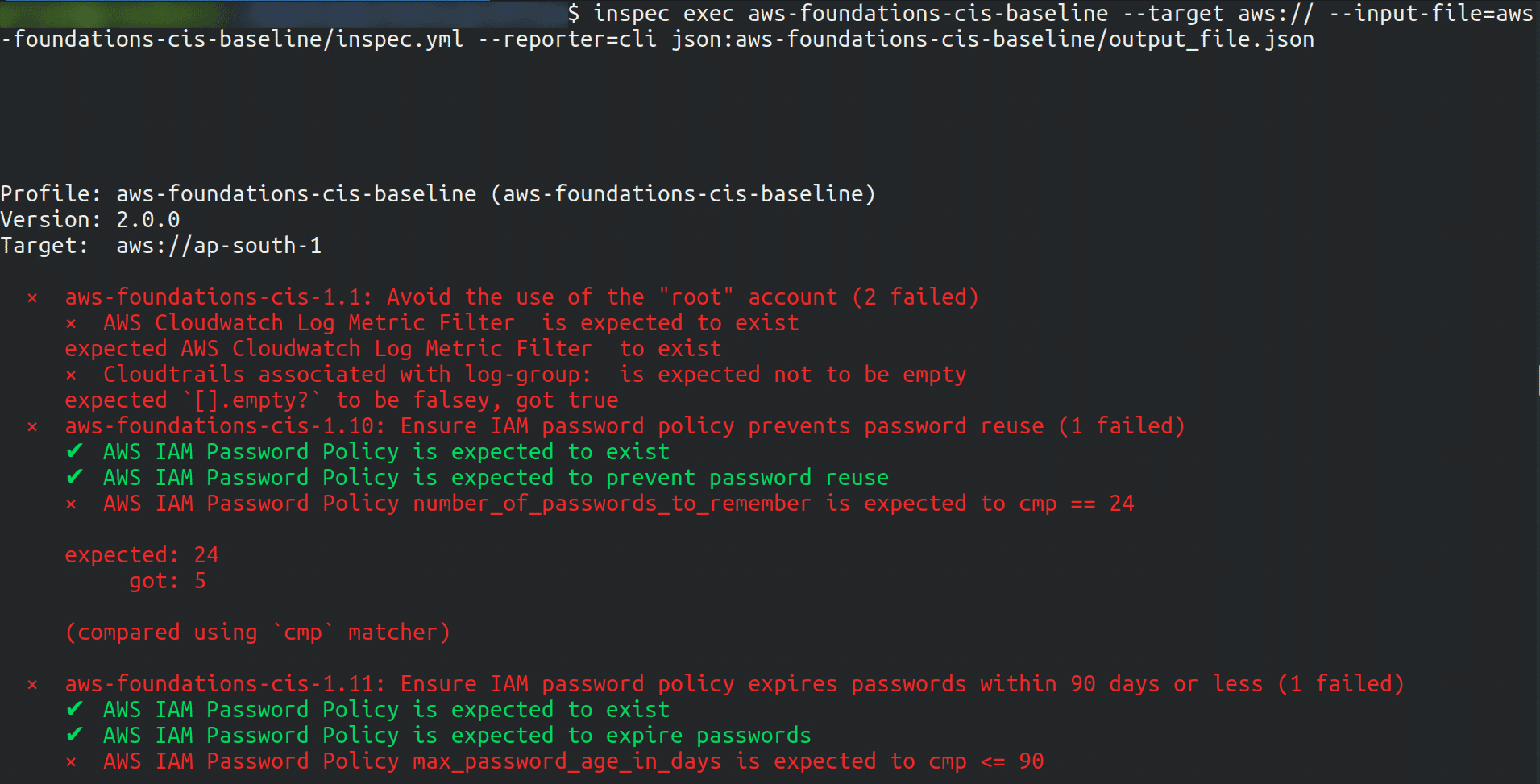
inspec exec <name of generated archive> --target aws:// --input-file=<path_to_your_inputs_file/name_of_your_inputs_file.yml> --reporter=cli json:<path_to_your_output_file/name_of_your_output_file.json>

Riyaz Walikar
Founder & Chief of R&D
Riyaz is the founder and Chief of R&D at Kloudle, where he hunts for cloud misconfigurations so developers don’t have to. With over 15 years of experience breaking into systems, he’s led offensive security at PwC and product security across APAC for Citrix. Riyaz created the Kubernetes security testing methodology at Appsecco, blending frameworks like MITRE ATT&CK, OWASP, and PTES. He’s passionate about teaching people how to hack—and how to stay secure.

Riyaz Walikar
Founder & Chief of R&D
Riyaz is the founder and Chief of R&D at Kloudle, where he hunts for cloud misconfigurations so developers don’t have to. With over 15 years of experience breaking into systems, he’s led offensive security at PwC and product security across APAC for Citrix. Riyaz created the Kubernetes security testing methodology at Appsecco, blending frameworks like MITRE ATT&CK, OWASP, and PTES. He’s passionate about teaching people how to hack—and how to stay secure.