Introduction
This tool is created to help the users to assess their security posture on the Google Cloud against the CIS Benchmark. In this article we will go through the steps to setup AWS Inspec tool using Cloud Shell and Using the CLI in detail.
Using Cloud Shell
Go to the Cloud Shell and clone the inspec repohttps://console.cloud.google.com/cloudshell/open?git_repo=https://github.com/GoogleCloudPlatform/inspec-gcp-cis-benchmark&page=editor&tutorial=walkthrough.md
-
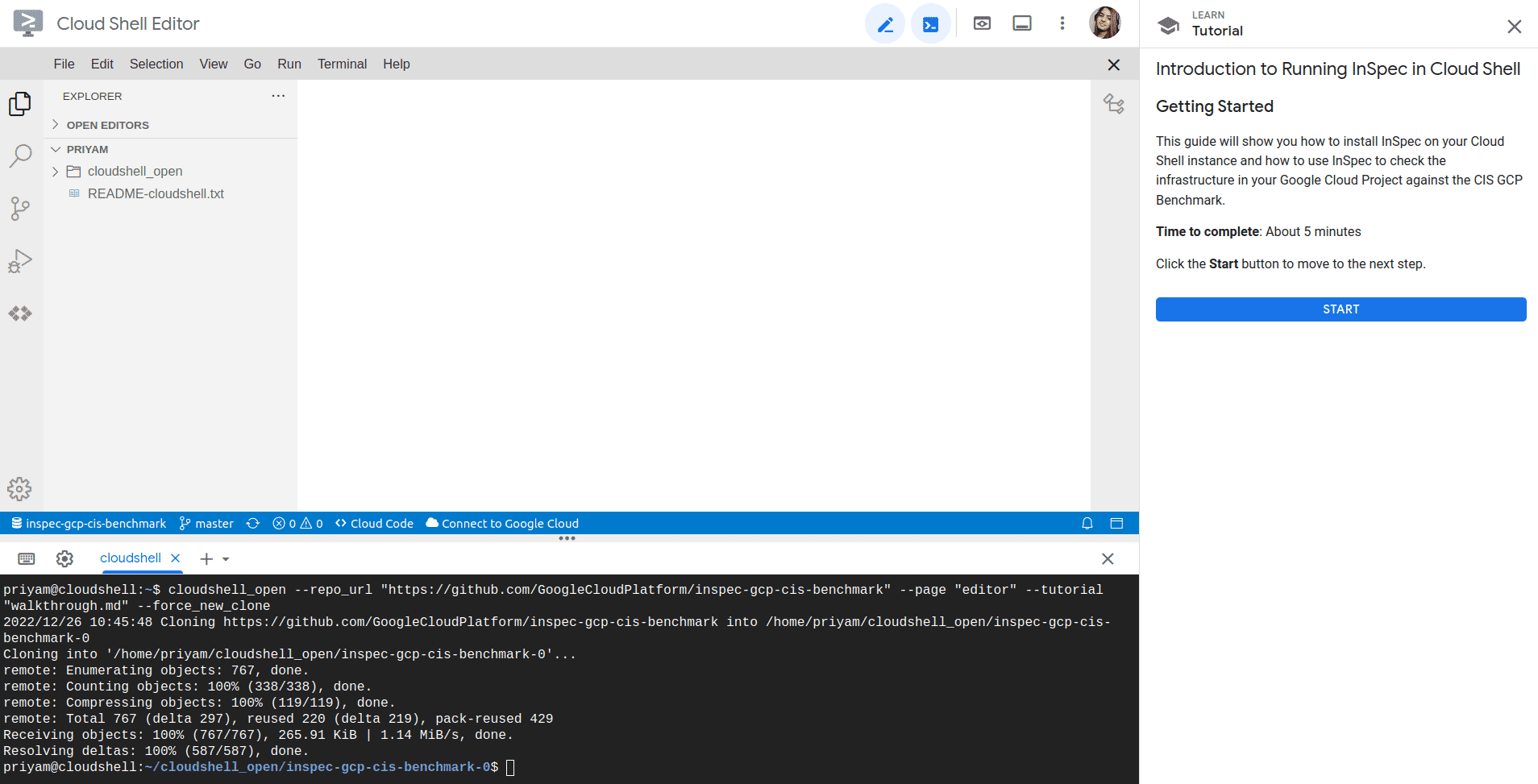
Once you click on start button, you will see the introduction to inspec and click on Next

-
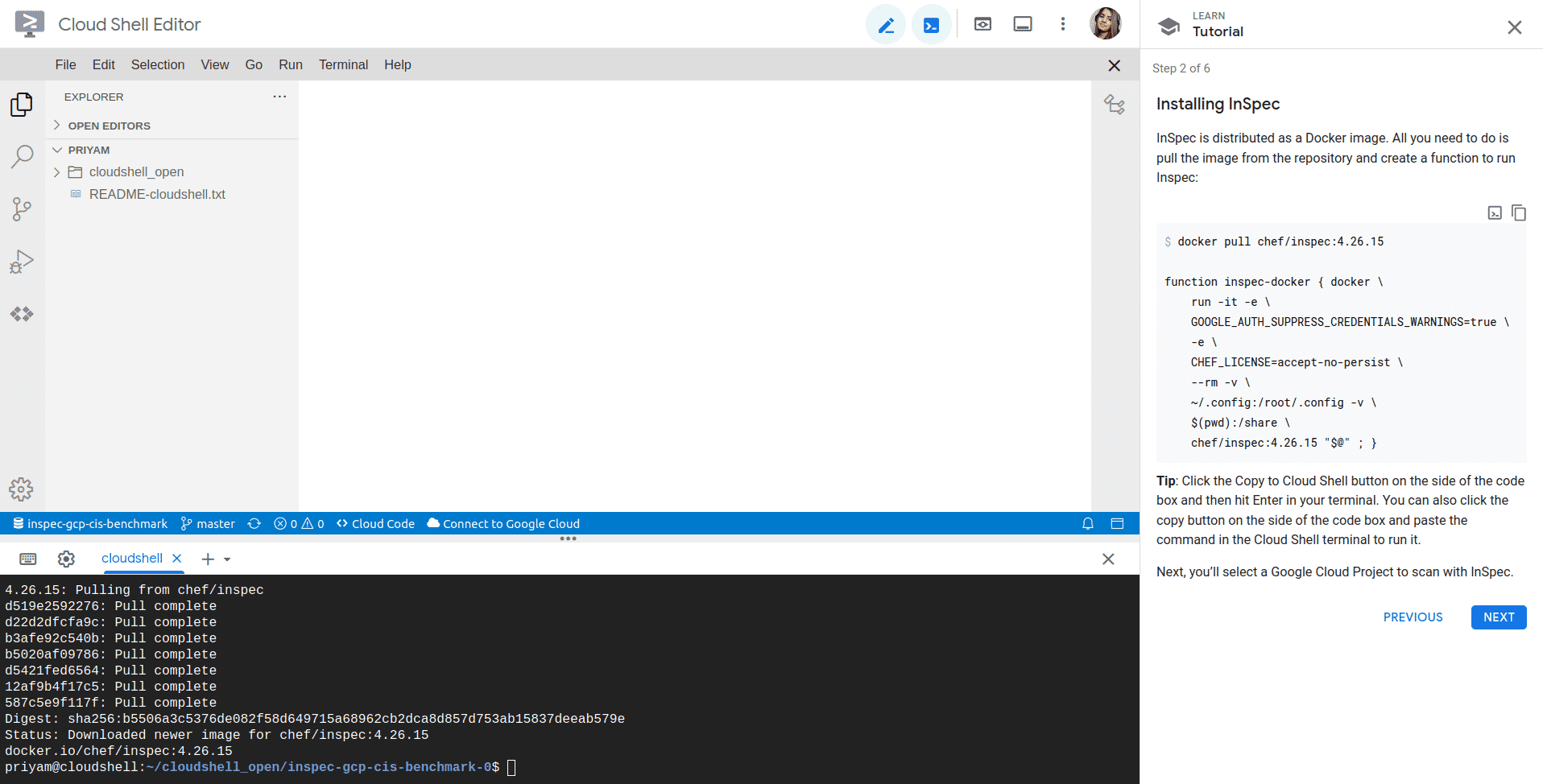
After this install inspec, then click on next.
-
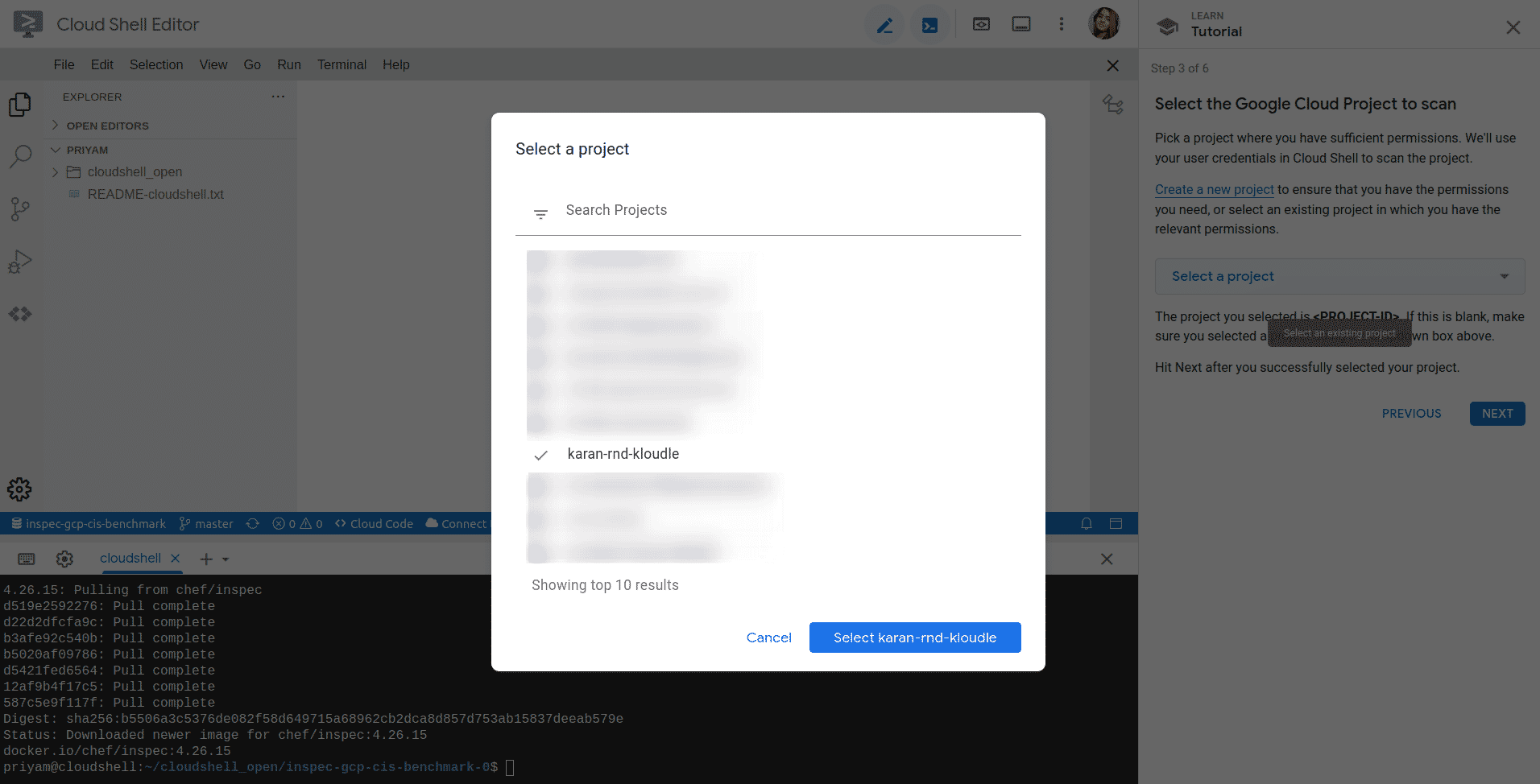
Select the cloud project on which you want to scan
-
After this run the inspec scan
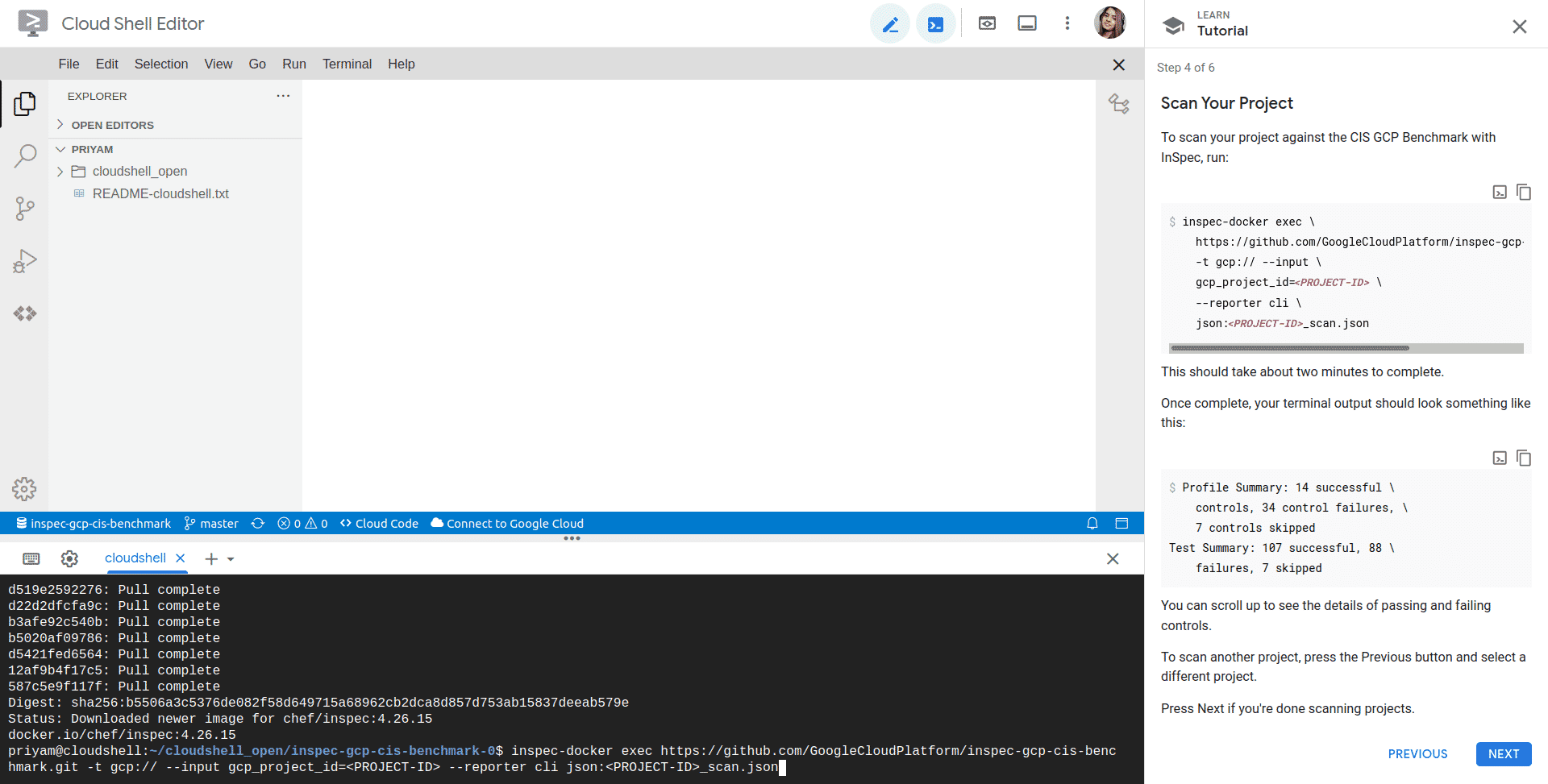
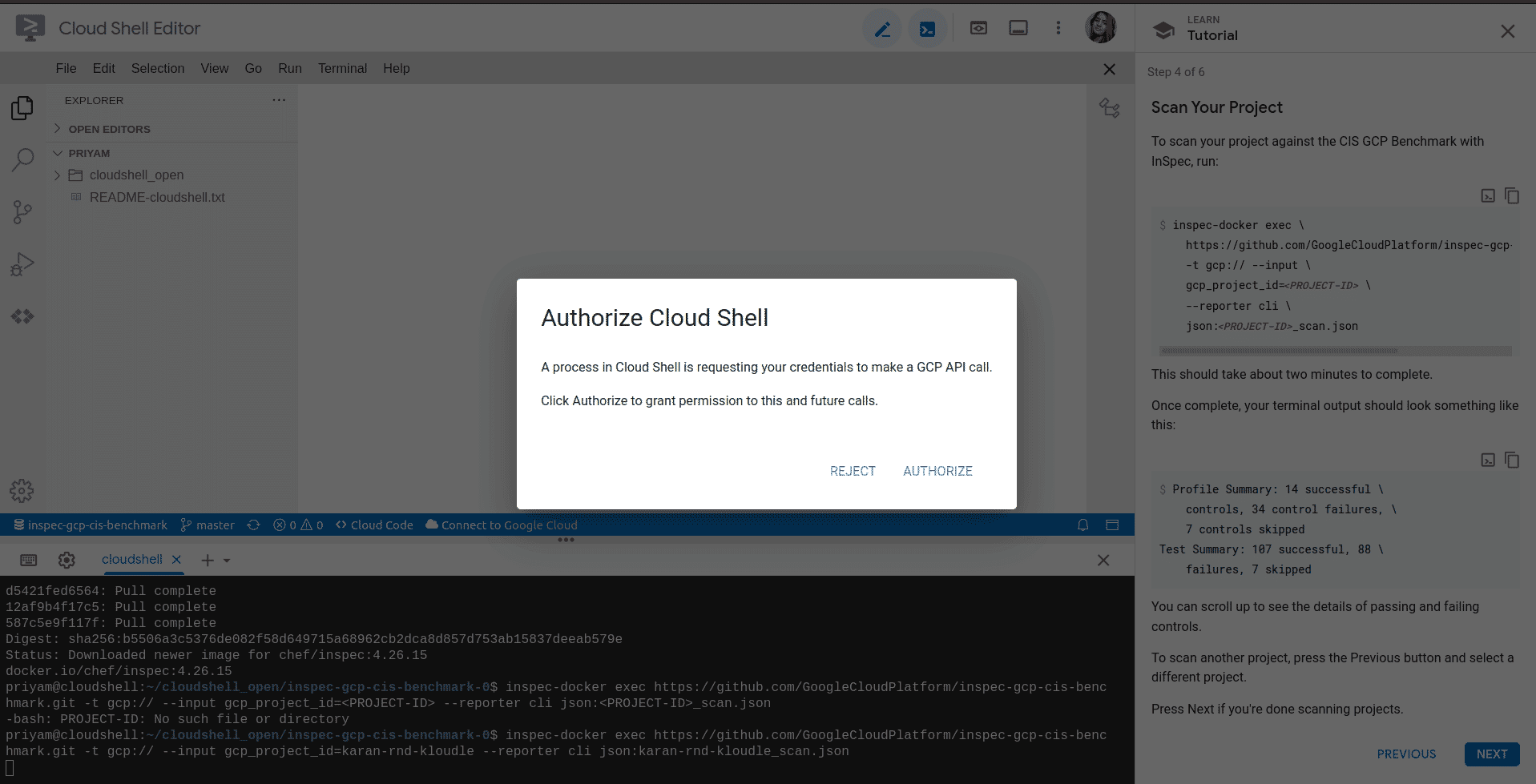
Authorize the cloud shell to make the API call
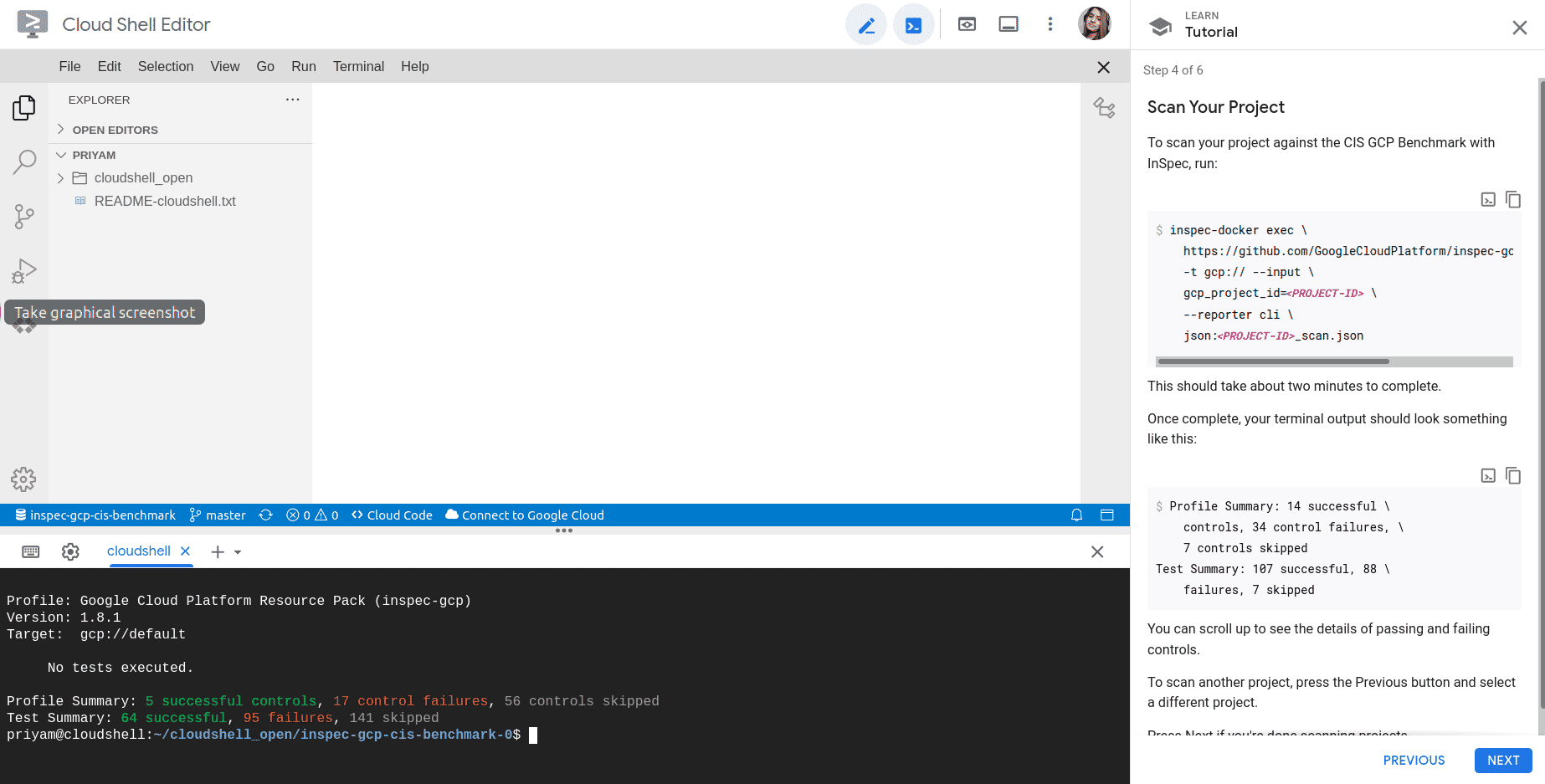
After authorization the scan will be complete
Using CLI
Prerequisites
- Install and do the configuration of the Google cloud SDK.
Download and install the SDK using the command below:
./google-cloud-sdk/install.sh
Steps for installation of Inspec
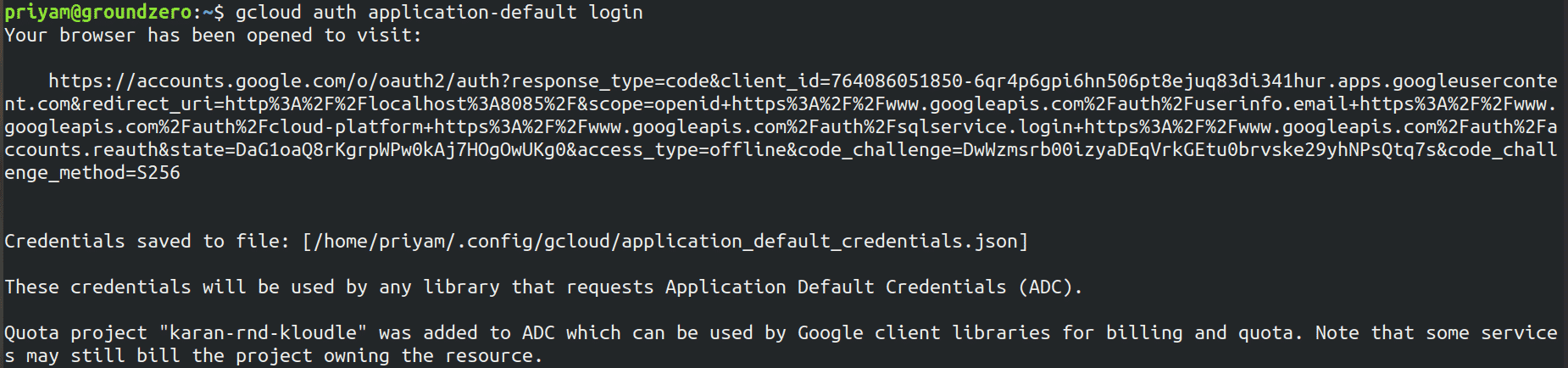
Let’s create the credentials file using the below command
gcloud auth application-default login
If successful it will open the window, and the credentials will be saved.
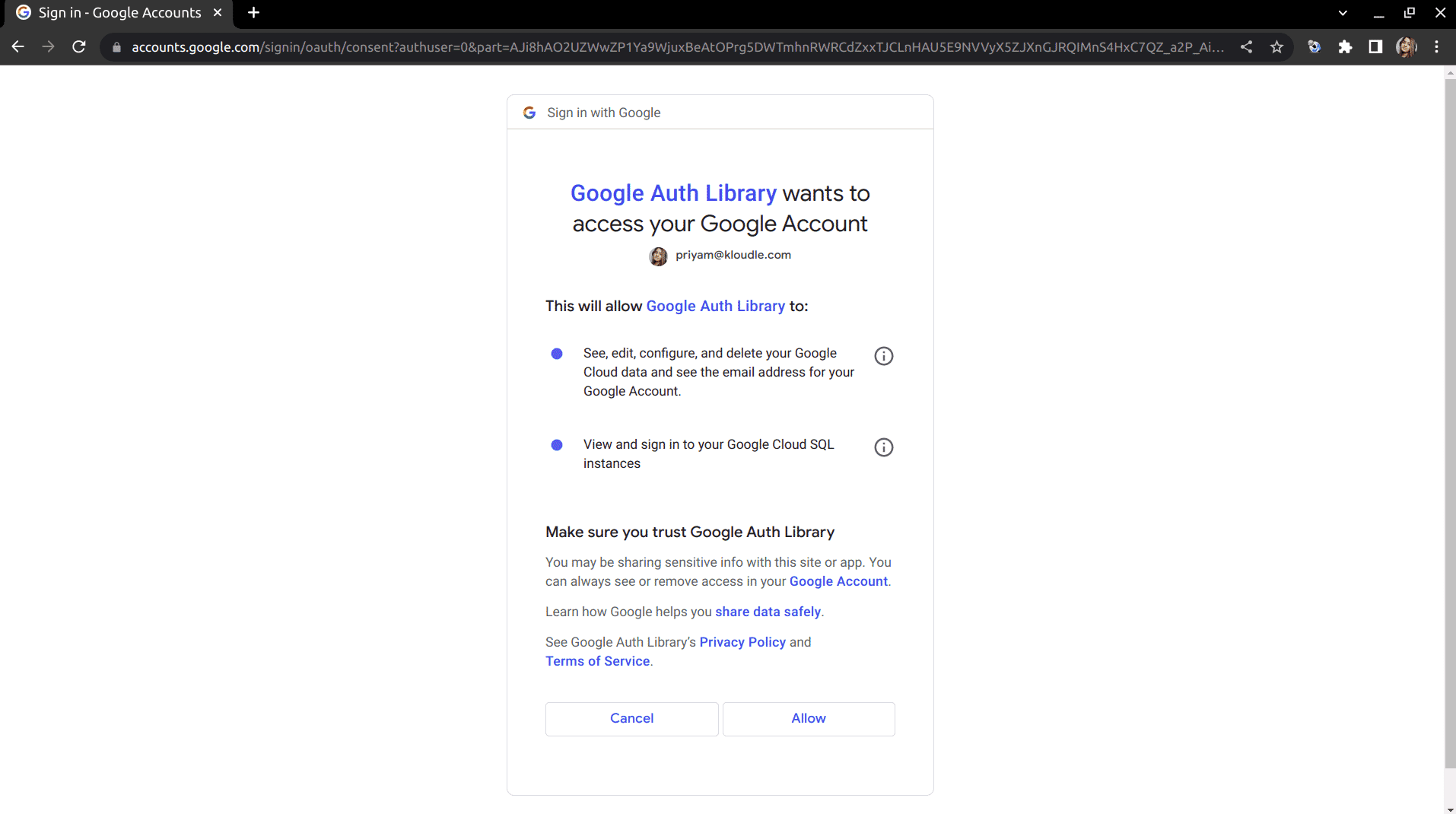
Google Cloud documentation recommends using of service accounts. InSpec can use user accounts for authentication.
Create the json credential file for a service account and save in your system. After this set the ENV variable before running the Inspec tool.
export GOOGLE_APPLICATION_CREDENTIALS='path/<json credential file name>.json'
To use the GCP resources in your tests follow the following steps
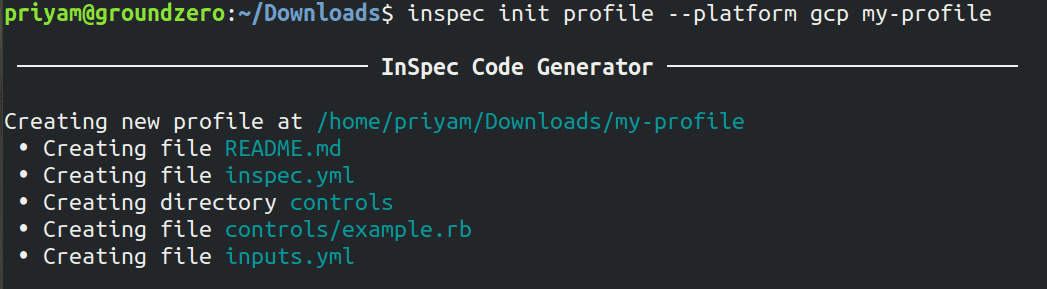
- Create a profile for GCP
inspec init profile --platform gcp my-profile
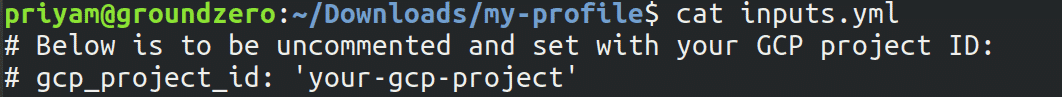
- Update inputs.yml to point to the project to on which you want to run the tool.
- After this run inspec tool and get the output
inspec exec . -t gcp:// --input-file inputs.yml

Riyaz Walikar
Founder & Chief of R&D
Riyaz is the founder and Chief of R&D at Kloudle, where he hunts for cloud misconfigurations so developers don’t have to. With over 15 years of experience breaking into systems, he’s led offensive security at PwC and product security across APAC for Citrix. Riyaz created the Kubernetes security testing methodology at Appsecco, blending frameworks like MITRE ATT&CK, OWASP, and PTES. He’s passionate about teaching people how to hack—and how to stay secure.

Riyaz Walikar
Founder & Chief of R&D
Riyaz is the founder and Chief of R&D at Kloudle, where he hunts for cloud misconfigurations so developers don’t have to. With over 15 years of experience breaking into systems, he’s led offensive security at PwC and product security across APAC for Citrix. Riyaz created the Kubernetes security testing methodology at Appsecco, blending frameworks like MITRE ATT&CK, OWASP, and PTES. He’s passionate about teaching people how to hack—and how to stay secure.