Introduction
AWS allows the creation of snapshots of EBS volumes. These snapshots can then be used to create / restore volumes and attach to an instance. These snapshots have permissions on them which can make them either public or private. A publicly available snapshot is accessible to any AWS user. Hence one should make sure that a snapshot that is not intended to be publicly accessible is made private.
If a snapshot is public, an attacker with an AWS account can create a new volume out of the exposed snapshot and mount it to an attacker controlled EC2 instance which can then be used to access all data within the snapshot.
Based on the data within the snapshot, an attacker can target other machines, leak sensitive information to the Internet or cause damage to reputation by exposing this misconfiguration as a public finding.
In this article, we will see how to update the permissions of a user owned EBS snapshot from public to private using AWS CLI.
Update EBS snapshot permissions
Following are the steps to update permissions for a user owned public EBS snapshot to private vis AWS CLI:
-
List the EBS snapshots by running the following command
aws ec2 describe-snapshots --owner-ids self --query 'Snapshots[]' --region <region>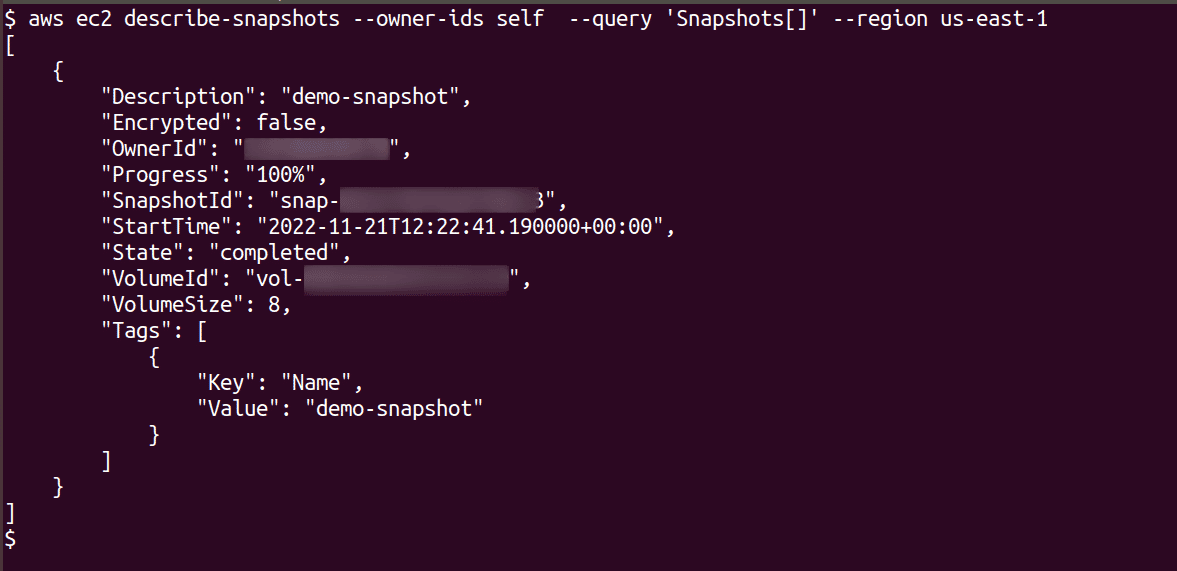
-
Modify the snapshot to update the permissions from public to private
aws ec2 modify-snapshot-attribute --region <region> --snapshot-id <snapshot id> --attribute createVolumePermission --operation-type remove --group-names all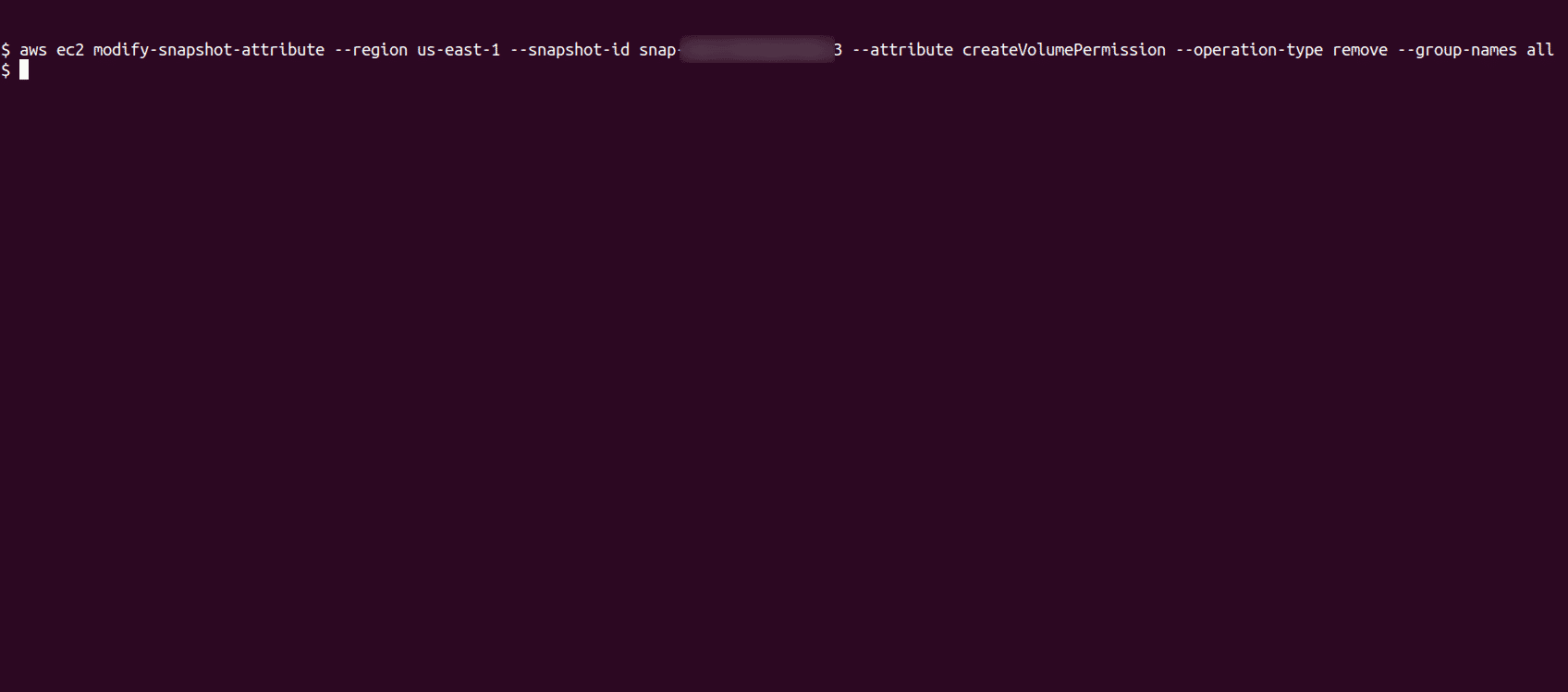

Riyaz Walikar
Founder & Chief of R&D
Riyaz is the founder and Chief of R&D at Kloudle, where he hunts for cloud misconfigurations so developers don’t have to. With over 15 years of experience breaking into systems, he’s led offensive security at PwC and product security across APAC for Citrix. Riyaz created the Kubernetes security testing methodology at Appsecco, blending frameworks like MITRE ATT&CK, OWASP, and PTES. He’s passionate about teaching people how to hack—and how to stay secure.

Riyaz Walikar
Founder & Chief of R&D
Riyaz is the founder and Chief of R&D at Kloudle, where he hunts for cloud misconfigurations so developers don’t have to. With over 15 years of experience breaking into systems, he’s led offensive security at PwC and product security across APAC for Citrix. Riyaz created the Kubernetes security testing methodology at Appsecco, blending frameworks like MITRE ATT&CK, OWASP, and PTES. He’s passionate about teaching people how to hack—and how to stay secure.