Introduction
In our listicle on Tools for Scanning IPv6 networks, you can find some open source tools that can be used for scanning IPv6 networks. In this article, we are back with our next instalment on tools for scanning IPv6. In this article, we will take a look at our second tool in the list - fi6s.
fi6s is a fast, open source port scanner for IPv6 networks written in C. fi6s makes use of a custom TCP/IP stack to scan IPv6 networks with speed, making it ideal for large-scale IPv6 network scanning tasks. This tutorial will guide you through installing fi6s and using the tool to scan an IPv6 network.
Notes:
- fi6s has support for most Linux operating systems, however, the tool does not officially support Windows. It may be possible to make use of fi6s on Windows machines through WSL Ubuntu, however, at the time of writing, this method isn’t confirmed or suggested on the project repository as a workaround.
- Make sure that the scans are conducted on the networks where you are allowed to do so with appropriate permissions.
Before we begin
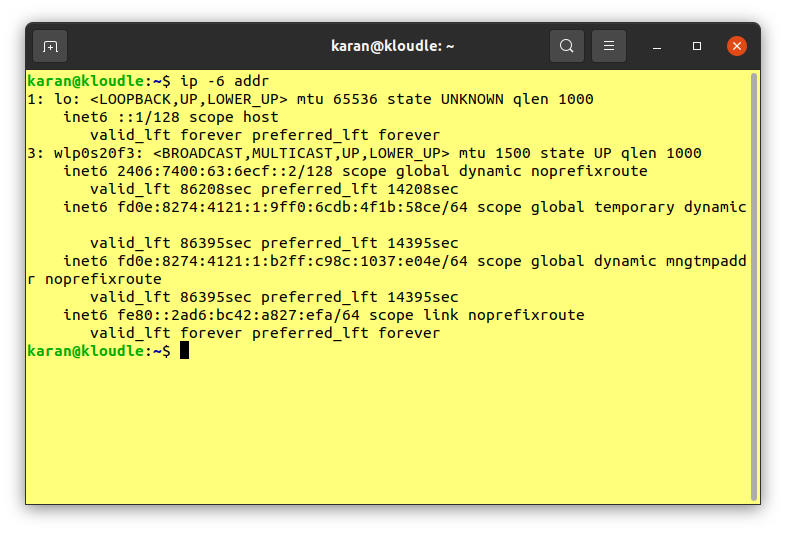
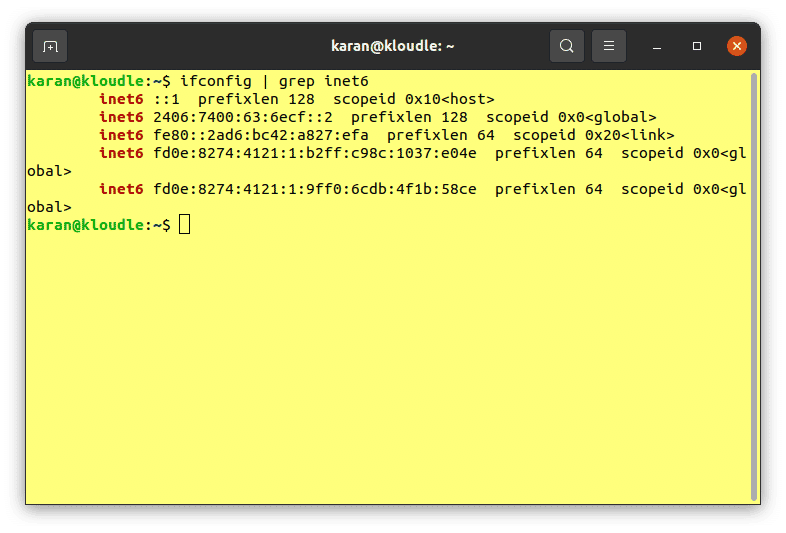
Like any other IPv6 scanning tool, your system needs to support IPv6 in order to utilise fi6s’ scanning capabilities. To verify that your system and network are properly configured to have IPv6 access, you can run either of the following commands:
-
ip -6 addr
-
ifconfig | grep inet6
Setting up fi6S
The source code for fi6s can be downloaded from the GitHub project repository. There are no pre-compiled binaries available for fi6s, thus requiring the tool’s binary to be compiled manually. GCC (or the GNU Compiler Collection) is a prerequisite for compiling the tool successfully.
As per the installation instructions provided on the repository, fi6s (and the required dependencies) can be downloaded and compiled by running the following commands:
1. sudo apt install gcc make git libpcap-dev
2. git clone https://github.com/sfan5/fi6s.git
3. cd fi6s
4. make BUILD_TYPE=release
You can verify whether the tool was successfully compiled by running ./fi6s -h. Additionally, the following commands can be used to move the compiled binary to /usr/bin, allowing for it to be executed regardless of the present working directory of the shell.
1. chmod +x fi6s
2. sudo mv fi6s /usr/bin
3. fi6s -h
Scanning IPv6 networks with fi6s
The syntax for fi6s is fairly simple. It will be intuitive for those who have used other port scanning tools (such as Nmap) before. Let’s consider the sample command provided in the README file for the project.
sudo fi6s -p 80,8000-8100 2001:db8::/120
The above command will scan port 80, as well as every port in the 8000 to 8100 range, for the 256 addresses in the range denoted by the CIDR notation. A useful feature of the tool is the --print-hosts option, which, when supplied along with a CIDR notation, will print a list of all IPv6 addresses that would be scanned as a result of the command being executed. Very useful if you want to quickly see a list of IP addresses that are targets in the CIDR you specify.
A tiny drawback of this tool is that it does not support hostname conversion, so you cannot actually scan ipv6.google.com directly but will have to provide its IPv6 address 2404:6800:4007:818::200e, instead.
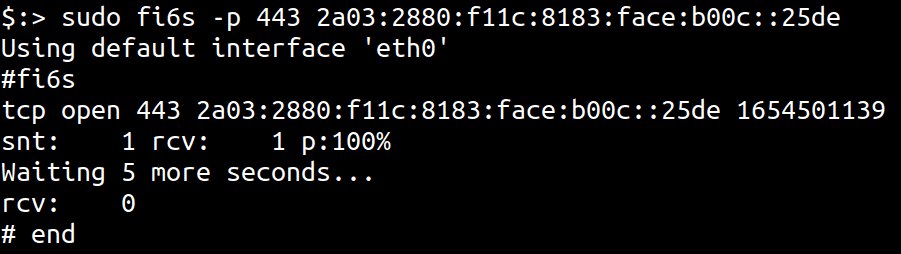
Here’s an example of fi6s being used to scan for port 443 on Facebook’s famous IPv6 address
sudo fi6s -p 443 2a03:2880:f11c:8183:face:b00c::25de
By default, fi6s will only scan addresses for open TCP ports. The author of the tool recommends adding the following ipv6tables rule to ensure scans aren’t slowed down as a result of a flurry of ICMPv6 unreachable responses for UDP scans. Note: Though recommended, this is not required, and the tool should still be able to scan UDP ports without having to add the rule.
ip6tables -A INPUT -p udp -m udp --dport 12345 -j DROP
After adding the rule to ip6tables, scanning UDP ports with fi6s is as easy as prepending the --udp option along with other required arguments for a scan. UDP scanning is unreliable in most cases, so the results would need to be verified using service specific tools (for example snmpwalk to confirm if UDP 161 is really open or not).
Note: To get a complete list of options and arguments that can be used with fi6s, run ./fi6s -h.
Conclusion
In this article, we discussed how to set up and use fi6s to scan IPv6 networks. fi6s is an open source tool designed for speed. The source code for the tool is available under the AGPL-3.0 licence.
This article is part of a series on scanning IPv6 addresses. Come back for our next article in the series in which we will take a look at another IPv6 scanner - RustScan.

Riyaz Walikar
Founder & Chief of R&D
Riyaz is the founder and Chief of R&D at Kloudle, where he hunts for cloud misconfigurations so developers don’t have to. With over 15 years of experience breaking into systems, he’s led offensive security at PwC and product security across APAC for Citrix. Riyaz created the Kubernetes security testing methodology at Appsecco, blending frameworks like MITRE ATT&CK, OWASP, and PTES. He’s passionate about teaching people how to hack—and how to stay secure.

Riyaz Walikar
Founder & Chief of R&D
Riyaz is the founder and Chief of R&D at Kloudle, where he hunts for cloud misconfigurations so developers don’t have to. With over 15 years of experience breaking into systems, he’s led offensive security at PwC and product security across APAC for Citrix. Riyaz created the Kubernetes security testing methodology at Appsecco, blending frameworks like MITRE ATT&CK, OWASP, and PTES. He’s passionate about teaching people how to hack—and how to stay secure.