Introduction
v6disc is not a port scanner per se, but a shell script to discover IPv6 hosts in the neighbourhood of your system. It also has support to run nmap to perform actual port scans but more as a wrapper than a native implementation of any tool.
The author of the scripts presents 3 reasons to use v6disc.sh
- Scan an IPv6 network 700,000 times faster than nmap
- Auto Discovery of IPv6 hosts on the network
- Quickly figure out what IPv6 is already on your network
Using parallelism, v6disc.sh scans a /64 subnet in less than 5 seconds (unverified), that is about 18,446,744,073,709,551,616 (2^64) potential addresses on a LAN segment. This speed is limited to the local network.
While playing around with the script, I realised that the best use of this script is to discover neighbouring hosts within your LAN segment and then use the other tools we have covered in this series to run specific port scans. You can also simply use the -N option to perform an nmap -6 -sT scan via v6disc itself.
The current code has a bug with the nmap scanning part as shown below, but we patched the bug locally and were able to continue using nmap for port scanning of a discovered scope.
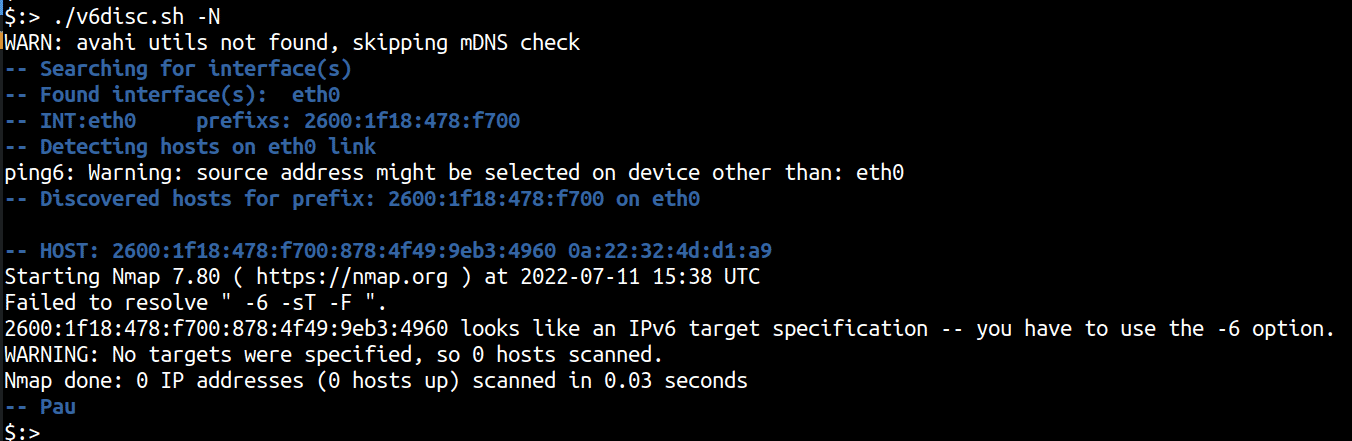
Note: As is with any security software, make sure that the scans are conducted on the networks where you are allowed to do so with appropriate permissions.
Before we begin
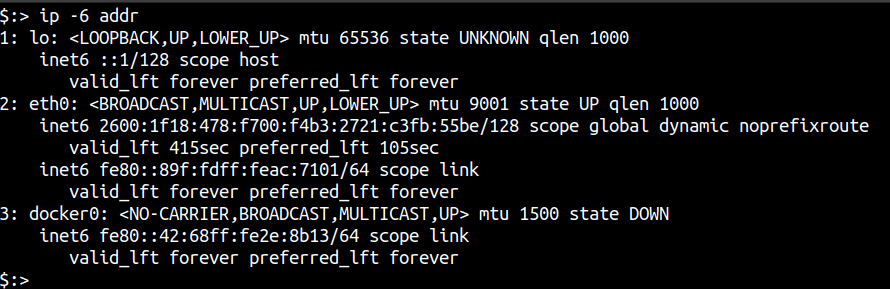
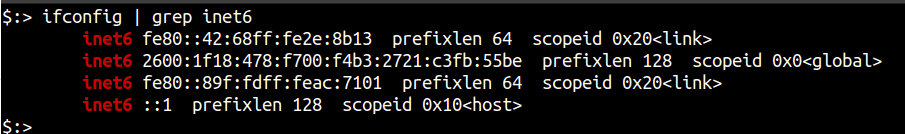
Like any other IPv6 scanning tool, your system needs to support IPv6 in order to utilise v6disc’s scanning capabilities. To verify that your system and network are properly configured to have IPv6 access, you can run either of the following commands:
-
ip -6 addr
-
ifconfig | grep inet6
Setting up v6disc
Setting up v6disc is a straightforward process on most Linux installations with the only exception of needing nmap installed if you want to use the port scanning feature. The script requires bash, ip, grep, tr, sed, sort, cut, awk, ping6 and ping, which by default are installed on most Linux distros.
Some limitations with v6disc include:
- Only detects hosts on locally attached network
- May not discover Windows machines which don’t respond to a ping6 to multicast address FF02::1
- Although MacOS X is supported (as of version 2.0), FreeBSD is still not supported. Similarly Windows is not supported as well.
The script heavily relies on the output of the ip command and its output format. To get the script running on MacOS (which doesn’t have the ip command), the script will automatically include ip_em.sh, the ip command emulator script.
To install the script, clone the repo and run the script.
git clone https://github.com/cvmiller/v6disc.git
cd v6disc
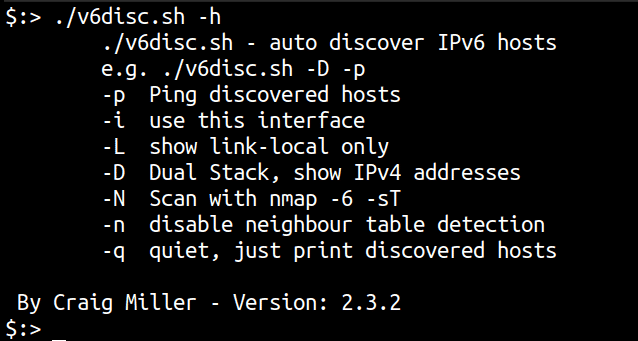
./v6disc.sh -h
Discovering and Scanning IPv6 with v6disc
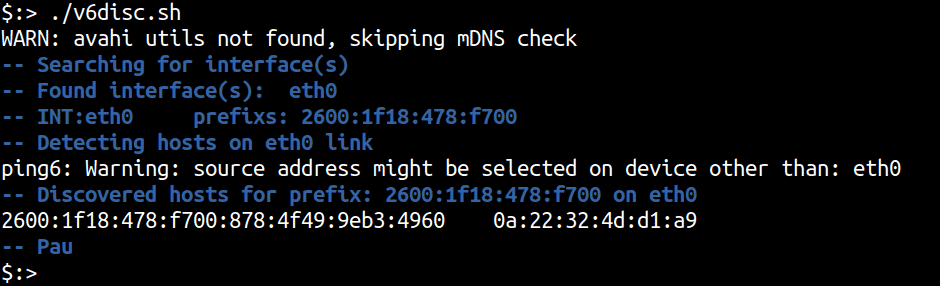
The script can be run by calling it without any arguments. The default action is to discover IPv6 hosts in the neighbourhood directly reachable from the host via a single hop.
./v6disc.sh
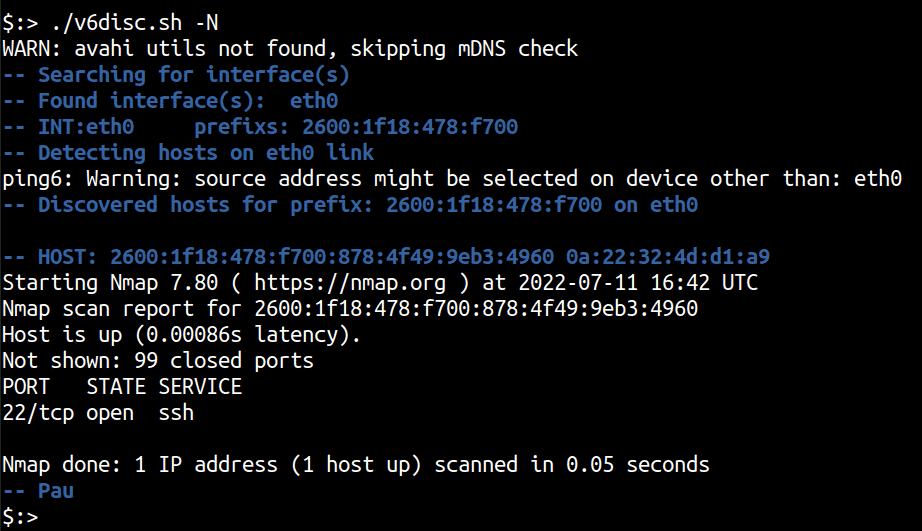
To use the nmap port scanning feature we use the -N argument that invokes nmap with the -6 -sT -F options. However, owing to a bug with the script, the nmap scanning doesn’t work. A quick patch however, allows for the nmap scanning to proceed as designed.
./v6disc.sh -N
Conclusion
In this article we looked at v6disc, which is a bash script on top of common network utilities in Linux that is used to perform IPv6 host discovery in the neighbourhood. The script can also be used to scan for IPv6 hosts using nmap that has to be installed in order to use the script’s scanning capabilities.
This article is the last of the series on scanning IPv6 addresses. In the previous articles we looked at nmap, fi6s, rustscan and massscan as the other tools that can be used to scan IPv6 networks.
While the adoption of IPv6 isn’t absolute yet, a multitude of services in the cloud respond to and can be configured to work with IPv6. From a security perspective it is important to be able to discover and scan for running services using IPv6.

Riyaz Walikar
Founder & Chief of R&D
Riyaz is the founder and Chief of R&D at Kloudle, where he hunts for cloud misconfigurations so developers don’t have to. With over 15 years of experience breaking into systems, he’s led offensive security at PwC and product security across APAC for Citrix. Riyaz created the Kubernetes security testing methodology at Appsecco, blending frameworks like MITRE ATT&CK, OWASP, and PTES. He’s passionate about teaching people how to hack—and how to stay secure.

Riyaz Walikar
Founder & Chief of R&D
Riyaz is the founder and Chief of R&D at Kloudle, where he hunts for cloud misconfigurations so developers don’t have to. With over 15 years of experience breaking into systems, he’s led offensive security at PwC and product security across APAC for Citrix. Riyaz created the Kubernetes security testing methodology at Appsecco, blending frameworks like MITRE ATT&CK, OWASP, and PTES. He’s passionate about teaching people how to hack—and how to stay secure.