Introduction
GitHub is a SaaS platform used for version control and software development using Git. It offers the distributed version control and source code management functionality of Git, plus its own features.
In this article, we will cover top 10 security best practices to follow for improving the security of your GitHub organisation and repositories.
Top 10 Security best practices
Here is a list of top 10 best practices to enhance the security of your GitHub organisation account:
-
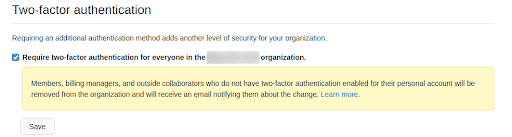
Enable organisation wide two-factor authentication (2FA)
Two-factor authentication provides an additional layer of security and must be enabled wherever possible. This way even if the account password is compromised, an attacker still cannot gain access to the account without the additional authentication factors.
GitHub provides the ability to enforce organisation wide two-factor authentication. This setting ensures that new users joining your GitHub organisation have two-factor authentication enabled from the beginning.
-
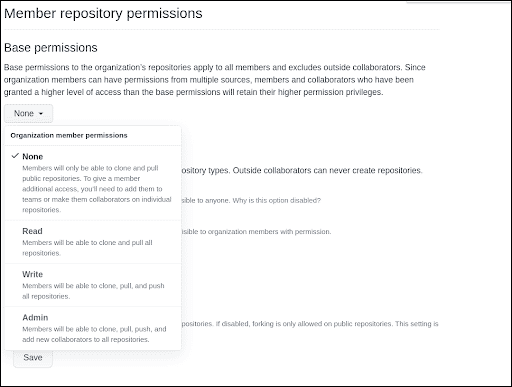
Limit base permissions
Access to repositories within an organisation can be managed using base permissions. These base permissions apply to all the members of a GitHub organisation. A member can have None, Read, Write or Admin permissions.
By default, GitHub organisation provides “Read” permission to the repositories to all the members, however from security perspective, setting this permission to None is a better option. To give the members any additional permissions, the admin must explicitly add them to teams or collaborators for accessing individual repositories.
-
Limit permissions for outside collaborators
GitHub has provisions to allow access to the organisation’s repositories to users who are not part of the organisation. Such users are known as outside collaborators.
Outside collaborators must be provided only required permissions and these permissions must be regularly reviewed. It is also a good practice to enforce two-factor authentication for all outside collaborators.
-
Verify third-party apps
Applications integrated in the organisation can be approved by all the owners. It is possible that a malicious third-party application is integrated intentionally or unintentionally. Therefore, as a security best practice, third party applications must be regularly verified to ensure that only required applications are present in the list.
-
Review access rights for third-party apps
Third-party applications can have different levels of access rights. It is essential to consciously understand the access that an application requires at the time of integration and regularly monitor the access rights of the applications.
-
Manage secrets
One of the most common security issues is hardcoded secrets present in the source code. Hardcoded secrets can provide additional access to attackers. Based on the type of hardcoded secrets, attackers could move from the code repository to attacking the cloud infrastructure.
Secrets should not be baked into the code but instead should be supplied to the pipeline using environment variables or via GitHub’s secrets manager. As a best practice, regular secrets scanning should also be performed.
-
Users membership should not be public
User membership to an organisation should ideally be private from a security point of view. Exposing a user’s membership for an organisation allows attackers to target the user via phishing attacks that could lead to attackers impersonating the user or even gaining access to the user’s account.
-
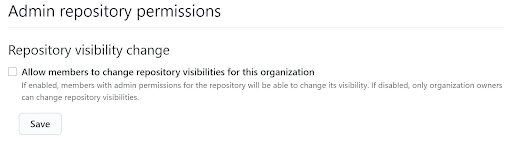
Restrict repository visibility permissions
Admin repository permissions include allowing admins to change repository visibility. If this setting is enabled, a malicious admin could change the visibility of a repository, resulting in code theft. The repo also becomes searchable on GitHub and will be cached by search engines. As a security best practice, this setting should be disabled to ensure no repository is made public by accident or malice.
-
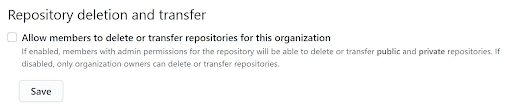
Repository deletion and transfer
GitHub allows organisation owners to control what the admin users are capable of, at an organisation level. A global setting exists that prevents admin users from deleting or transferring a repository to another organisation or user. If this setting is enabled, a member can delete the entire repository or simply effect a change in ownership. Hence, this setting should be disabled.
-
Monitor Audit Logs
Audit logs are created in the GitHub organisation that provide vital information on the actions performed by members. It includes details like the action performed, the member who initiated the action, the timestamp, etc. The audit logs should be regularly monitored for suspicious activities within the organisation.
Conclusion
GitHub is a platform for maintaining source code in the repositories within an organisation. It is important to keep your GitHub organisation secure since it contains data that may be critical and sensitive in nature. Therefore, it is essential to follow the security best practices and monitor any actions or the entities that performed certain actions on a regular basis.

Riyaz Walikar
Founder & Chief of R&D
Riyaz is the founder and Chief of R&D at Kloudle, where he hunts for cloud misconfigurations so developers don’t have to. With over 15 years of experience breaking into systems, he’s led offensive security at PwC and product security across APAC for Citrix. Riyaz created the Kubernetes security testing methodology at Appsecco, blending frameworks like MITRE ATT&CK, OWASP, and PTES. He’s passionate about teaching people how to hack—and how to stay secure.

Riyaz Walikar
Founder & Chief of R&D
Riyaz is the founder and Chief of R&D at Kloudle, where he hunts for cloud misconfigurations so developers don’t have to. With over 15 years of experience breaking into systems, he’s led offensive security at PwC and product security across APAC for Citrix. Riyaz created the Kubernetes security testing methodology at Appsecco, blending frameworks like MITRE ATT&CK, OWASP, and PTES. He’s passionate about teaching people how to hack—and how to stay secure.