Creating a self hosted runner
-
Login to GitHub and navigate to the settings page of the Organization
-
From the “Code, planning and automation” section on the left, click on Actions > Runners
-
Click on the “New runner” button and select “New self-hosted runner”
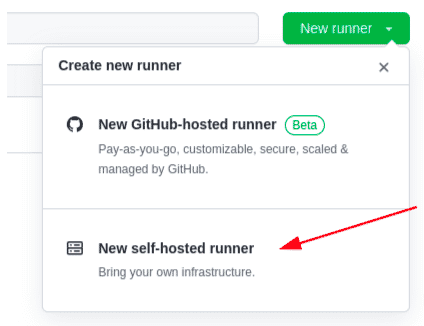
-
For this exercise, our self hosted runner is a docker container based on an Ubuntu image.
-
Do not run any command here, but simply copy the value of the TOKEN shown under “Configure”
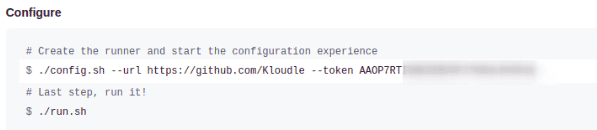
Setting up a local runner using docker to perform secrets scanning in GitHub
The following commands are a one time set up to launch a docker container based on an Ubuntu image, install required tools in it and connect it to GitHub as a self hosted runner.
docker run -it --name gh-runner-ubuntu ubuntu
docker exec -it gh-runner-ubuntu bash
apt install curl sudo wget git -y
adduser app
usermod -aG sudo app
su app
cd ~
mkdir actions-runner && cd actions-runner
curl -o actions-runner-linux-x64-2.297.0.tar.gz -L https://github.com/actions/runner/releases/download/v2.297.0/actions-runner-linux-x64-2.297.0.tar.gz
tar xzf ./actions-runner-linux-x64-2.297.0.tar.gz
mkdir trufflehog && cd trufflehog
wget https://github.com/trufflesecurity/trufflehog/releases/download/v3.14.0/trufflehog_3.14.0_linux_amd64.tar.gz
tar xzf ./trufflehog_3.14.0_linux_amd64.tar.gz
sudo cp trufflehog /usr/bin/
cd ..
./config.sh --url https://github.com/Kloudle --token TOKEN
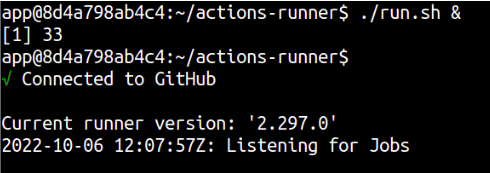
./run.sh &
A message should print on screen that says “Connected to GitHub”
The runner will be visible (status idle) under https://github.com/organizations/ORG_NAME/settings/actions/runners, if set up correctly.
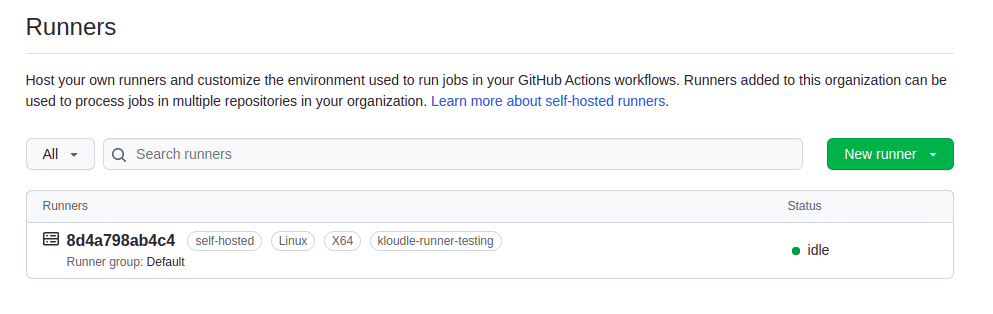
GitHub Actions Workflow under the repo
-
Navigate to the repository that you want to perform code secret scanning on
-
Click on the “Actions” tab
Note: If “Actions” is not visible, it means that either the repo is excluded from Actions settings or Actions is disabled Organization wide. Review the settings under
https://github.com/organizations/ORG_NAME/settings/actions -
Click on the link under “Actions” to “set up a workflow yourself”
-
Add the following YAML as main.yml. Note the name of the branch (master/main) and update the YAML as required.
name: Secrets Scanning with GitHub Actions and TruffleHog # Controls when the workflow will run on: # Triggers the workflow on push or pull request events but only for the "master" branch push: branches: [ "main" ] pull_request: branches: [ "main" ] # A workflow run is made up of one or more jobs that can run sequentially or in parallel jobs: # This workflow contains a single job called "build" build: # The type of runner that the job will run on runs-on: kloudle-runner-testing # Steps represent a sequence of tasks that will be executed as part of the job steps: # Checks-out your repository under $GITHUB_WORKSPACE, so your job can access it - uses: actions/checkout@v3 # Runs a single command using the runners shell - name: Run trufflehog run: trufflehog --no-update filesystem --directory=${{ github.workspace }} --json > /tmp/trufflehog.json # Upload the scan output - name: Upload the scan output uses: actions/upload-artifact@v2 with: name: scan_results path: /tmp/trufflehog.json retention-days: 2 -
The YAML creates a workflow that will allow the runner to checkout the repo whenever a push or a pull request is created to the “main” branch, and run TruffleHog on it. The runner will end the job after the scan results are uploaded to GitHub.
-
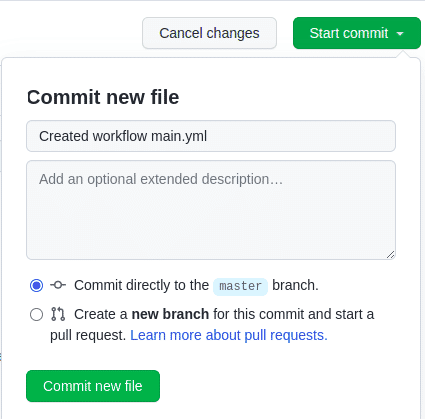
Click on “Start commit” and commit the workflow file to trigger a job.
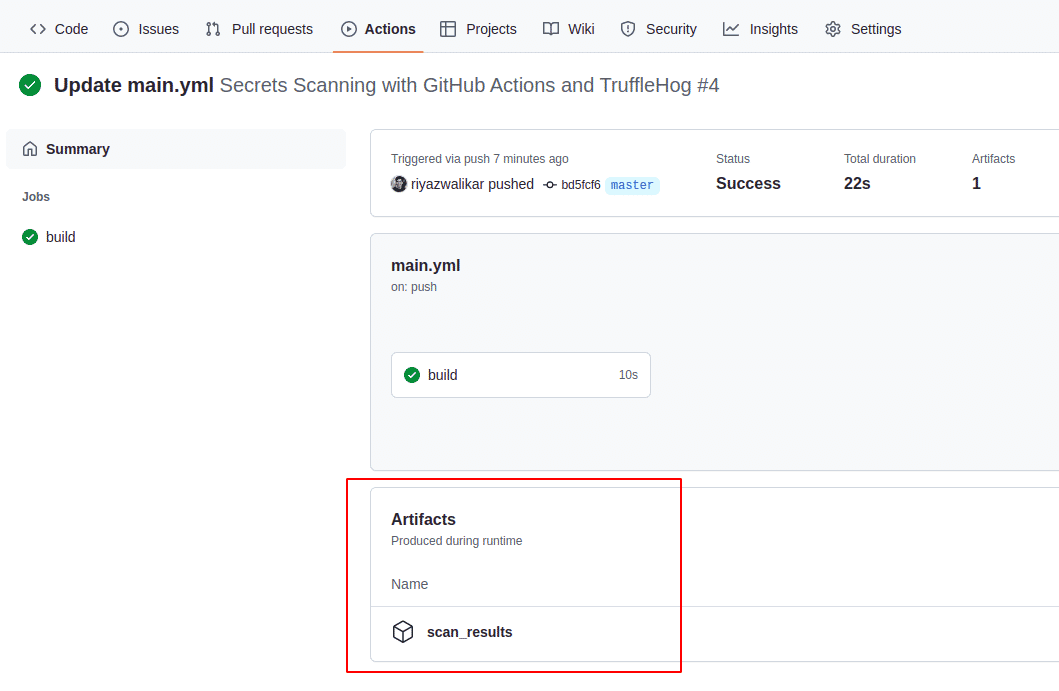
You can download the results from the scan under the “Actions” > Workflow run > Artifacts as shown in the screenshot below

Riyaz Walikar
Founder & Chief of R&D
Riyaz is the founder and Chief of R&D at Kloudle, where he hunts for cloud misconfigurations so developers don’t have to. With over 15 years of experience breaking into systems, he’s led offensive security at PwC and product security across APAC for Citrix. Riyaz created the Kubernetes security testing methodology at Appsecco, blending frameworks like MITRE ATT&CK, OWASP, and PTES. He’s passionate about teaching people how to hack—and how to stay secure.

Riyaz Walikar
Founder & Chief of R&D
Riyaz is the founder and Chief of R&D at Kloudle, where he hunts for cloud misconfigurations so developers don’t have to. With over 15 years of experience breaking into systems, he’s led offensive security at PwC and product security across APAC for Citrix. Riyaz created the Kubernetes security testing methodology at Appsecco, blending frameworks like MITRE ATT&CK, OWASP, and PTES. He’s passionate about teaching people how to hack—and how to stay secure.