Introduction
Amazon, in a recent blog announcement, shared that AWS S3 will encrypt all new objects by default. This post analyzes the update and explains what it means to consumers, auditors and tool creators who work with AWS S3.
What is Server Side Encryption for S3?
AWS SSE-S3 is a decade old AWS S3 server side encryption that has been available as an encryption option when attempting to secure objects uploaded to S3. This is a 256-bit AES encryption, also known as AES-256 which is one of the strongest block ciphers available. The entire encryption, key management, and decryption process is transparent to the user.
AWS S3 provides two types of encryption depending on who manages the keys. You can use either server-side encryption with Amazon S3 managed keys (SSE-S3) or server-side encryption with AWS Key Management Service (AWS KMS) keys (SSE-KMS).
With SSE-KMS, you have more control over your key. If you use SSE-KMS, you can choose an AWS KMS customer managed key or use the default AWS managed key (aws/s3).
How to detect if objects are encrypted?
To check if your objects are encrypted in a bucket or not, you will need to know the name of the bucket and the object you want to inspect.
You can verify encryption using either the web console or the CLI.
Using the Web Console
- Login to the AWS console and navigate to S3
- Under S3, open the bucket that contains your object
- Click on the object and scroll down to find
Server-side encryption settingspanel. The status of encryption is shown here
- The panel will show either “Off”, “Amazon S3-managed keys (SSE-S3)” or the KMS Key ARN used to encrypt the object.
Using the CLI
- Ensure you are using the correct AWS profile and credentials
- Run the following command
aws s3api head-object --query ServerSideEncryption --bucket <bucket-name> --key <object-name>
- The output will be either “null”, “AES256” or “aws:kms”
What does the AWS announcement mean?
Earlier this month, AWS announced that Amazon Simple Storage Service (Amazon S3) encrypts all new objects by default. S3 will automatically apply server-side encryption (SSE-S3) for each new object, unless you specify a different encryption option post the upload.
The difference is, earlier we had to explicitly set the SSE-S3 encryption on objects but now AWS will take care of this by default. This is a great change to AWS S3’s design principles as this ensures objects are secure by default on disk.
We decided to verify this per the AWS announcement and see what it means and looks like for users and tools.
Our observations
Although, AWS claims this is a “zero click” design and that all new objects are encrypted by default, we noticed the following
-
Currently, AWS encrypts objects being added to a bucket. This is visible in a CloudTrail data log that records
PutObjectAPI calls for file uploads orInitiateMultipartUploadfor multipart uploads. A key-value pair of"SSEApplied":"Default_SSE_S3"is present in the API call.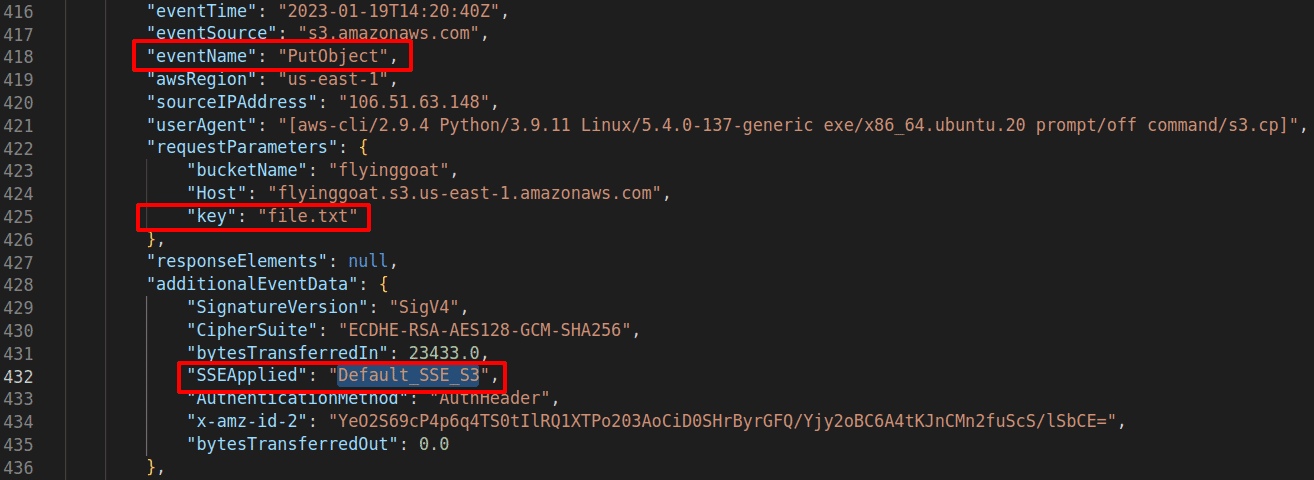
-
The web console and API calls via the CLI do not show encryption status if the encryption is not explicitly enabled. Basically, if you upload a file to S3, you still have to go enable encryption for the status of encryption to change to “Amazon S3-managed keys (SSE-S3)”. Else this is always shown as “Off”.
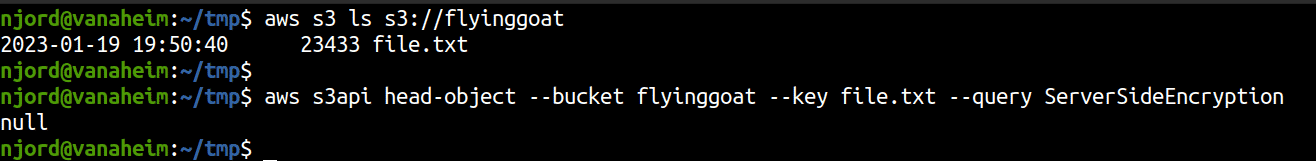
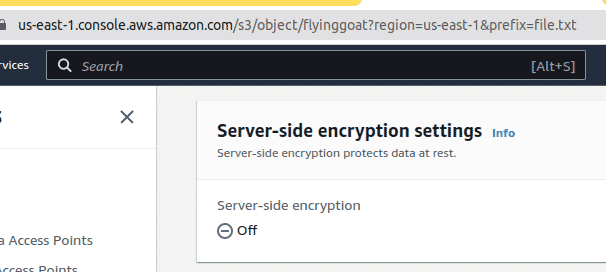
-
Any tool or service that relies on the API calls to detect if an object is encrypted or not will simply flag the object as unencrypted. This could result in incorrect results and false positives. For example, compliance tools and cloud security products may incorrectly report this.
-
There is no way currently, other than taking AWS’ word for this and relying on data events via Cloudtrail for S3 to detect if an object has server side encryption enabled.
What can you do?
We recommend server side encryption to all our customers, regardless of whether this is now a default setting or not. Enable Server Side encryption and choose one of the two options presented to you. If you do not have KMS then ensure “Amazon S3-managed keys (SSE-S3)” is selected.
Unfortunately, this step needs to be repeated per object to ensure encryption settings are applied properly across the bucket.
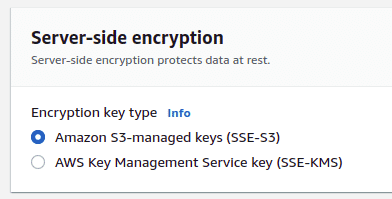
Bucket wide encryption can be applied to any new objects that are added to the bucket under bucket properties.
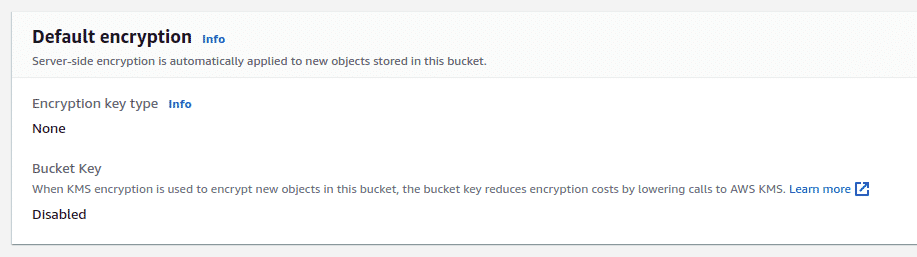
Until AWS updates their APIs to show the correct state of the objects encryption if the objects have server side encryption enabled by default, we need to ensure encryption settings are applied properly.
References
- https://aws.amazon.com/blogs/aws/amazon-s3-encrypts-new-objects-by-default
- https://aws.amazon.com/blogs/aws/new-amazon-s3-server-side-encryption/
- https://docs.aws.amazon.com/AmazonS3/latest/userguide/default-bucket-encryption.html

Riyaz Walikar
Founder & Chief of R&D
Riyaz is the founder and Chief of R&D at Kloudle, where he hunts for cloud misconfigurations so developers don’t have to. With over 15 years of experience breaking into systems, he’s led offensive security at PwC and product security across APAC for Citrix. Riyaz created the Kubernetes security testing methodology at Appsecco, blending frameworks like MITRE ATT&CK, OWASP, and PTES. He’s passionate about teaching people how to hack—and how to stay secure.

Riyaz Walikar
Founder & Chief of R&D
Riyaz is the founder and Chief of R&D at Kloudle, where he hunts for cloud misconfigurations so developers don’t have to. With over 15 years of experience breaking into systems, he’s led offensive security at PwC and product security across APAC for Citrix. Riyaz created the Kubernetes security testing methodology at Appsecco, blending frameworks like MITRE ATT&CK, OWASP, and PTES. He’s passionate about teaching people how to hack—and how to stay secure.