- What is Kloudle?
- What is this document about?
- AWS Onboarding for Kloudle
- Pre-Requisites
- Video Instructions
What is Kloudle?
Kloudle is a Digital Assets Security Automation Platform for SREs and DevOps. When integrated with your Cloud or SaaS provider, Kloudle takes periodic security snapshots and provides complete security contextual visibility that allows you to make informed decisions about your infrastructure, the assets and their various configurations.
Kloudle collects metadata about the resources and analyzes them to identify misconfigurations and using a massive research powered knowledgebase, identifies what would go wrong if these misconfigurations were exploited and what you can do to fix them.
As part of making sure the lives of SREs and DevOps become easier, Kloudle offers the ability to create “rules” that allow a user to take automated actions against a baseline. These automated actions, which we call Security Processes, allow users to configure a series of steps that kick in when custom events occur to ensure the security of the cloud and SaaS platform being monitored.
What is this document about?
This document details the steps that are required to create an AWS user that will be onboarded to Kloudle so that Kloudle can make API requests to AWS.
AWS Onboarding for Kloudle
Pre-Requisites
- You need to be an IAM user with the ability to create other IAM users and attach policies to them.
Through Console
-
Log in to the AWS account you want to onboard
-
Ensure you have permissions to create an IAM user and attach policies to the user
-
Navigate to IAM - https://console.aws.amazon.com/iamv2/home
-
Go to Users page
-
Click on the “Add users” button
-
Enter User Name as
kloudle-user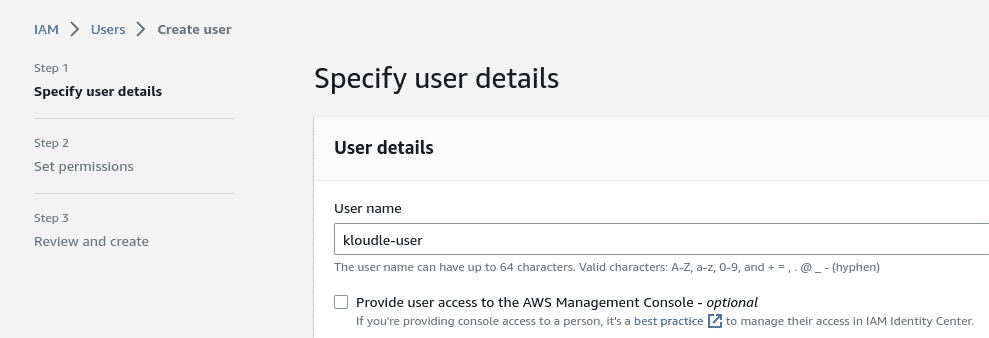
-
Click on “Next”
-
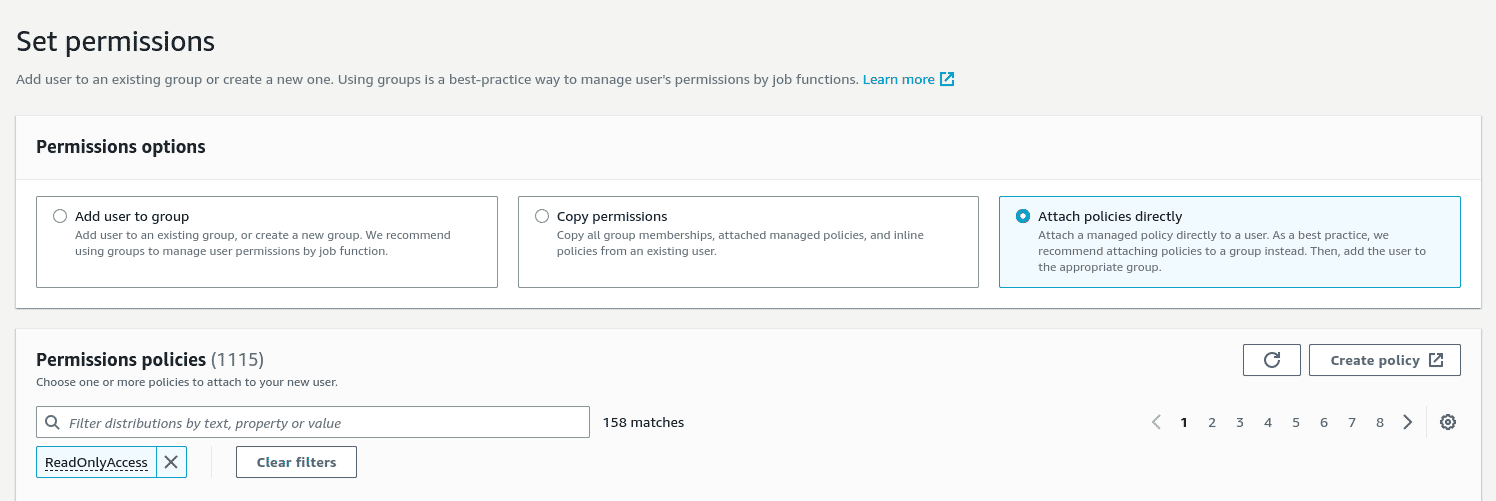
Choose “Attach existing policies directly”.
-
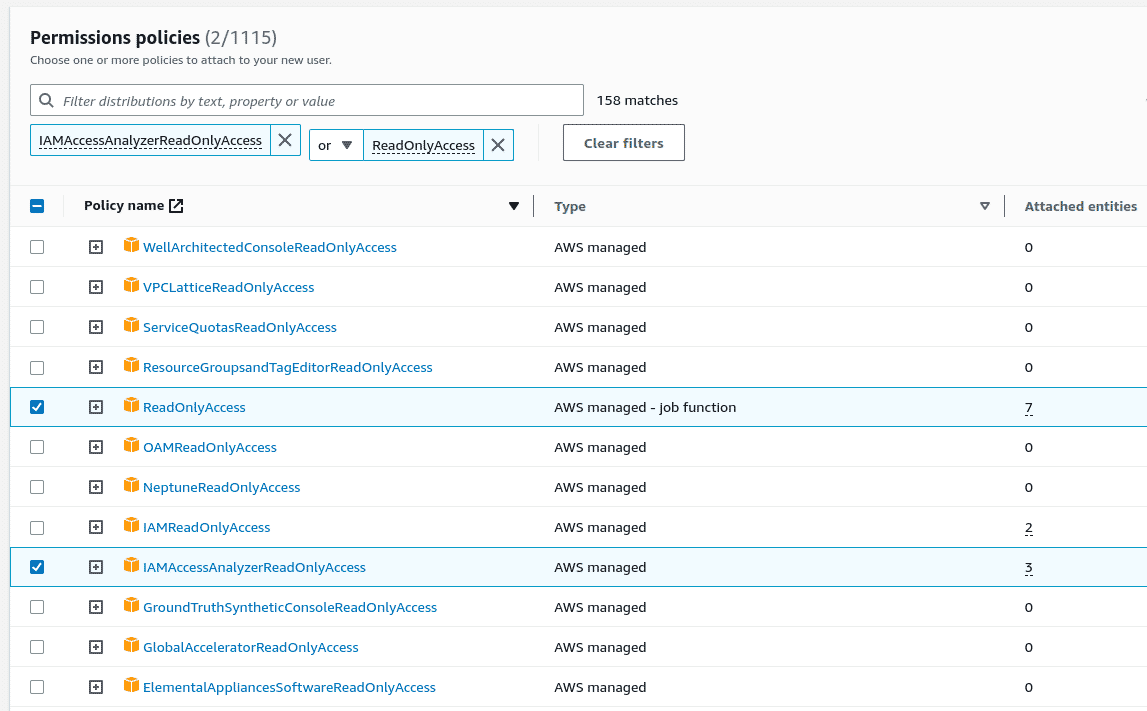
We will require two policies to be attached
ReadOnlyAccessandIAMAccessAnalyzerReadOnlyAccess. Search for these policies using the “Filter policies” search box. Sort the “Policy name” column if you don’t see the policy in the list.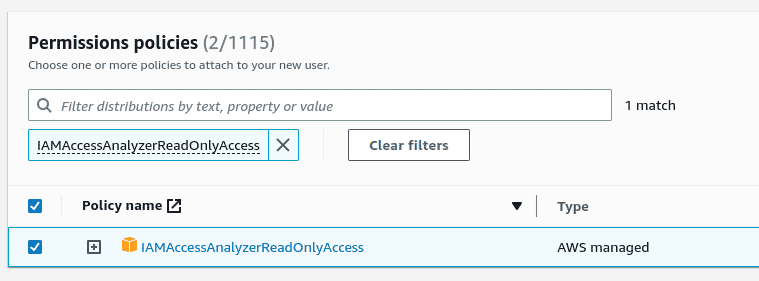
-
Add Tags in the next page,
createdByandcreatedFor, by clicking on “Add new tag” button.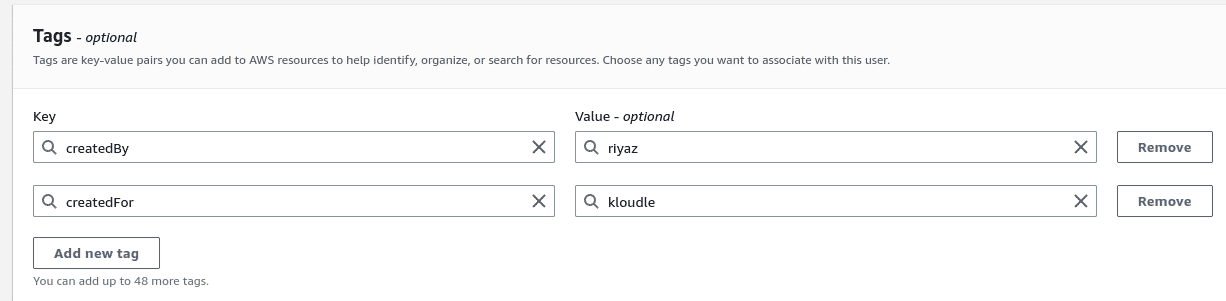
-
Click on the “Create user” button
-
To create an Access Key and a Secret Key for this user, select the user from the list of users in IAM and click on the “Security credentials” tab and click “Create access key”
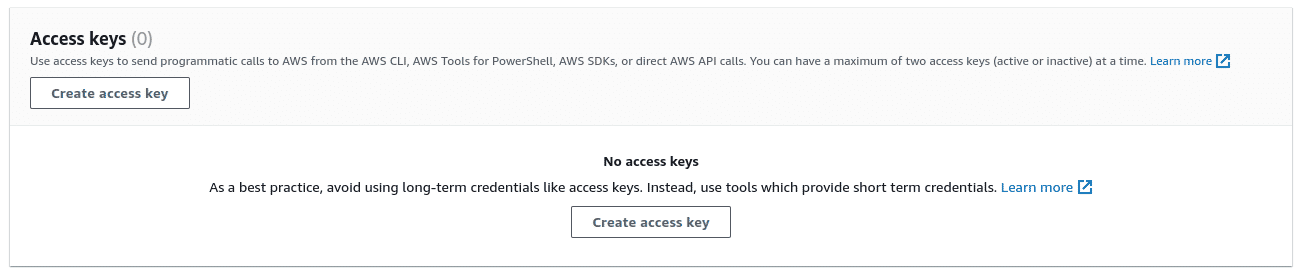
-
Select the “Application running outside AWS” option under the “Access key best practices & alternatives” page
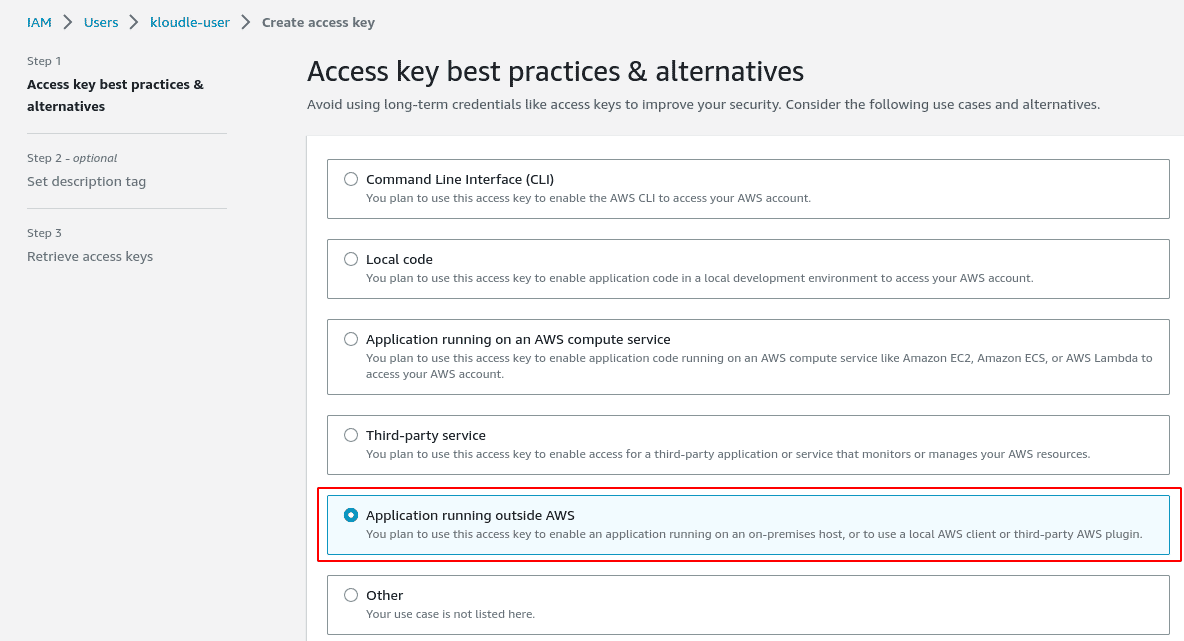
-
Generate a description tag - “generated-for-kloudle”
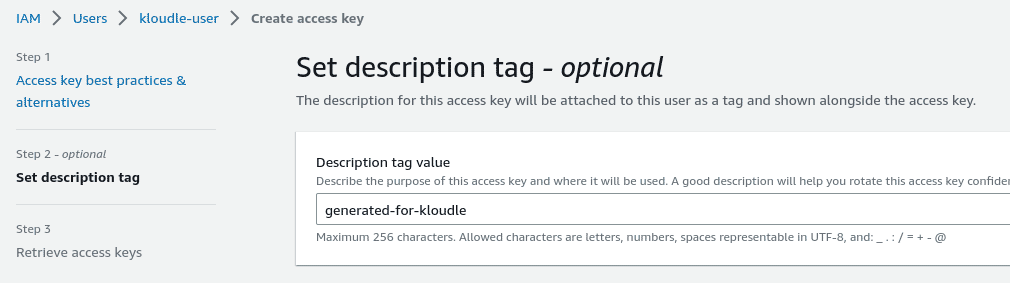
-
Download the csv file containing the user credentials
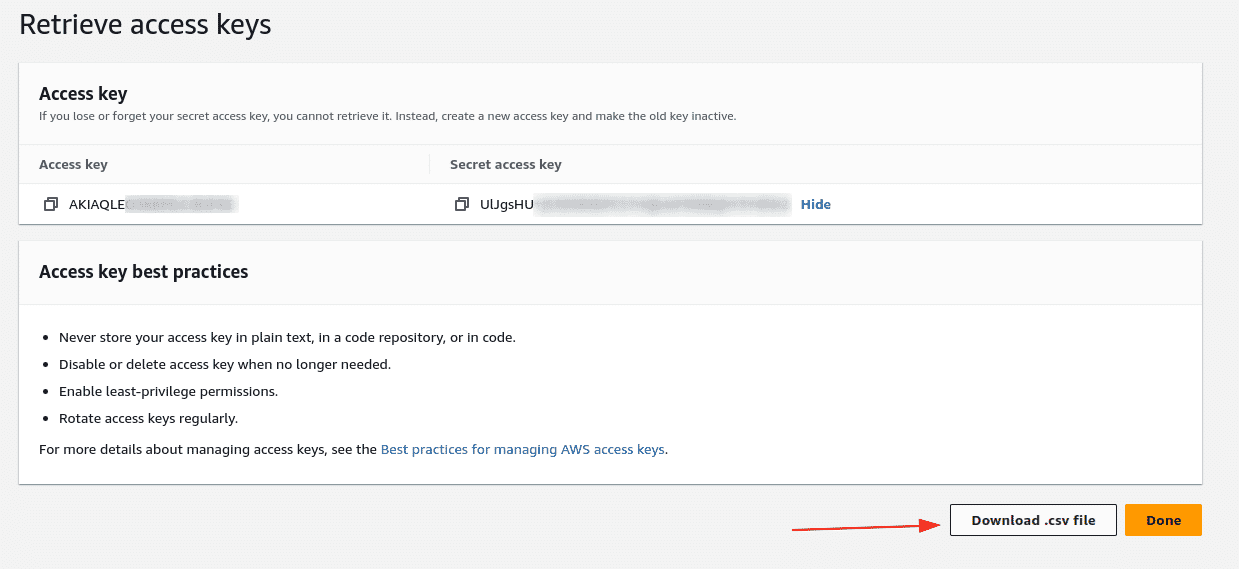
-
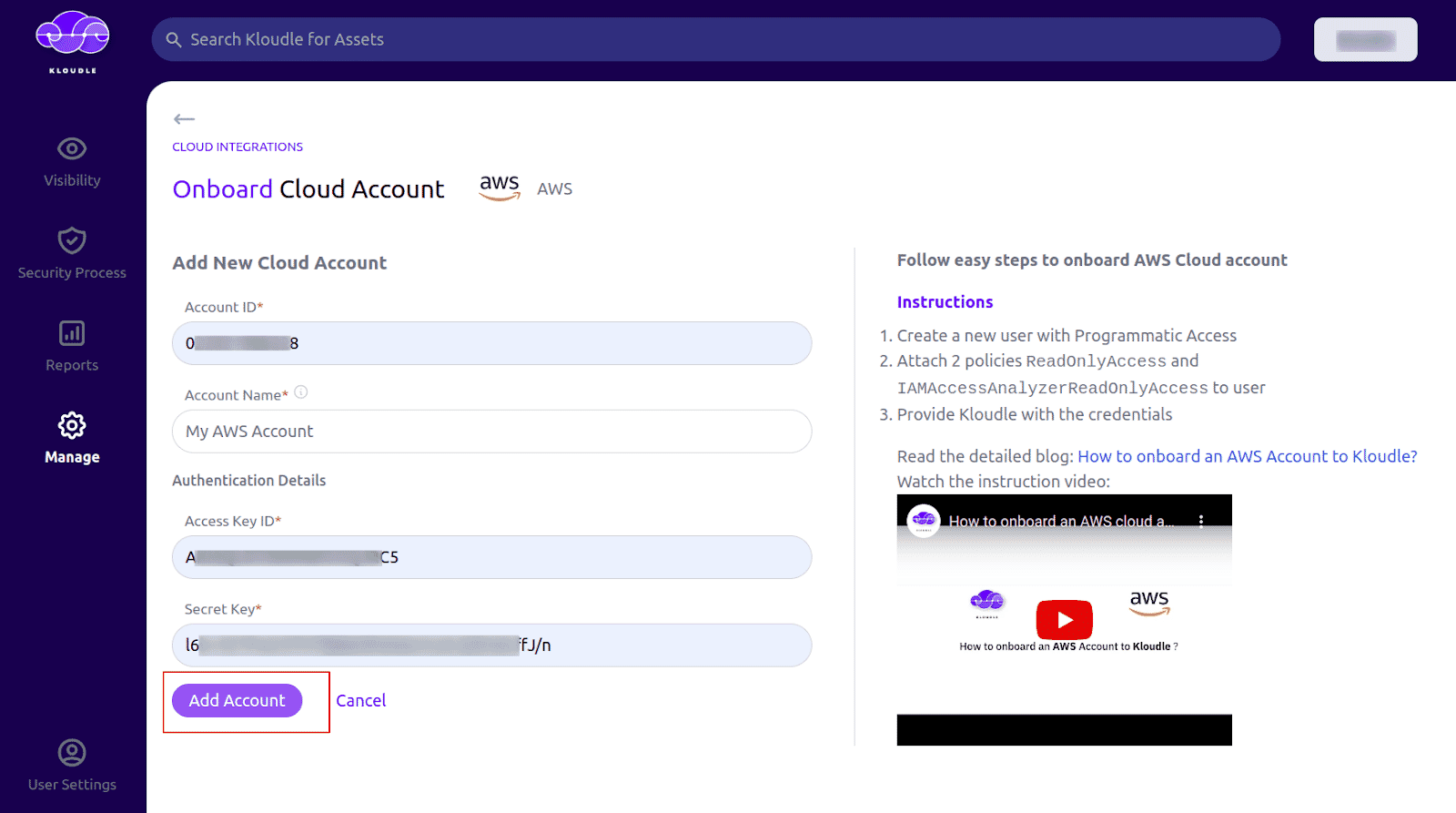
Now in Kloudle dashboard, go to Manage and click on AWS under Cloud Integrations
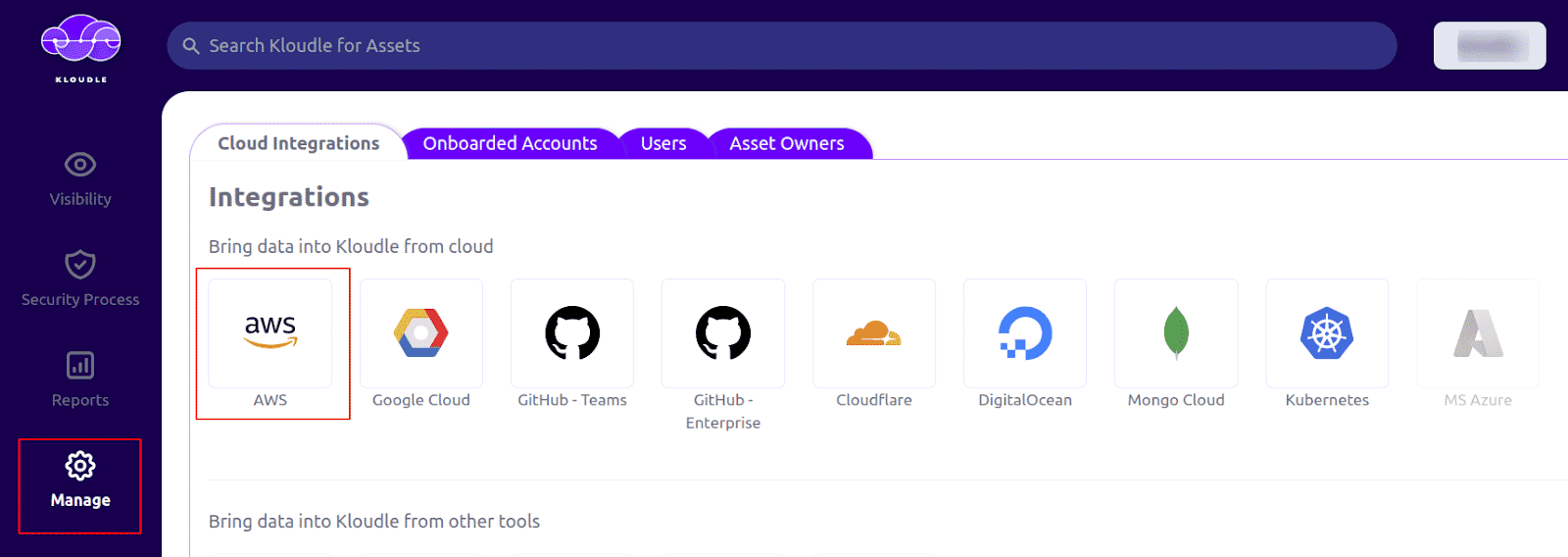
-
On the onboarding screen, enter your AWS Account ID for which the credentials were generated
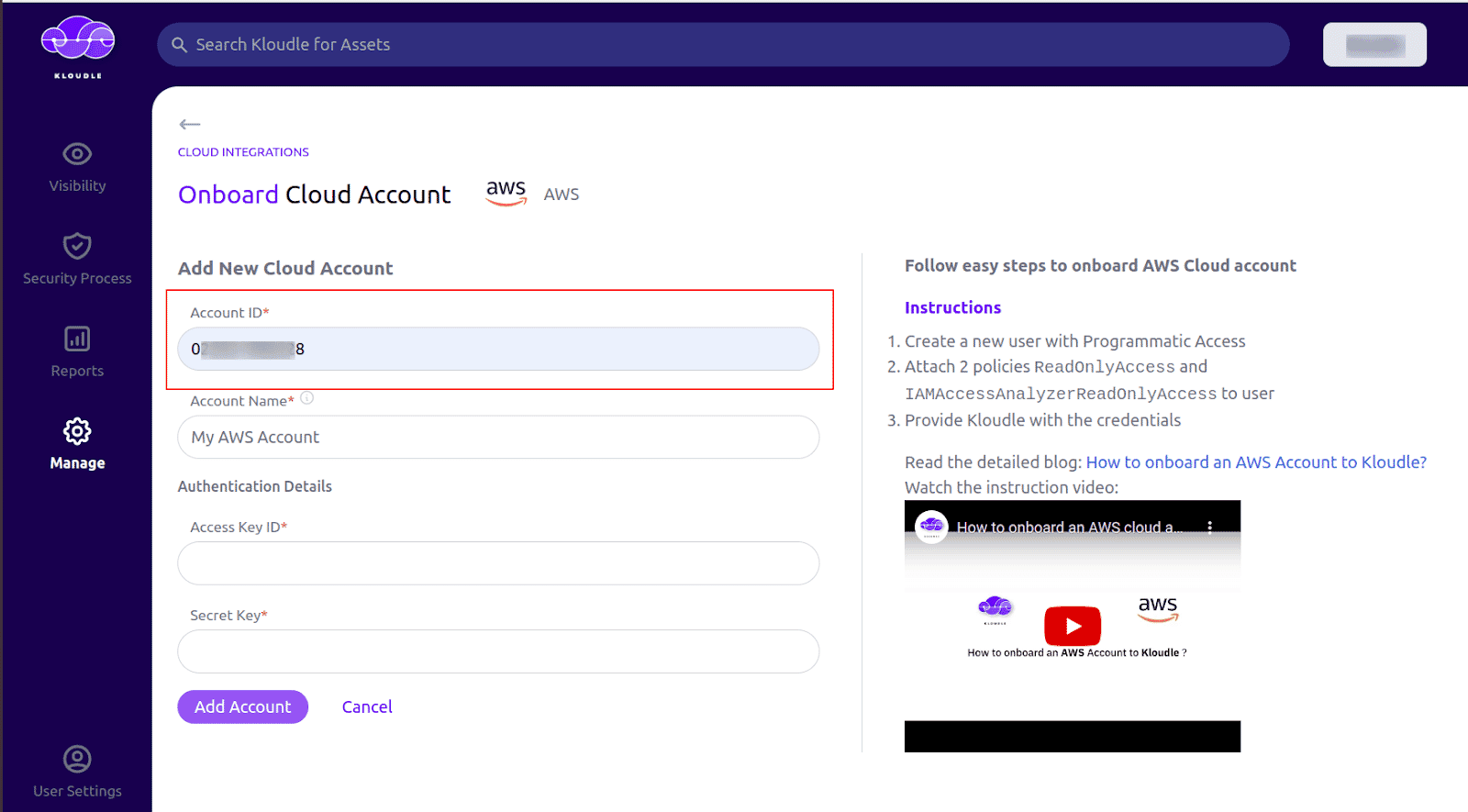
-
You can give a custom name for your AWS account under Account Name
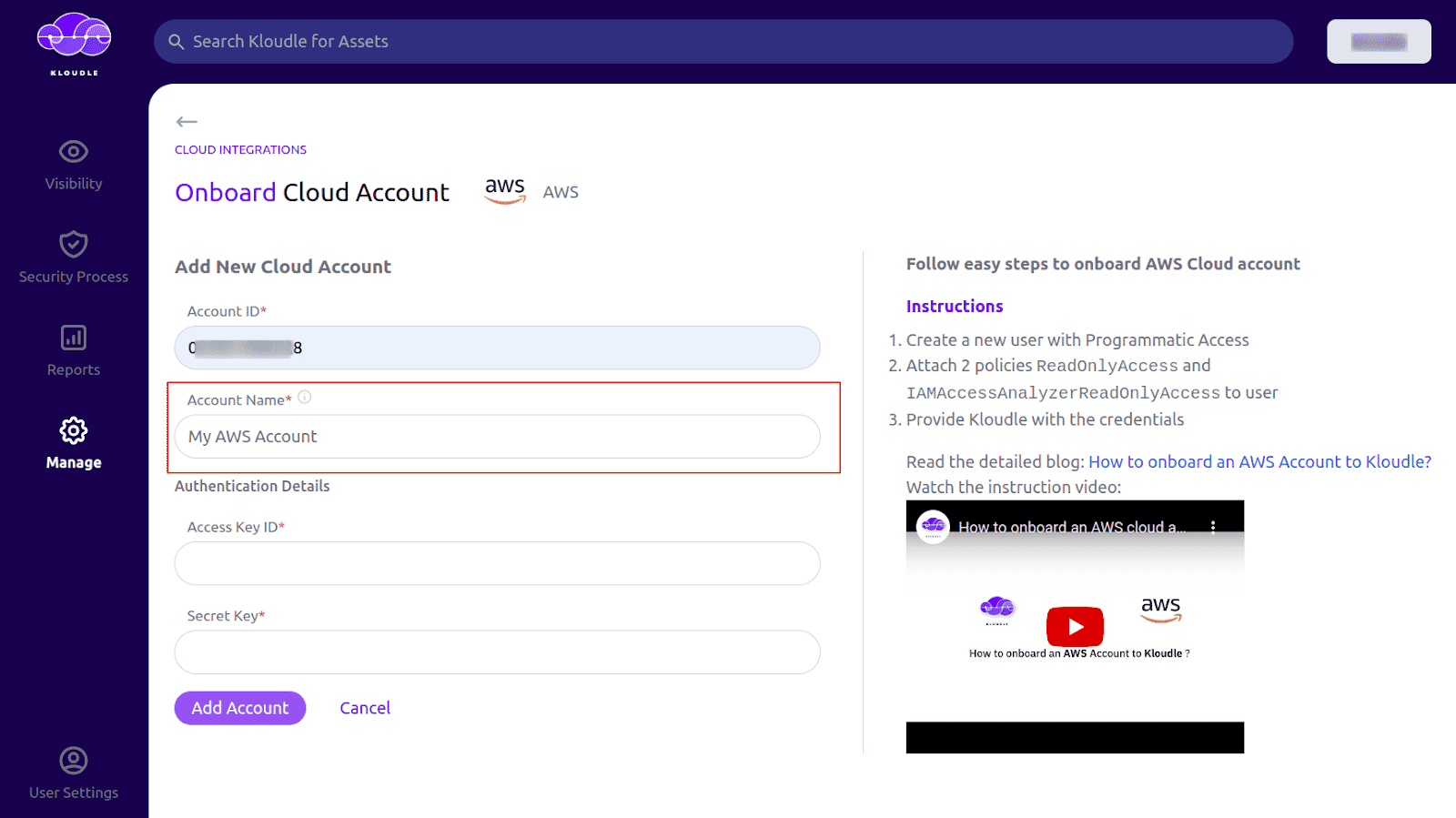
-
Under Authentication Details, provide the Access Key ID and Secret Key
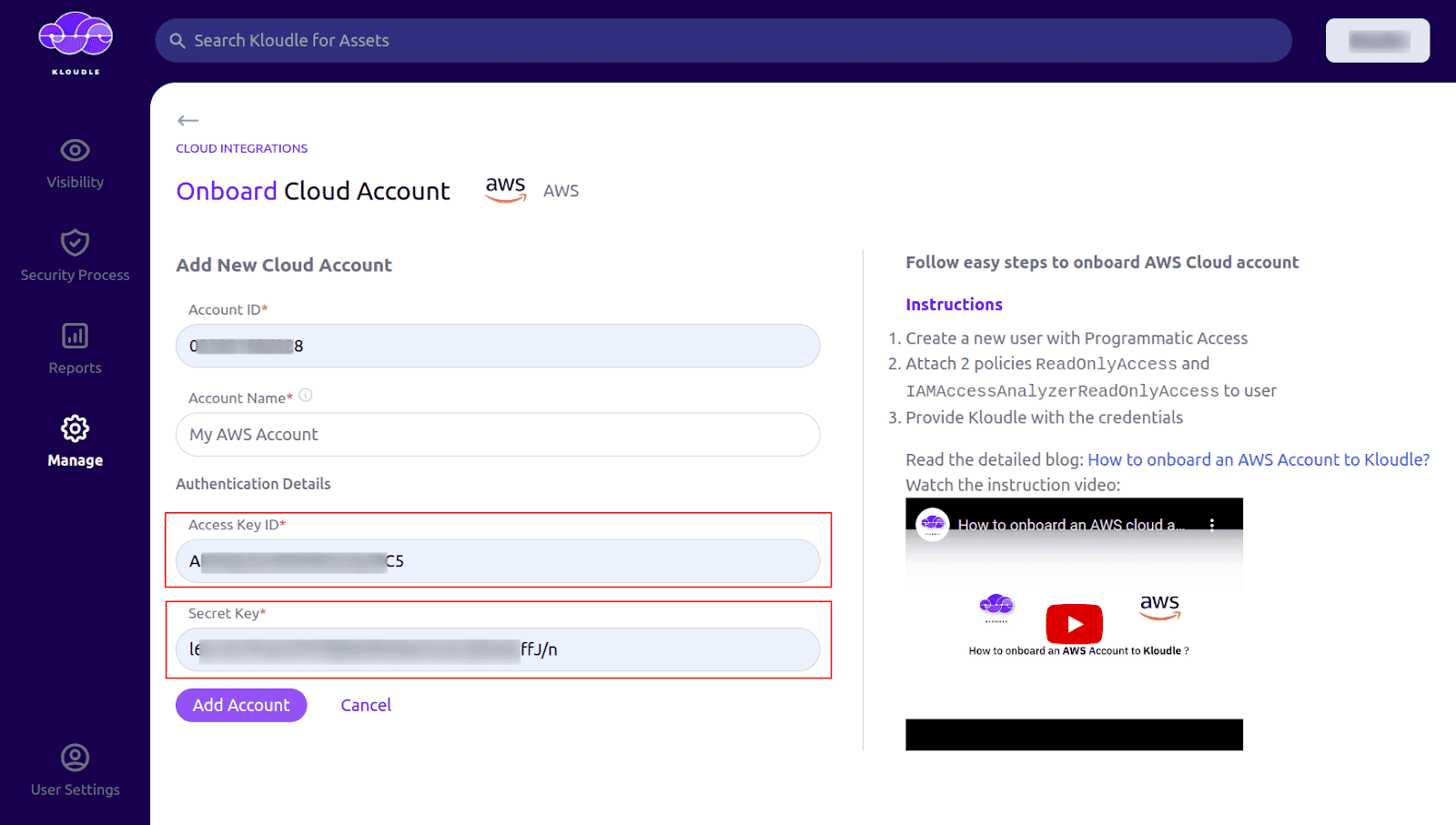
-
Click on Add Account button to onboard your AWS account to Kloudle
Through CLI
-
Ensure you have your CLI credentials to access the AWS account you want to onboard
-
Ensure you have permissions to create an IAM user and attach policies to the user
-
Run the below command to create the user kloudle-user,
aws iam create-user —user-name kloudle-user —tags Key=createdfor,Value=kloudle
-
Then we will create access key for the user
aws iam create-access-key —user-name kloudle-user
-
Note down the Access Key ID and Secret Access Key for the user
-
Now we can attach the required policies ReadOnlyAccess and IAMAccessAnalyzerReadOnlyAccess to the user
aws iam attach-user-policy —user-name kloudle-user —policy-arn arn:aws:iam::aws:policy/ReadOnlyAccess
aws iam attach-user-policy —user-name kloudle-user —policy-arn arn:aws:iam::aws:policy/IAMAccessAnalyzerReadOnlyAccess
-
We can verify that the permissions are attached to the user by running list-attached-user-policies
aws iam list-attached-user-policies —user-name kloudle-user
Once you have created the kloudle-user and noted down the Access Key ID and Secret Key for it, you can proceed with the onboarding steps on Kloudle as mentioned from Step 14 onwards in the previous section “Through Console”.
Video Instructions
Here’s a video that shows how you can do this.

Riyaz Walikar
Founder & Chief of R&D
Riyaz is the founder and Chief of R&D at Kloudle, where he hunts for cloud misconfigurations so developers don’t have to. With over 15 years of experience breaking into systems, he’s led offensive security at PwC and product security across APAC for Citrix. Riyaz created the Kubernetes security testing methodology at Appsecco, blending frameworks like MITRE ATT&CK, OWASP, and PTES. He’s passionate about teaching people how to hack—and how to stay secure.

Riyaz Walikar
Founder & Chief of R&D
Riyaz is the founder and Chief of R&D at Kloudle, where he hunts for cloud misconfigurations so developers don’t have to. With over 15 years of experience breaking into systems, he’s led offensive security at PwC and product security across APAC for Citrix. Riyaz created the Kubernetes security testing methodology at Appsecco, blending frameworks like MITRE ATT&CK, OWASP, and PTES. He’s passionate about teaching people how to hack—and how to stay secure.