- What is Kloudle?
- Requirements to get started
- Kubernetes Cluster Onboarding to Kloudle
- External cluster - Standalone Kubernetes Platform Onboarding steps for Kloudle
- Internal cluster - Standalone Kubernetes Platform Onboarding steps for Kloudle
- Video Instructions
What is Kloudle?
Kloudle is a Digital Assets Security Automation Platform for SREs and DevOps. When integrated with your Cloud or SaaS provider, Kloudle takes periodic security snapshots and provides complete security contextual visibility that allows you to make informed decisions about your infrastructure, the assets and their various configurations.
Kloudle collects metadata about the resources and analyzes them to identify misconfigurations and using a massive research powered knowledgebase, identifies what would go wrong if these misconfigurations were exploited and what you can do to fix them.
As part of making sure the lives of SREs and DevOps become easier, Kloudle offers the ability to create “rules” that allow a user to take automated actions against a baseline. These automated actions, which we call Security Processes, allow users to configure a series of steps that kick in when custom events occur to ensure the security of the monitored cloud and SaaS platform.
Requirements to get started
To onboard your standalone Kubernetes cluster to Kloudle, you need to have the following prerequisites ready to create the credentials required to onboard:
- A kubernetes administrator or user with the ability to create resources at cluster level, is required to run the shell script as it invokes kubectl with your saved user credentials
- Ensure your kubeconfig cluster context is set correctly since the script creates resources in the current context. You can verify this using kubectl cluster-info
Kubernetes Cluster Onboarding to Kloudle
A Kubernetes cluster can exist as an external cluster (with a reachable public IP address) or as an internal cluster accessible through a private network. This blogpost covers instructions for both the type of setups.
External cluster - Standalone Kubernetes Platform Onboarding steps for Kloudle
These instructions are for an external cluster with a public IP address.
The credentials required by Kloudle to onboard a standalone Kubernetes cluster is the kubeconfig of a service account with read only access. We have published a script that allows for the generation of the required kubeconfig.yml that needs to be supplied to the Kloudle app.
Command to Execute
- Launch a terminal window and run
kubectl cluster-infoto ensure you are using the correct target cluster. - If Step 1 shows the correct cluster, run the following command
curl -sS https://raw.githubusercontent.com/Kloudle/kloudle-kubernetes-onboarding/master/kubernetes-readonly-admin-creator.sh | sh
Paste the output in the Kubernetes Onboarding page under “Manage” > “Kubernetes”, in the Kloudle app, as shown below
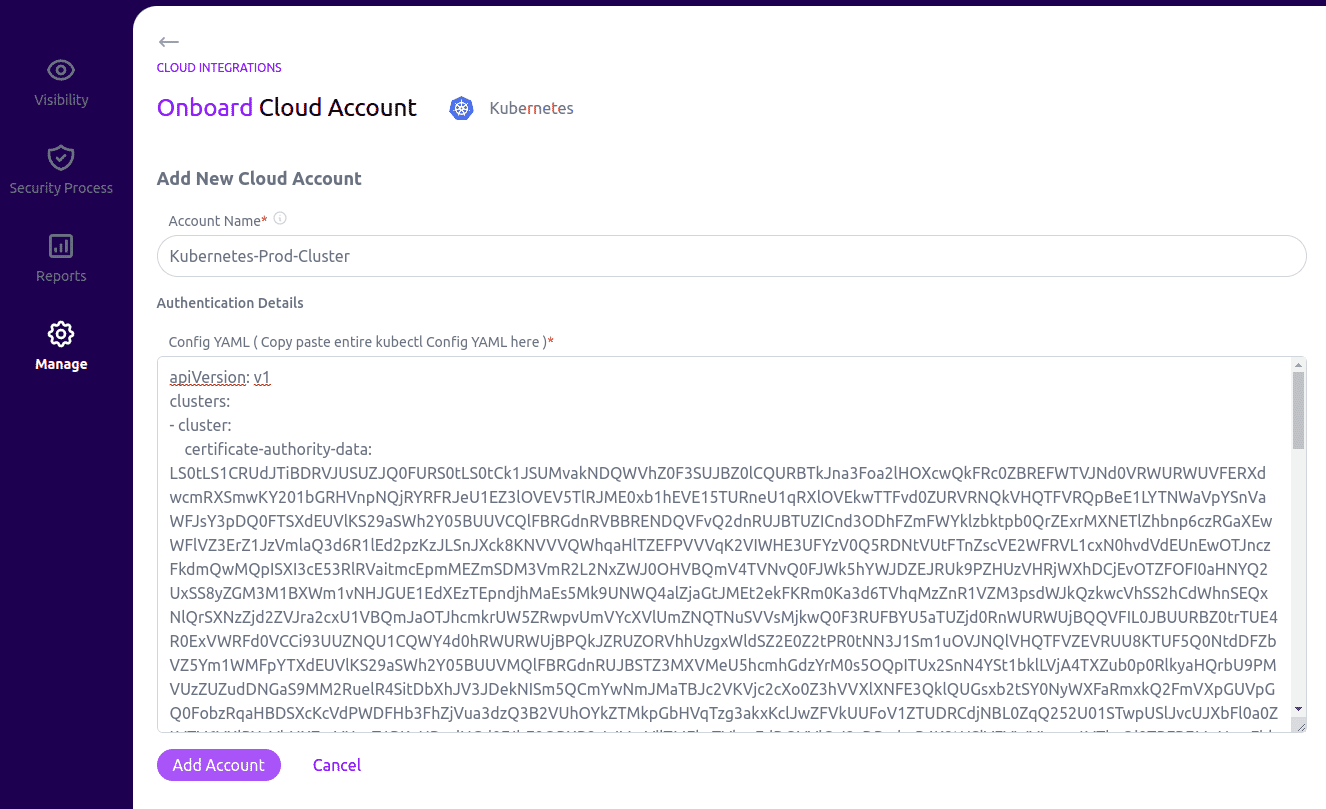
Click on Add Account to complete the onboarding.
What does the Command do?
The command, executed in the previous section, pulls a shell script hosted in the Kloudlekloudle-kubernetes-onboarding GitHub repository and executes it with sh.
The script uses the locally configured Kubernetes credentials to create the following readonly resources in the target cluster and prints a kubeconfig that is used to onboard the Kubernetes cluster to Kloudle.
- A ReadOnly ClusterRole
- A ClusterRoleBinding for the ClusterRole
- A Service Account
- A Secret Token for the Service Account
Internal cluster - Standalone Kubernetes Platform Onboarding steps for Kloudle
These instructions are for an internal cluster without a public IP address. This setup uses a bastion host (commonly called jumpbox) to reach the Kubernetes cluster.
The credentials required by Kloudle to onboard a standalone Kubernetes cluster is the kubeconfig of a service account with read only access. We have published a script that allows for the generation of the required kubeconfig.yml that needs to be supplied to the Kloudle app.
Additional requirements to get started
-
Either set up a new small instance or SSH to an existing machine that will be used as the jumphost. Ubuntu 20.04 and above preferred.
-
This machine needs to fulfil the following requirements
- This machine needs to be able to reach the internal Kubernetes cluster
- This machine must be reachable from the Internet
- The machine must allow traffic from 34.173.52.204 to reach TCP port 8443
Command to Execute
The following commands are to be run on the bastion host
- Launch a terminal window and run
kubectl cluster-infoto ensure you are using the correct target cluster. - If Step 1 shows the correct cluster, run the following command
curl -sS https://raw.githubusercontent.com/Kloudle/kloudle-kubernetes-onboarding/master/kubernetes-jumpbox-proxy-readonly-admin-setup.sh | sh
- Paste the Proxy IP address as shown in the output of the command
- Paste the output in the Kubernetes Onboarding page under “Manage” > “Kubernetes”, in the Kloudle app, as shown below
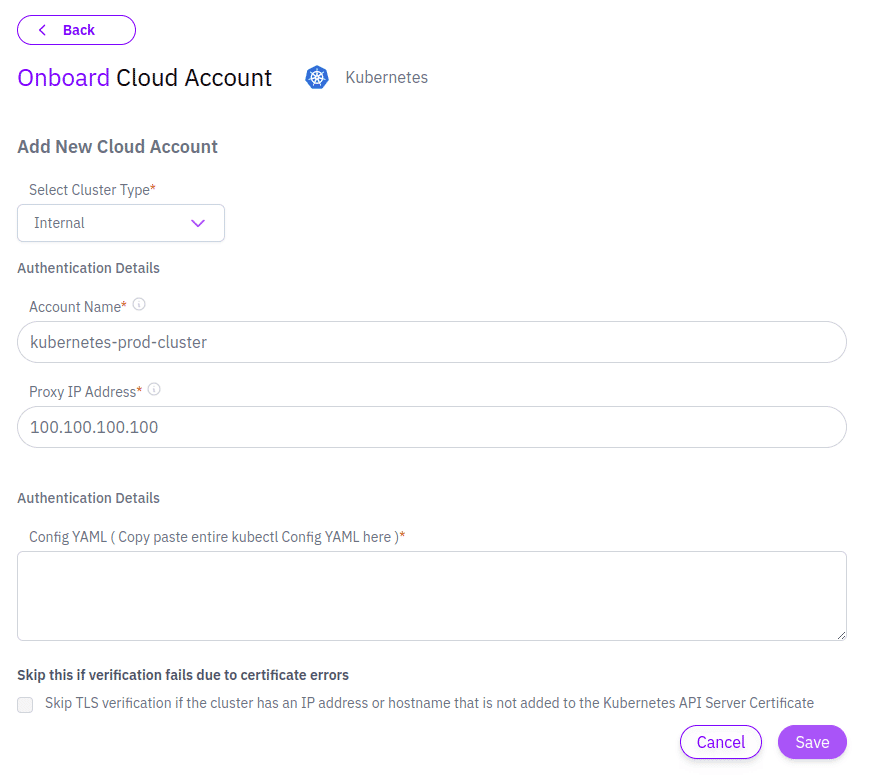
Click on Add Account to complete the onboarding.
What does the Command do?
The command, executed in the previous section, pulls a shell script hosted in the Kloudlekloudle-kubernetes-onboarding GitHub repository and executes it with sh.
The script then sets up Tinyproxy to act as a HTTP/HTTPS proxy to reach the cluster and then creates the following readonly resources in the target internal cluster and prints a kubeconfig that is used to onboard the Kubernetes cluster to Kloudle.
- A ReadOnly ClusterRole
- A ClusterRoleBinding for the ClusterRole
- A Service Account
- A Secret Token for the Service Account
Video Instructions

Riyaz Walikar
Founder & Chief of R&D
Riyaz is the founder and Chief of R&D at Kloudle, where he hunts for cloud misconfigurations so developers don’t have to. With over 15 years of experience breaking into systems, he’s led offensive security at PwC and product security across APAC for Citrix. Riyaz created the Kubernetes security testing methodology at Appsecco, blending frameworks like MITRE ATT&CK, OWASP, and PTES. He’s passionate about teaching people how to hack—and how to stay secure.

Riyaz Walikar
Founder & Chief of R&D
Riyaz is the founder and Chief of R&D at Kloudle, where he hunts for cloud misconfigurations so developers don’t have to. With over 15 years of experience breaking into systems, he’s led offensive security at PwC and product security across APAC for Citrix. Riyaz created the Kubernetes security testing methodology at Appsecco, blending frameworks like MITRE ATT&CK, OWASP, and PTES. He’s passionate about teaching people how to hack—and how to stay secure.