What is Kloudle?
Kloudle is a Digital Assets Security Automation Platform for SREs and DevOps. When integrated with your Cloud or SaaS provider, Kloudle takes periodic security snapshots and provides complete security contextual visibility that allows you to make informed decisions about your infrastructure, the assets and their various configurations.
Kloudle collects metadata about the resources and analyzes them to identify misconfigurations and using a massive research powered knowledgebase, identifies what would go wrong if these misconfigurations were exploited and what you can do to fix them.
As part of making sure the lives of SREs and DevOps become easier, Kloudle offers the ability to create “rules” that allow a user to take automated actions against a baseline. These automated actions, which we call Security Processes, allow users to configure a series of steps that kick in when custom events occur to ensure the security of the cloud and SaaS platform being monitored.
Quay.io onboarding for Kloudle
Prerequisites
To onboard a Quay.io cloud account to Kloudle, an OAuth2 Access Token needs to be generated. This token can be generated from an Application that is created within Quay.io in any organisation.
Regardless of which organisation you create the Application in, the token that is generated will always act on behalf of the logged in user.
Steps to onboard Quay.io to Kloudle
Following are the steps to create an OAuth2 Token on Quay.io to onboard the account..
-
Login to the Quay.io dashboard at https://quay.io/
-
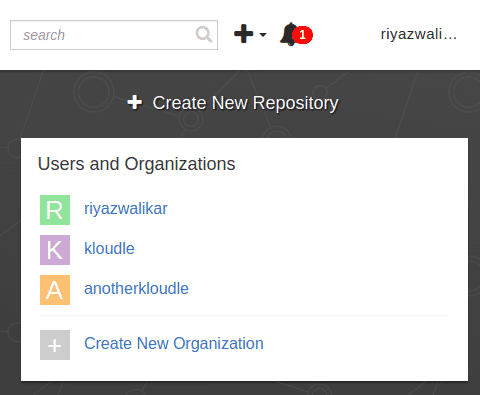
On the right side of the screen, select any organisation. Organisations have a URL of the form - https://quay.io/organization/ORGNAME
-
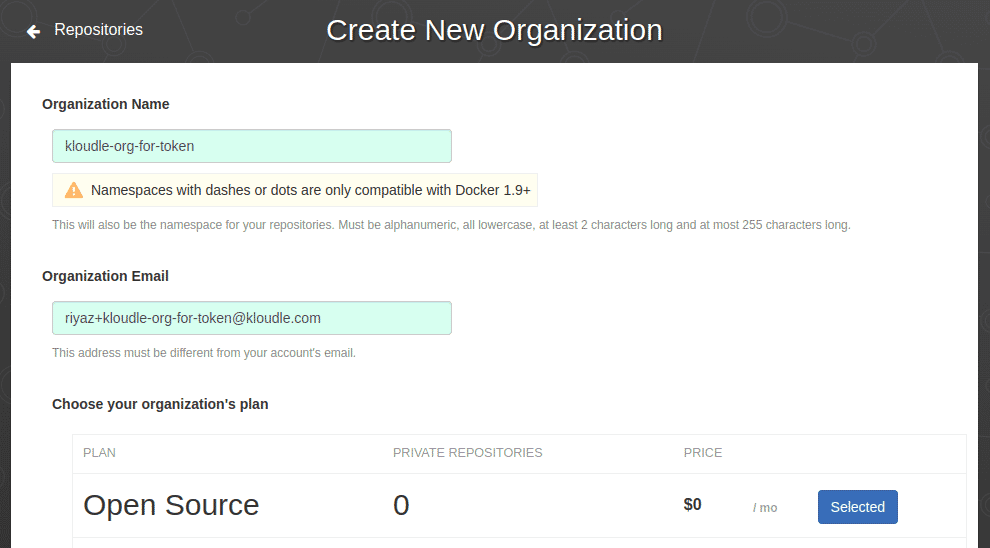
If no organisations exist, create a new organisation under the “Open Source” plan for the sake of generating the token. Note the name of the organisation.
-
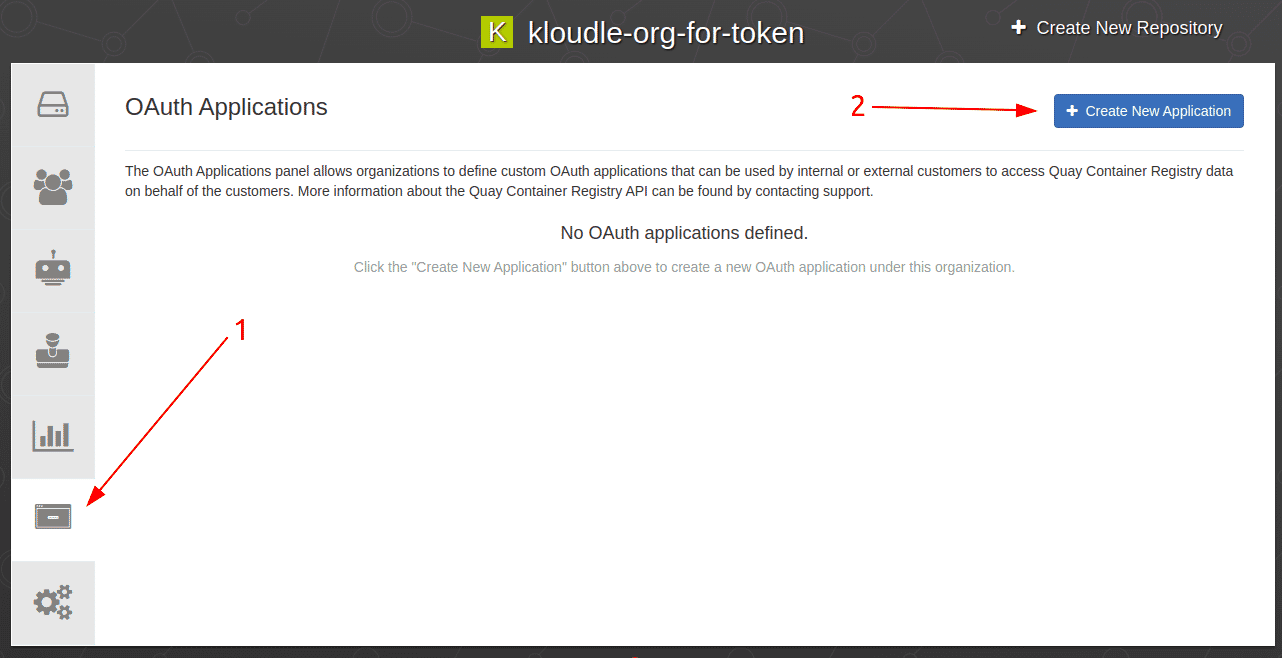
In the Organisation selection, click on the “OAuth Applications” menu and click on the “Create New Application” button.
-
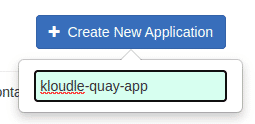
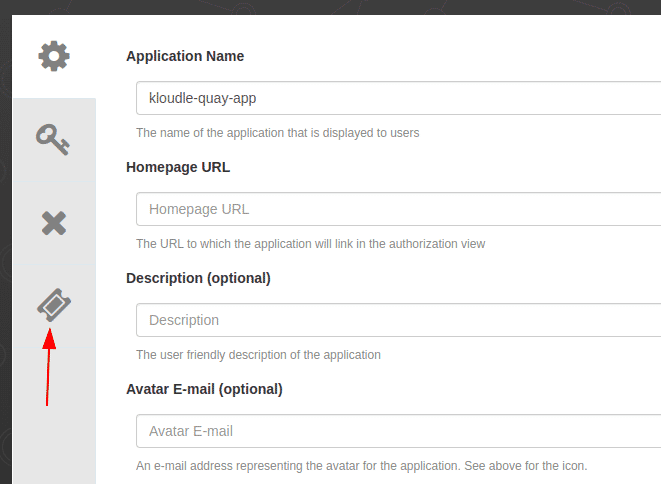
Give the app the name “kloudle-quay-app”
-
Once the application is created, click on the app name and select the “Generate Token” menu.
-
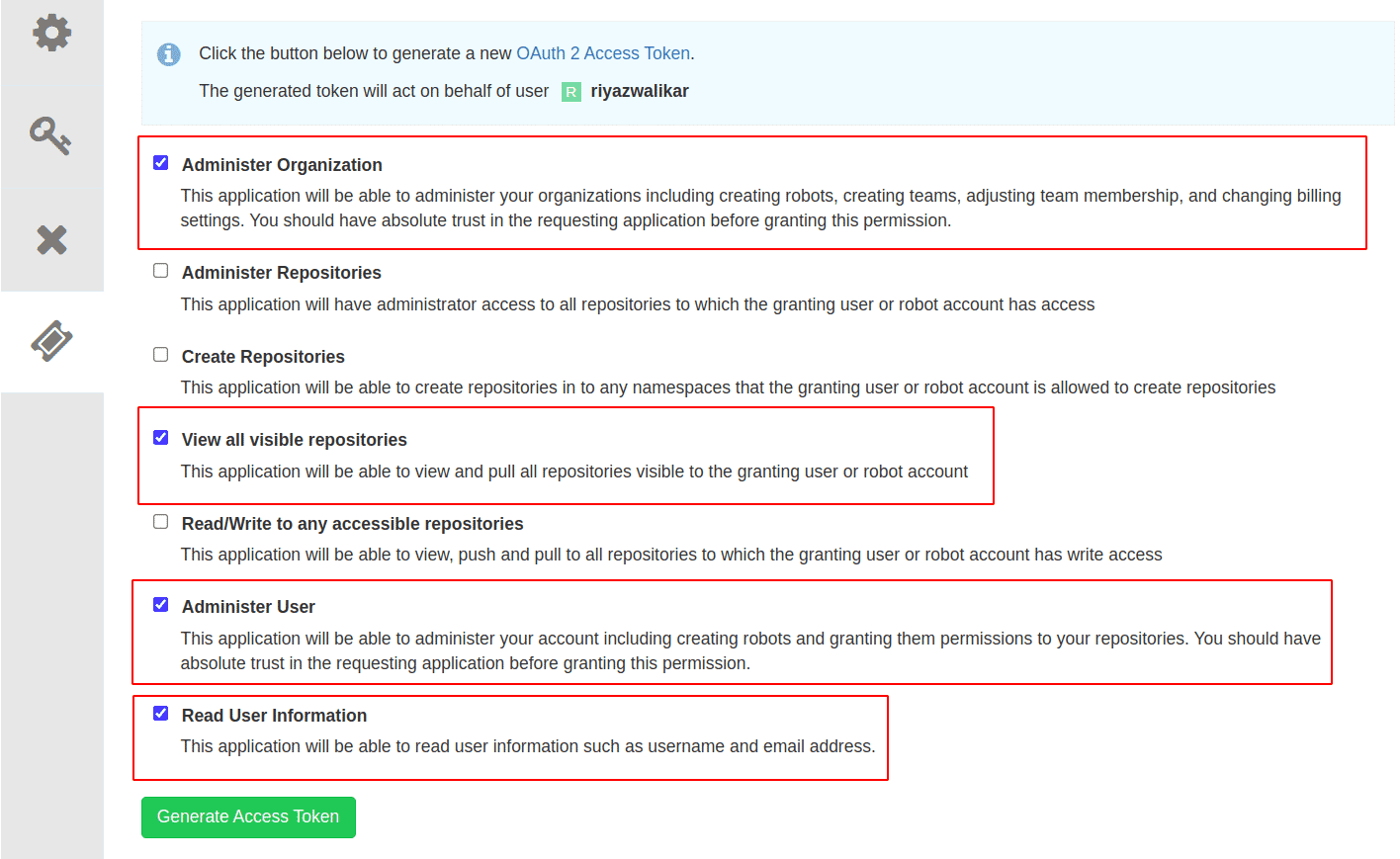
Select the following permissions
- Administer Organization (required for organization level visibility, including teams and their permissions)
- View all visible repositories (required for repository visibility)
- Administer User (required for visibility into robot accounts and permissions)
- Read User Information (required for visibility of user information)
-
Click the “Generate Access Token” button.
-
A new tab will open to request Authorization. Click on “Authorize Application” to generate the token.
-
Copy the token shown and add it to Kloudle via the onboarding window. This token cannot be recovered if the window is closed, so make sure this is copied.
-
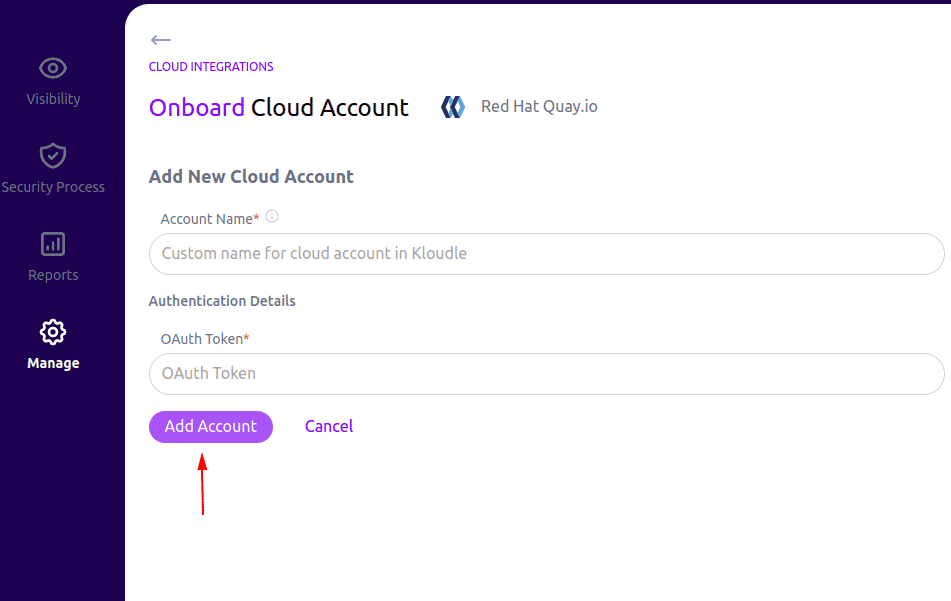
Now in the Kloudle dashboard, go to Manage and click on Red Hat Quay.io under Cloud Integrations.

-
Provide the Account name and OAuth Token we copied in step 10
-
Click on Add Account to complete the setup.
Video Instructions

Riyaz Walikar
Founder & Chief of R&D
Riyaz is the founder and Chief of R&D at Kloudle, where he hunts for cloud misconfigurations so developers don’t have to. With over 15 years of experience breaking into systems, he’s led offensive security at PwC and product security across APAC for Citrix. Riyaz created the Kubernetes security testing methodology at Appsecco, blending frameworks like MITRE ATT&CK, OWASP, and PTES. He’s passionate about teaching people how to hack—and how to stay secure.

Riyaz Walikar
Founder & Chief of R&D
Riyaz is the founder and Chief of R&D at Kloudle, where he hunts for cloud misconfigurations so developers don’t have to. With over 15 years of experience breaking into systems, he’s led offensive security at PwC and product security across APAC for Citrix. Riyaz created the Kubernetes security testing methodology at Appsecco, blending frameworks like MITRE ATT&CK, OWASP, and PTES. He’s passionate about teaching people how to hack—and how to stay secure.