Introduction
(This is the last of a 9 part blog series that explains the Kubernetes MITRE ATT&CK like Threat Matrix created by Microsoft from an attacker perspective and attempts to provide how real world attackers use the techniques covered in the framework to gain access, execute, persist and explore Kubernetes cluster environments.)
Use this index to navigate to and read the rest of the posts in this series
- Part 1 - Initial access
- Part 2 - Execution
- Part 3 - Persistence
- Part 4 - Privilege escalation
- Part 5 - Defense evasion
- Part 6 - Credential access
- Part 7 - Discovery
- Part 8 - Lateral movement
(This blog post discusses the last tactic described in the MITRE ATT&CK framework for Kubernetes - Impact)
In the last post, we saw the techniques in the Lateral Movement tactic of the MITRE ATT&CK framework for Kubernetes. Let’s look at the next tactic, Impact and the techniques that attackers use within this tactic. For reference, here’s the framework that Microsoft created as a visual cue to the overall tactics and techniques that attackers use when attacking a Kubernetes cluster.
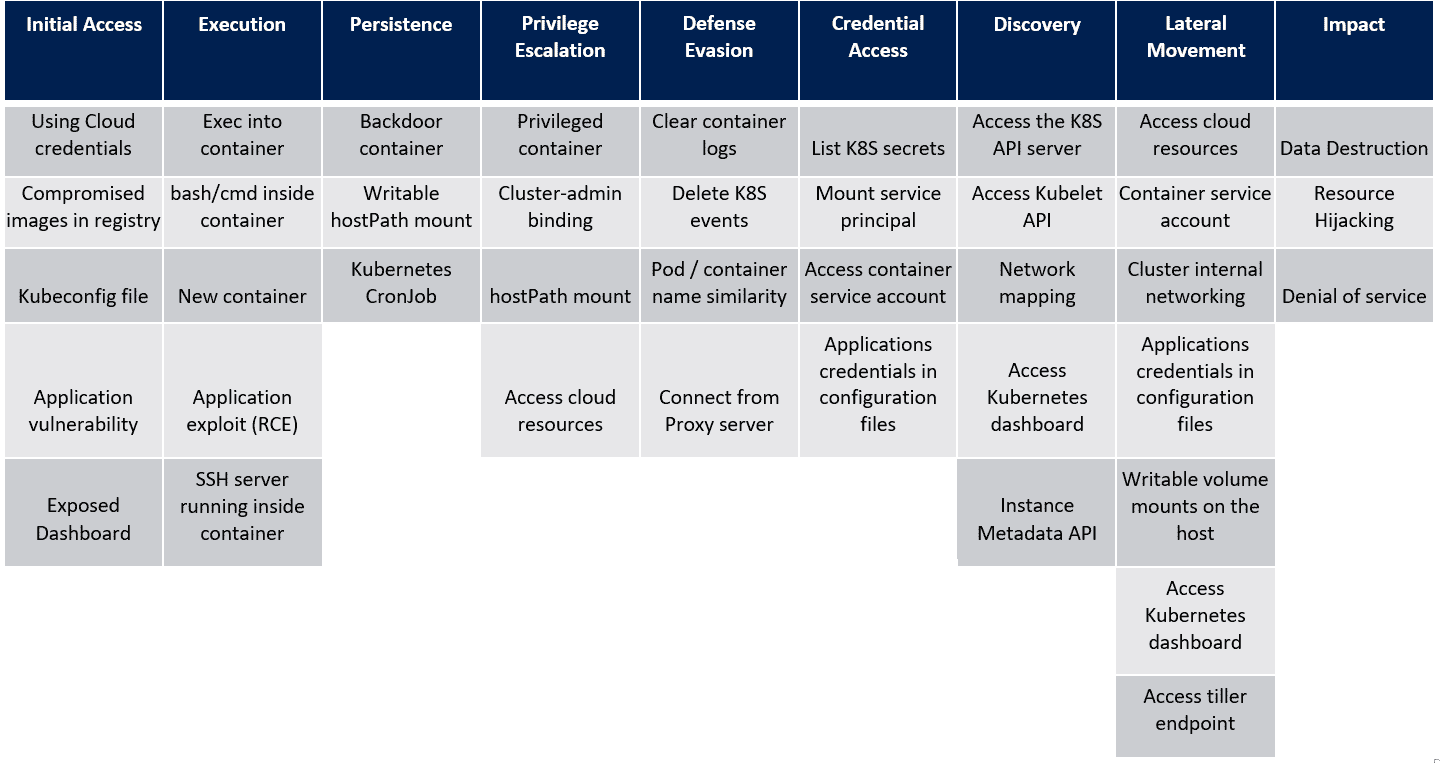
Impact
The Impact tactic simply describes techniques that are used by attackers to destroy data, abuse access or change the cluster environment in a way to cause a Denial of Service for legitimate users. The techniques that the Impact tactic describes are more consequences of malicious actions that an attacker takes rather than being actual ways of executing the actions that lead the described outcomes.
Data destruction
An attacker, with full cluster control, can scale down deployments, delete storage volumes, terminate running pods, drain nodes or delete any data that is accessible via running services etc.
For example, an attacker could use the credentials obtained from configuration files or the Kubernetes secrets store to connect to a MySQL server and issue DROP DATABASE commands.
Resource Hijacking
This is one of the most common consequences of a cluster compromise, especially for managed instances on the cloud. Attackers gain control of compromised resources and use them to run attacker chosen tasks, like cryptocurrency mining for example.
Denial of service
A Denial of Service would occur when legitimate users of applications running within the cluster are unable to access them. That would additionally be true of any resource object within the cluster. An attacker simply makes the resource unavailable to users by removing the resources, altering its configuration so that it no longer becomes accessible or by updating the resource in a way that it changes the meaning of the resource entirely.
Conclusion
With the Impact tactic, an attacker attempts to prevent the cluster from serving its primary purpose of servicing the users of the cluster. Attackers can destroy data, alter the state of data and resources, make them inaccessible to cause a denial of service or simply hijack the resources to perform malicious pre-orchestrated tasks like cryptocurrency mining and malware hosting.
The MITRE ATT&CK threat matrix serves as a guide to defenders as well as authorized security testers that can be used to understand how an attack could occur on a cluster going all the way from obtaining Initial Access to performing destructive actions via the Impact tactic.
References
This article is brought to you by Kloudle Academy, a free e-resource compilation, created and curated by Kloudle. Kloudle is a cloud security management platform that uses the power of automation and simplifies human requirements in cloud security. If you wish to give your feedback on this article, you can write to us here.

Riyaz Walikar
Founder & Chief of R&D
Riyaz is the founder and Chief of R&D at Kloudle, where he hunts for cloud misconfigurations so developers don’t have to. With over 15 years of experience breaking into systems, he’s led offensive security at PwC and product security across APAC for Citrix. Riyaz created the Kubernetes security testing methodology at Appsecco, blending frameworks like MITRE ATT&CK, OWASP, and PTES. He’s passionate about teaching people how to hack—and how to stay secure.

Riyaz Walikar
Founder & Chief of R&D
Riyaz is the founder and Chief of R&D at Kloudle, where he hunts for cloud misconfigurations so developers don’t have to. With over 15 years of experience breaking into systems, he’s led offensive security at PwC and product security across APAC for Citrix. Riyaz created the Kubernetes security testing methodology at Appsecco, blending frameworks like MITRE ATT&CK, OWASP, and PTES. He’s passionate about teaching people how to hack—and how to stay secure.