Technology can simplify life but also opens the door to cyberattacks. As attacks become more sophisticated and targeted, businesses need to stay ahead by conducting regular security audits. This way, they can spot misconfigurations and vulnerabilities before they can be exploited.
Misconfigurations occur when cloud configurations are incorrect and data security best practices are not followed. With regular audits, you can detect and fix these issues to prevent cyberattacks and operational issues.
In this article, we will explore the importance of proactive security audits and how they protect organizations from modern cyber threats. We will also outline practical steps for maintaining a secure cloud environment.
Audits Identify Deviations from Baselines
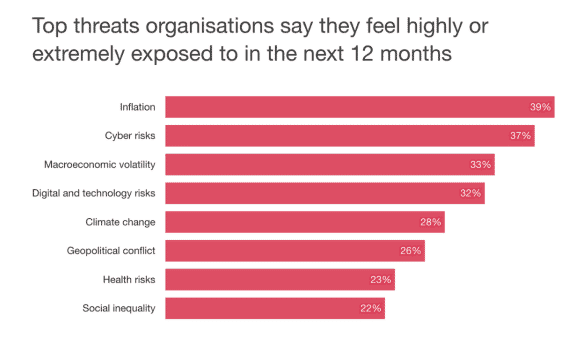
With 37% of organizations reporting they felt exposed to cyber risks, it is crucial to prioritize regular audits. Audits are key for spotting deviations from established baselines by helping organizations identify unauthorized changes or misconfigurations that could lead to security risks. Regularly identifying these deviations ensures that systems are secure, compliant, and optimized.
It Lets You Compare Configurations to Standards
With audits, you compare configurations to standards to ensure systems remain aligned with security best practices and reduce the risk of vulnerabilities. By regularly checking configurations, organizations can ensure consistency, avoid compliance issues, and quickly identify areas needing remediation.
Here’s how businesses can effectively compare configurations to standards
- Create a comprehensive baseline for your network settings, such as setting specific firewall rules, user permissions, and software versions, and document these configurations in detail.
- Implement tools like Ansible or Chef to manage and enforce configuration settings across your servers automatically. These tools maintain consistency and minimize manual errors.
- Schedule monthly checks to review and verify server configurations against your baseline. You can confirm that security patches and updates are applied consistently across all systems.
It Helps Detect Unauthorized Changes
Regular audits help protect businesses’ system integrity and security by detecting unauthorized changes. Monitor for such changes to ensure accountability, compliance, and quick response to potential security breaches to prevent vulnerabilities from being introduced.
Try the following tips to help in detecting unauthorized changes
- Use software like Tripwire or OSSEC to detect and report unauthorized system configuration changes automatically.
- Perform detailed reviews of your system settings, such as verifying the configuration of your web servers or network devices every quarter.
- Configure your monitoring systems to send instant alerts via email or SMS if unauthorized changes are detected in critical files or system settings.
- Among the best practices for maintaining cloud security is to use logging systems to record every change made to your system configurations, including who made the change, what was altered, and when it occurred.
- Restrict access to configuration settings to only authorized personnel, using role-based access controls and multi-factor authentication to ensure security.
Audits Ensure Compliance with Security Policies
Maintain a strong defense against potential threats by employing audits that ensure that all security policies are enforced. With 73% of organization leaders agreeing that cyber and privacy regulations are effective in reducing cyber risks, aligning your systems with these regulations through regular audits ensures your organization meets its security goals and effectively mitigates risks.
Check Alignment with Security Policies
Check your businesses’ alignment with security policies by doing the following
- Create detailed security guidelines covering every aspect of your IT infrastructure, such as network security, data protection, and access controls.
- Deploy security tools like Qualys or Nessus to continuously monitor and report on whether your systems adhere to your security policies.
- Focus on the most critical systems, such as databases and application servers, to ensure they are fully aligned with your security policies.
- Perform internal audits every six months to review how well your systems and processes align with your security policies.
Ensure Industry Regulations are Met
Audits ensure compliance with industry regulations and safeguard your organization from potential penalties or fines. When you earn an online computer science degree, you learn about audits that equip professionals with the expertise to thoroughly assess systems and maintain security. By conducting audits, organizations demonstrate their commitment to secure and compliant operations. This, in turn, reinforces trust with customers and stakeholders.
Take note of the following to guarantee meeting industry regulations
- Research and pinpoint specific regulations such as GDPR for data protection or PCI DSS for payment card security that govern your industry.
- Schedule and execute audits at least annually to ensure adherence to relevant regulations and standards.
- Hire external experts to perform unbiased assessments and provide an objective review of your compliance status.
It Assesses Patch Management
Identify security gaps faster through audits to assess patch management. Regular audits ensure patches are applied properly. This also protects systems from threats and ensures operational integrity.
Review Applied Patches and Updates
Spot misconfiguration by following these steps on reviewing applied patches and updates
- Keep Detailed Records of All Applied Patches. Maintain a log of every patch installed, including dates and versions, for tracking and compliance purposes.
- Use Automated Patch Management Tools. Deploy software solutions that automate the process of discovering, downloading, and installing patches across your systems.
- Conduct Post-Patch Vulnerability Scans. After applying patches, run vulnerability scans to ensure they effectively address the intended security issues without introducing new vulnerabilities.
Identify Missing or Outdated Patches
Proactivity is always key. Make it a habit to identify missing or outdated patches to prevent vulnerabilities from being exploited. This proactive approach reduces risks and ensures compliance with security regulations.
Do the following to easily identify missing or outdated patches
- Conduct regular vulnerability scans to identify potential weaknesses.
- Use patch management tools to receive real-time alerts about available updates.
- Maintain an inventory of all systems and software to track patch needs.
- Prioritize patching for critical systems and high-risk vulnerabilities.
- Establish clear timelines and policies for applying patches.
IT Evaluates Access Controls
Audits of access controls are vital to prevent unauthorized access to sensitive data. They verify configurations, reduce security risks, and ensure compliance.
Verify Appropriate User Permissions
Verify appropriate user permissions to maintain data security and minimize the risk of unauthorized access. Here are some proven methods to verify user permissions
-
Schedule quarterly reviews of user access roles to verify that each user’s permissions align with their current job responsibilities.
-
Set up role-based access control (RBAC) systems, such as Microsoft Active Directory or Okta, to manage permissions based on user roles and responsibilities.
-
Deploy automated permission management tools like CyberArk or BeyondTrust to monitor and manage user access continuously.
-
Perform monthly audits of permission records using tools like SailPoint or IBM Security to ensure accuracy and compliance with access policies.
Detect Excessive or Unauthorized Access
Here’s how you can effectively detect excessive or unauthorized access
-
Implement continuous monitoring solutions like Splunk or Security Onion to detect unusual access attempts in real time.
-
Schedule weekly reviews of system audit logs using tools such as ELK Stack (Elasticsearch, Logstash, Kibana) to spot anomalies.
-
Define and enforce access thresholds with tools like RSA SecurID to flag and review accounts with excessive privileges.
-
Utilize user behavior analytics platforms like Sumo Logic or Exabeam to identify and analyze abnormal access patterns.
-
Deploy intrusion detection systems (IDS) such as Snort or Suricata to receive alerts on unauthorized access attempts.
Audits Analyze System Logs
Analyzing system logs during regular audits provides detailed records of system events. These logs offer insights into potential vulnerabilities, anomalies, and security issues. Through these regular audits, you can present timely responses to misconfiguration and keep systems secure and compliant.
Examine Logs for Unusual Activities
Unusual patterns in log data can reveal unauthorized access, system failures, or deviations from normal operations. Here’s how to check logs and unusual activities:
- Use Automated Log Analysis Tools. Deploy tools like Graylog or LogRhythm to analyze and flag unusual patterns in your logs automatically.
- Establish Normal Activity Baselines. Create benchmarks of typical system and user activities using platforms like Nagios or SolarWinds to detect deviations.
- Monitor High-Volume Data Transfers. Track and analyze large data transfers with network monitoring tools such as Wireshark or PRTG Network Monitor to prevent unauthorized data exfiltration.
Identify Patterns of Misconfigurations
Many online programs now emphasize hands-on experience that allows students to work with real-world datasets and enhance their problem-solving capabilities. So whether you choose a traditional degree or a cheap online computer science degree, you’ll gain access to critical tools and techniques like log analysis, which are essential for modern cybersecurity. This practical knowledge, combined with theoretical foundations, empowers graduates to detect vulnerabilities. By recognizing these patterns, you can have proactive risk management that safeguards sensitive data and maintains operational continuity effectively.
Here are quick ways to identify misconfiguration patterns:
- Correlate Events from Different Systems. Use SIEM solutions like LogRhythm or ArcSight to link related events from various sources and uncover broader security patterns.
- Regularly Review and Report Findings. Conduct monthly or quarterly reviews of log analysis results and generate reports to inform stakeholders and guide improvements.
- Analyze Error Rates for Patterns. Track and investigate error logs with tools like Nagios or PagerDuty to identify and address recurring issues that may indicate larger problems.
Practice Proactive Security Through Regular Audits
Regular audits help businesses avoid security issues by catching misconfigurations early. By checking system logs, monitoring unusual activities, and spotting patterns of vulnerabilities, companies can boost their security and meet industry standards. This proactive approach reduces the risk of cyberattacks and protects sensitive data.
Follow the tips in this article to adopt regular audits and keep your business ahead of potential threats. Regular audits promote a culture of continuous cybersecurity improvement and allow you to adjust security measures before breaches occur. Try our methods today to ensure long-term resilience and data protection.

Akash Mahajan
Founder & CEO
Akash is the founder of Kloudle, a developer-first cloud security scanner. He’s spent 20+ years in cybersecurity and now builds tools that make securing cloud infra simple, fast, and frustration-free.

Akash Mahajan
Founder & CEO
Akash is the founder of Kloudle, a developer-first cloud security scanner. He’s spent 20+ years in cybersecurity and now builds tools that make securing cloud infra simple, fast, and frustration-free.